As the saying goes, “If you fail to plan, then you plan to fail.” In the last few years, there have been a lot of discussions about how nudging is the missing link to fast-tracking behavioural change. The need to drive faster change is understandable with the ever-evolving threat landscape, which changes the skills that your employees need to acquire to help defend the business.
Your teams are also constantly changing and growing. This raises an important question: Is it possible for end users to keep up with these changes?
We believe so, and we think that nudging is a key part of the solution. In this blog post, we focus on three questions about frameworks that are key to enabling a nudging strategy that drives rapid behavioural change. We also look at a fourth approach that integrates across frameworks, taxonomies and models.
- Adaptive learning framework: Can the same nudge work for all your users?
- Threat taxonomy: How should you incorporate threat intelligence into a nudge?
- The Fogg Behaviour Model: Are nudges alone good enough?
- An integrated model: We explore a business email compromise (BEC) scenario.
1: The adaptive learning framework
Let’s start this discussion with a focus on the information environment. A rigorous cybersecurity education must include content across multiple domains (or topics), where the material is presented in a way that matches the current understanding of the learner.
The adaptive learning framework from Proofpoint breaks down cybersecurity into eight foundational domains, two role-based domains focused on security professionals, and four levels of mastery.
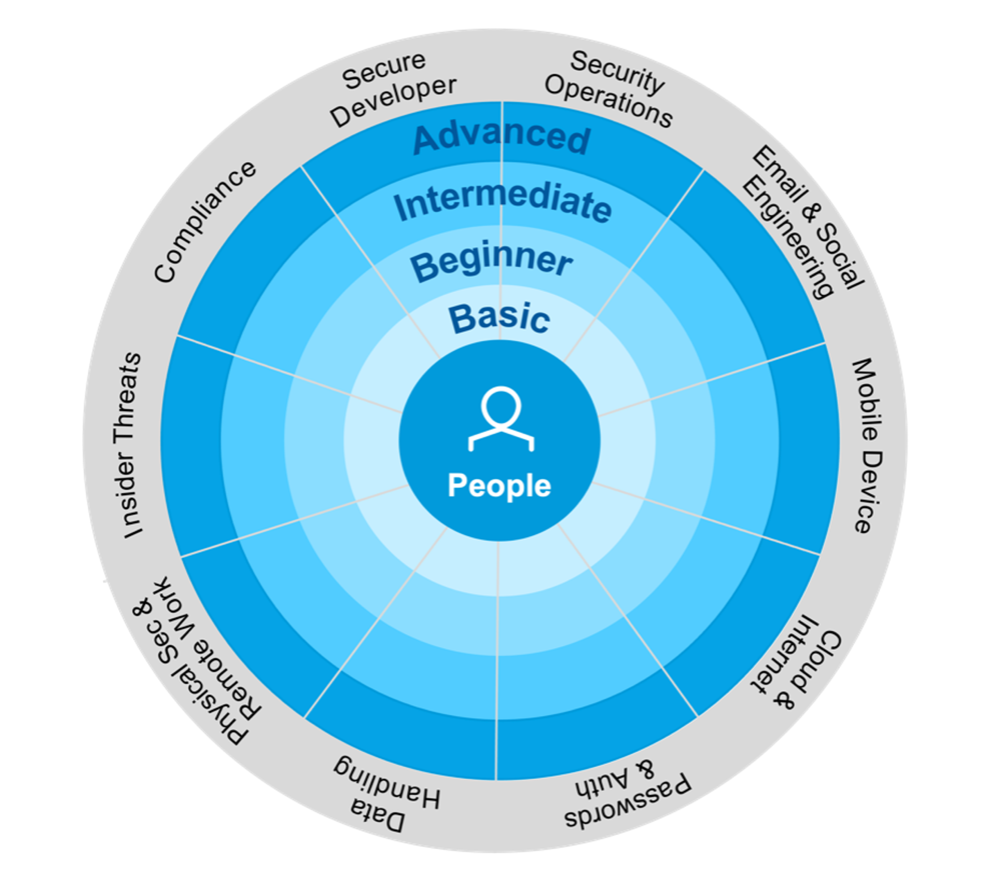
The adaptive learning framework includes 10 domains and four levels of understanding.
The benefit of organising training content this way is twofold. First, it ensures broad coverage across a range of important cybersecurity topics. Second, it takes the learner’s background knowledge into account and moves them to a deeper level of understanding.
2: The threat taxonomy
Nested within the domains of the adaptive learning framework are specific types of attacks. They are separated into two broad categories:
- Identified threats, like BEC, which are either tracked by a Proofpoint product or a third-party integration
- General threats, like tailgating attacks, which are not tracked
These threats comprise our threat taxonomy, which is a classification of threats by nature and source.
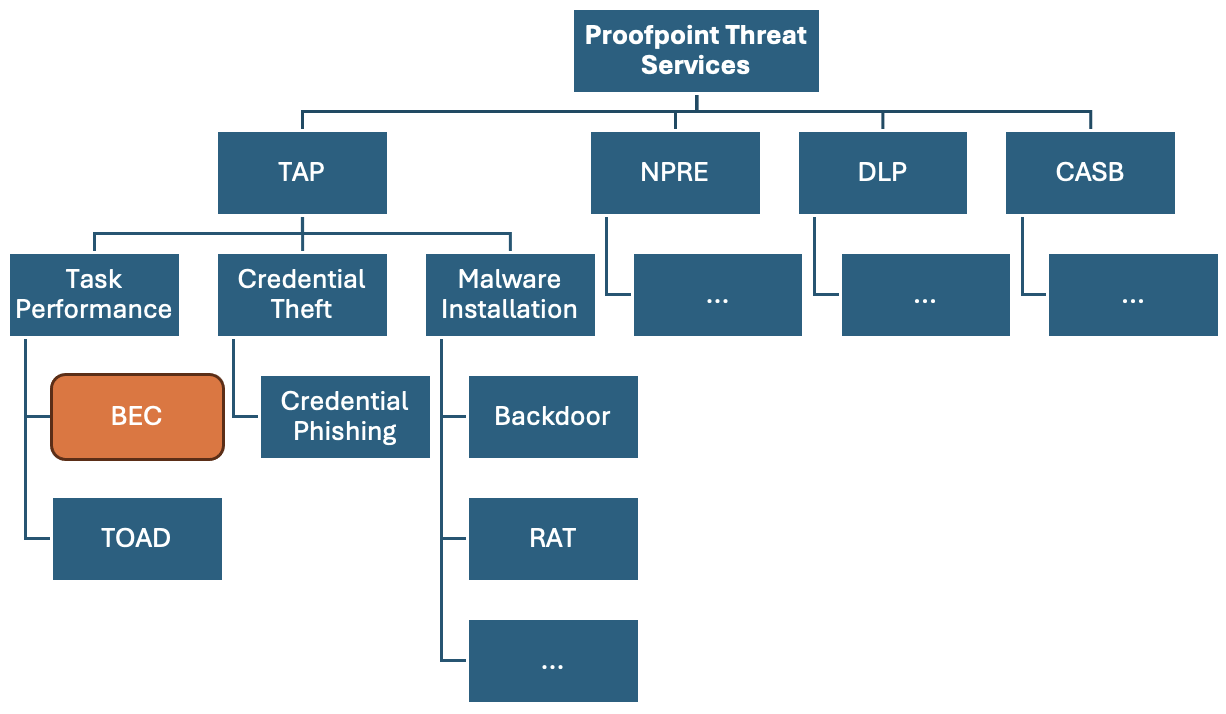
A partial specification of the threat taxonomy from Proofpoint, with a special emphasis on BEC.
Specific threats from the taxonomy are associated with training content as metadata. And some content is associated with one or more threats from the taxonomy. Training content associated with threat-driven metadata varies by levels, domains, roles and themes.

Each terminal node is an identified threat, which can be described by a set of properties (domain, level, role and theme).
By classifying threats systematically, businesses can educate employees effectively on how to recognise and respond to potential risks. Continuous refinement of our taxonomy helps ensure alignment with evolving threat landscapes, empowering companies to mitigate emerging threats proactively.
3: The Fogg Behaviour Model
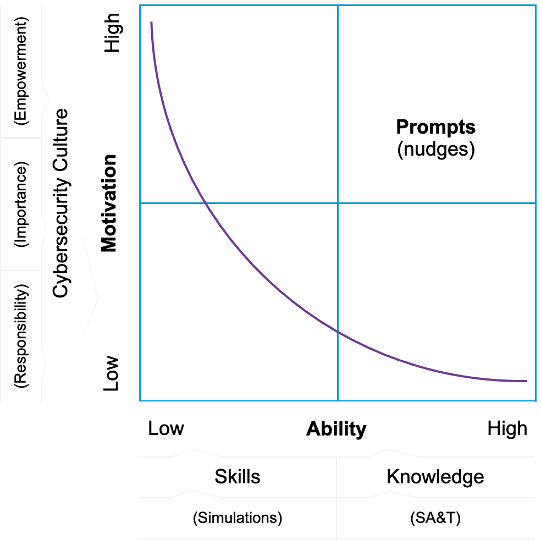
The Fogg Behaviour Model indicates that behaviour is the combination of three factors: motivation, ability and prompts. To understand why an individual took an action (or did not), we need to ask questions in relation to these three factors.
Motivation
- Do they have a high enough level of motivation?
- Do they care?
- Do they see it as their responsibility?
Ability
- Does the individual have the ability to take the desired action?
- Do they have the right skills and knowledge?
Prompts
- Is the environment structured to prompt the individual to engage in the desired behavior?
- Is the environment designed in such a way that it allows for the behaviour to occur, or is it designed to make the intended behaviour difficult or unlikely?
If the desired behaviour did not occur, and we’ve taken the time to ask the above questions, then we must evaluate our options. We need to ask ourselves which levers we have at our disposal to change the likelihood a user will take the right action in the future. We can influence the three factors in the following ways.
1. Motivation. Culture is a motivational factor, and it is why building a strong cybersecurity culture is so important. We see a cybersecurity culture as the overlapping contribution of three main dimensions:
- Responsibility—Is this my job?
- Importance—Do I care?
- Empowerment—Do I know how?
2. Ability. A comprehensive cybersecurity curriculum, as defined by the adaptive learning framework, can influence the ability variable. Ability is the composition of both skills and knowledge.
- If you want to increase skills, you need to provide opportunities to exercise the skill in a safe environment with feedback, like with simulations.
- Increasing knowledge requires the user to pay attention to the material, link it to prior knowledge, and then apply that knowledge to relevant scenarios.
3. Prompts. Nudging provides a methodology to structure the environment in such a way that it increases the likelihood a user will engage in the target or optimal behaviour. As discussed in a recent post on why nudge theory alone won’t save cybersecurity, defaults are the most impactful and efficacious nudges.
4: An integrated model: exploring a BEC scenario
What does it look like when we integrate the threat taxonomy and adaptive learning framework with the Fogg Behaviour Model and nudge theory? See below.
A model that shows three key elements of cybersecurity culture.
The integrated behaviour model above decomposes motivation into three cultural dimensions and ability into two dimensions. And it uses nudge theory as a methodology for building prompts into the environment.
To make this integration concrete, consider the following scenario. Holly is the chief financial officer (CFO) of a major corporation, and she is the target of a BEC campaign. We know this because the Proofpoint Targeted Attack Protection (TAP) service has identified that this threat is being sent to her inbox.
Based on the properties of BEC within the threat taxonomy, targeted education on this threat is pulled from the “Email & Social Engineering” domain. The level for this training topic is categorised as both “Intermediate” and “Advanced.” Holly’s role as the CFO means her training on BEC is further elevated by focusing on finance-related themes.
Drawing on the taxonomic data provided above, we can start asking the three questions from the previous section:
- Does Holly have the right motivation to fend off this attack? If her organisation has administered our Cybersecurity Culture Survey, then we can look at the Responsibility dimension to see if people, on average, see security as their responsibility. That might provide a clue about her personal motivation.
- Second, does Holly have the right knowledge and skills that are directly related to this threat? We know this is an Advanced topic, so we can provide Holly with a short training curriculum to get her up to speed on this identified threat. The content in the Proofpoint Security Awareness platform is tagged with this identified threat, so finding content related to this attack is simple.
- Finally, is Holly’s environment structured in such a way that it makes it easy for her to take the right set of actions? We want to structure Holly’s environment to keep her safe. Since she is being targeted with a BEC attack, we will alert her to this fact by sending a nudge to keep an eye out for specific indicators of a BEC message.
Conclusion
Building a strong cybersecurity culture is an ongoing and incremental process. If you do it well, it will help move your people in the right direction in terms of the motivational dimension described in this post. Your security team won’t need to worry about convincing employees that cybersecurity is their responsibility and that they have the authority to report anything that is suspicious or goes against company policies.
Another ongoing process is to increase users’ ability by enhancing their skills and knowledge through high-quality educational experiences. Skills are exercised using simulations, and knowledge is extended through training videos, Teams and Slack messages, newsletters, and other awareness materials that can be constantly refreshed to keep security top of mind.
Finally, nudge theory provides guidance on how to structure the environment in a way that helps people choose to engage in safe online behaviours.
Next Steps
To further enhance your security awareness initiatives and apply the best practices we've discussed, I invite you to join our upcoming webinar series, "From Targets to Defenders: Building a Culture of Vigilance Through Cybersecurity Awareness." This series, which starts August 14, is designed to provide actionable insights and tools to transform your users into proactive defenders against cyber threats. Don’t miss out on this opportunity to deepen your understanding and improve your security programme—register today!

