The threat landscape moves fast. As new attack methods and social engineering techniques appear, organizations need to maintain security awareness programs that are relevant, agile and focused. Research from Proofpoint for the 2024 State of the Phish report found that most businesses used real-world threat intelligence to shape their security awareness programs in 2023. That makes us happy!
At Proofpoint, we know it is essential to use threats and trends from the wild to teach your employees about attacks they might encounter. It is equally important to ensure that your program isn’t teaching them about security topics that are no longer relevant.
In this article, we discuss four essential best practices to help keep your security awareness and training content both fresh and threat-driven:
- Analyze real threat trends to stay current and relevant
- Use real-world threats to inform your testing and training
- Refresh your training plan so that it’s relevant and accurate
- Ensure that security practitioners stay on top of content changes

An image from our always-fresh (see what we did here?) phishing template that tests brand impersonation.
The human-centric risk of not keeping it fresh
Let’s first talk about what happens when you use outdated threat content to train your employees. The results can create significant human-centric risk for your business because your employees might approach security with unsafe behavior such as:
- Having a false sense of security about their knowledge. People might believe they are well prepared to identify and respond to threats, leading to actions based on incorrect assumptions.
- Not responding effectively to targeted threats. People might make decisions based on incorrect assumptions, increasing the possibility of successful attacks specific to their role or industry.
- Incorrectly reporting a security incident. Outdated training content may give incorrect procedures for reporting and responding to security incidents.
- Being noncompliant with industry regulations. Outdated content might not fit the required compliance training, exposing your company to possible legal and financial penalties.
- Being unengaged in your security culture. If employees perceive security education as outdated or irrelevant, they might see security responsibility as a waste of their time.
Now, let’s talk about our four best practices to help ensure that none of this happens.

An image from the “AI Chatbot Threats” training (play video).
1: Analyze real threat trends to stay current and relevant
Informing your program with threat intelligence is a must. Real-world insights will help your employees understand the scope and impact of the threats they may face. It will also enable your security teams to tailor their training and messaging accordingly.
To use threat intelligence effectively, security awareness practitioners must work collaboratively across their organizations. You want to understand the attack trends that the security practitioners who monitor, analyze and investigate cyber threats see in real time. These practitioners might be your incident response team or your security operations center (SOC) team.
At Proofpoint, we are committed to staying on top of the latest threats and passing this information to customers. The Proofpoint Security Awareness solution is built on insights that we gather from analyzing over 2.6 billion emails daily, monitoring 430+ million domains and tracking hundreds of threat groups to stay ahead of attackers. We do this by collaborating with our in-house Threat Intelligence Services team and using their insights in our integrated threat platform, which ties email monitoring and remediation to human risk detection and education.
Recent insights from real-world trends include:
- Telephone-oriented attack delivery (TOAD). In the 2024 State of the Phish, we reported that TOAD attacks remain prevalent. Proofpoint researchers saw an average of 10 million TOAD messages sent every month in 2023, and over 13 million TOAD attacks at their peak in August 2023.
- QR code phishing. In recent months, our research team has seen an increase in attackers using malicious QR codes as an alternative to links and attachments. This technique is particularly dangerous because it presents a familiar format in an unfamiliar phishing context.
- Generative artificial intelligence (GenAI) scams. We see GenAI methods such as deepfakes and conversational scams on the rise. Attackers can use AI models to create highly convincing message-based attacks, such as personalizing for individual recipients and translating fluently into many languages.

The Proofpoint blog showcases the human risk connection between security awareness and threat intelligence research.
2: Use real-world threats to inform your testing and training
As people become more sophisticated at detecting phishing (and all its variations), attackers find new ways to embed malicious content. That is why it is imperative for security practitioners to transform real-world threats into relevant training and awareness initiatives.
By training employees on how to detect and respond to the latest threats, you can strengthen your overall security defenses. Consider methods such as real-world testing with threat simulation, engaging bite-sized training about trending topics and timely communication to employees about a recent attack. For instance, you could:
- Run QR code phishing simulations for payroll and finance teams to explain the real-world trend of malicious QR codes
- Provide training videos to warehouse employees on the less common but still evergreen malicious USB drop
- Send company-wide emails and distribute screensavers about being vigilant with phone calls, both at home and work, due to AI-generated conversational scams
Proofpoint Security Awareness strengthens the important connection between education and threats by continuously releasing new threat-driven content. This includes Threat Alerts, which are weekly news bulletins focused on a specific attack identified by our threat analysts or collected through open-source research. We also release monthly Attack Spotlights, which cast a wider lens on a particular threat attack that is global in nature and growing in prevalence or expected to trend soon.

An image from the Attack Spotlight video about conversational scams (play video).
3: Refresh your training plan so that it’s relevant and accurate
So far in this post, we have focused on the importance of incorporating relevant threat trends and real-world threats into security training. But adding more content to address emerging threats is only one part of an effective plan. Fresh content and regular updates also keep cybersecurity top of mind with your users and help to promote a proactive security culture.
When refreshing your training plan, get back to the basics and consider these five aspects:
- Who needs to be trained? For example, are help desk employees trained on the latest tactics used to access accounts? Is your finance team aware of how attackers use GenAI to improve messaging in business email compromise (BEC) scams?
- What do you need to train on? For instance, are there industry regulations that certain roles must be trained on? Has there been a security incident or threat trend that people should be aware of? Is the purpose of the training relevant for all or some of your learners?
- Where are you running your initiatives? Are you always running training online or in person? If so, can you tell if that has been effective? What channels do you use to deliver the messaging to your employees? Do your users notice?
- When are you running your initiatives? Do you only run training once a year? If so, you might consider more frequent training to help ensure that you deliver timely information on the latest in threats.
- How are you updating the content? Are your learners watching the same content each year? Does your phishing training require a refresh in advice and guidance? A previous standard was to point out red flags such as poor grammar and spelling. However, emails written with GenAI can now easily avoid these errors.
In Proofpoint Security Awareness, we regularly review, update and remove content as needed. For instance, we recently removed COVID-19 material due to its decreased relevance. We also updated our GDPR content to reflect recent changes.
When we review our content, we pay close attention to diversity, equity and inclusion in the way that topics are shaped and characters are designed. We test our content for accessibility to ensure it can be used by federal, state and local governments.
We look at this refresh as support for our continued development to streamline the work of security practitioners. And that leads us to our final best practice!
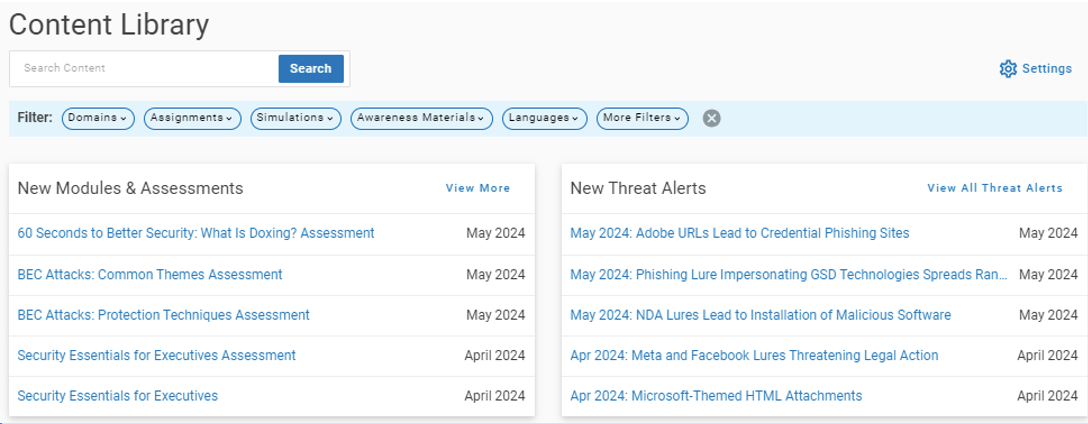
Our Content Library homepage showcases the newest content that is continuously added.
4: Ensure security practitioners stay on top of content changes
We hear you: Security practitioners juggle a lot of manual work for content management. It’s important to minimize the time and resources required to build and grow your awareness program. Often, this means using tools that streamline your content workflow with built-in processes and automation.
In Proofpoint Security Awareness, we continuously streamline our Content Library and improve its features. Recent updates include:
- Integrating a central content repository. Our phishing templates, training modules and awareness material share a single pane of glass, so you can quickly develop and deploy a phishing simulation campaign and follow-up training.
- Expanding the filters for a streamlined experience. Now, you can more easily find, view and access content, like searching across criteria like domains, assignments, simulations, material and languages.
- Providing a go-to place for viewing content updates. The revamped Resource Center has a section dedicated to what’s new in Content & Threat Alerts, such as threats detected by our research team and newly released content pieces.
- Making it easier to see content changes. For example, new visibility buttons show whether Proofpoint content will be retired or will reach end of support (EOS).
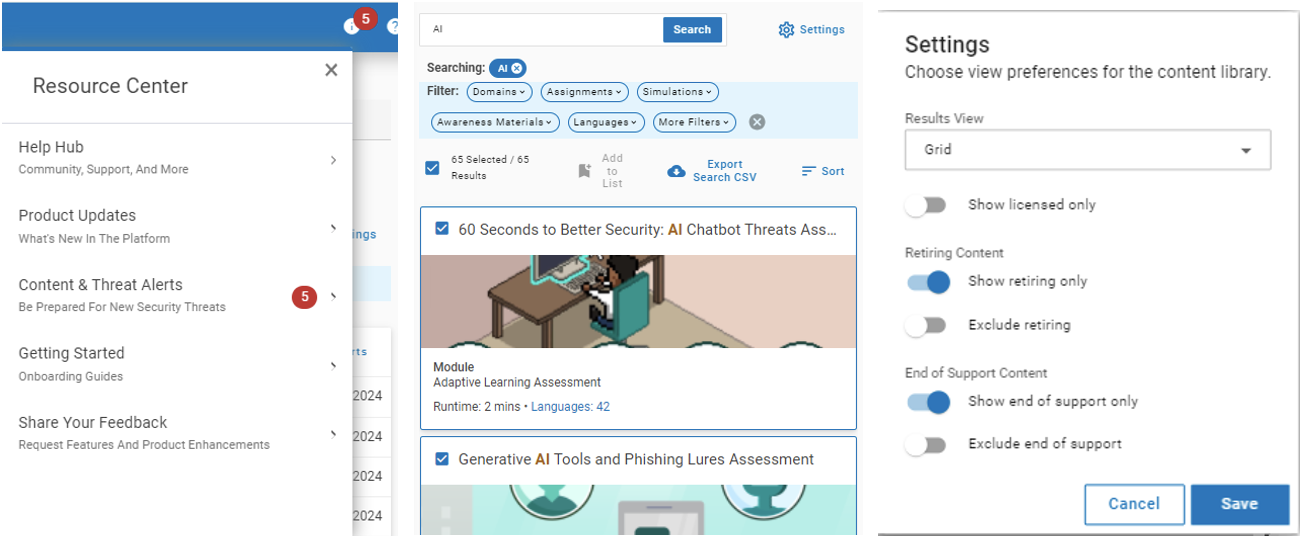
From left to right: Resource Center alerts, content filters and content status buttons.
Minimize your human security risk with Proofpoint
For security education to drive continuous improvement, you must keep your content relevant and reflective of current security threat trends. It is just as important to keep a fresh and flexible approach to how you produce and deliver that content to your users.
Exposure to relevant threat-driven content helps cultivate a security-conscious culture in your organization. In the event of a security incident, employees trained on the latest threats will be better prepared to respond—and do so quickly. Training plans and content can provide the knowledge, skills and procedures for people to handle potential risks and their own vulnerabilities more effectively.
At Proofpoint, our goal is to always help employees view cybersecurity as a shared responsibility and to help security practitioners minimize the human risk to their organization.
You can view samples of our security awareness content here.

