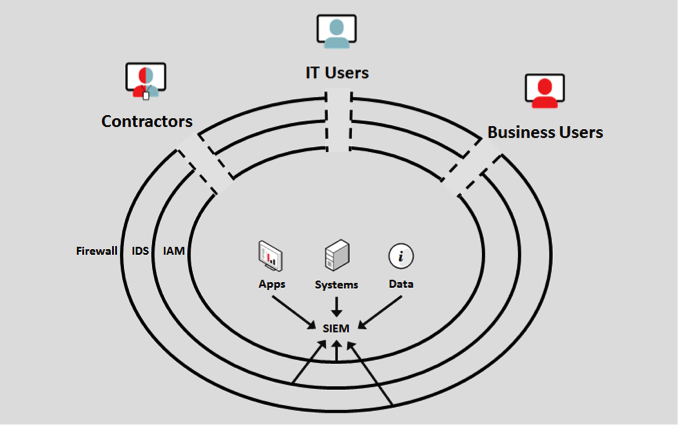
As Dimitri Vlachos discussed in this blog a couple of weeks ago (Your Users: Gateways to Risk), the biggest IT security threat facing companies today is their authorised users. These users – IT administrators, contractors and business users alike – are granted access to the applications, systems and data that are the core digital assets of any business. While organisations have deployed extensive protections around their networks in the form of firewalls, IDS, IAM and the like, these perimeter-defense measures become useless once users are given access to sensitive IT assets.
It is Critical to Monitor User Activity
This leads to the unescapable conclusion that users and their activities should be a top-primary focus of IT security. Only by ensuring full awareness and transparency of all user actions can IT security teams ensure that the assets under their watch are indeed secure.
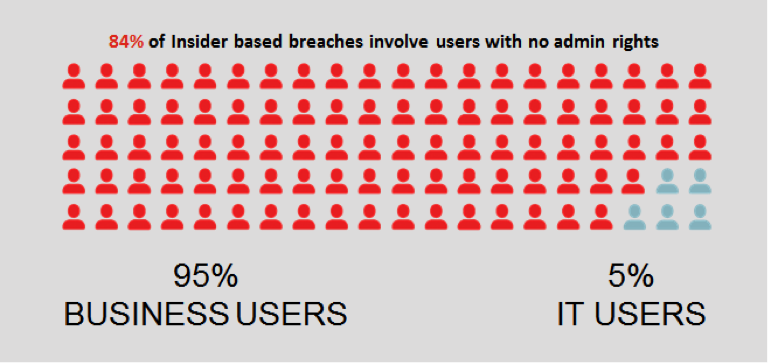
In the past, IT security best practices considered it sufficient to protect and monitor the back-end systems accessible by privileged administrators. However, the truth is that it is the regular business users, not IT administrators, who pose the greatest data breach risk to most organisations. Recent research shows this empirically. For example, the2014 IBM/Ponemon Cost of Data Breach report indicates that 84% of internal data breaches come from regular business user accounts with no administrator privileges. Another example is Verizon’s 2013 Data Breach Investigations Report, which reported that 76% percent of all breaches originate from accounts with access to sensitive data. Whatever the exact numbers, it is obvious that business users pose the greatest security risk to your organisation.
However, this poses a major challenge to security teams: according to Gartner’s 2013 IT Metrics report, there are 20 times more business users than IT users in the average enterprise! The sheer number of business users, their volume of activity and their necessary access to critical/sensitive applications and data combine to make it absolutely critical that their activity is closely monitored.
The Need for an Enterprise-scale Monitoring Solution
The reality of this situation clearly dictates that effective User Activity Monitoring requires an enterprise-scale solution. Simple keyloggers and screen recorders may have provided a degree of security when monitoring a handful of IT administrators, but today’s user-based threats require a much more robust approach.
In order to effectively monitor all users – especially the large number of business users – organisations require a User Activity Monitoring solution with:
- Enterprise-scale system performance – Organisations need the ability to record every screen, keystroke and command generated by tens of thousands of concurrent users per site, and more across multiple sites. This requires advanced technologies and extreme optimisation in the areas of data transmission protocols, screen image compression, database storage and back-end application server performance.
- Enterprise-scale system management – IT needs the ability to effectively manage, support and monitor the health/performance of the User Activity Monitoring mechanisms across thousands of end points, not to mention the application and database servers on the back end.
- Enterprise-scale security automation – IT security teams need the ability to effectively manage and monitor these vast quantities of user activity data to ensure that no security threat or policy violation goes unnoticed.
- Enterprise-scale user privacy assurance – With permissive BYOD policies and the general blurring of the lines between business and personal information, it is imperative that the User Activity Monitoring solution respects user privacy and complies with workplace privacy laws and regulations across the entire enterprise.
Proofpoint Delivers Enterprise-scale User Activity Monitoring
Proofpoint’s leading User Activity Monitoring solution has been developed from the ground up to address the security and business requirements of the largest organisations – which explains why it is used by more than 1,200 enterprises world-wide, including 1 in 5 of the Fortune Global 500.
To learn about how Proofpoint addresses all of the challenges I described above, contact us or try it yourself and experience the value of User Activity Monitoring in your own environment. Get a free 15-day trial of the full-featured Proofpoint ITM. After your trial, purchase the solution or keep Proofpoint ITM Lite, free forever. Try it now!
