Imagine this: you’re part of a security team that has invested heavily in cybersecurity technology, layered defences and rigorous training for your team. Yet a single click on a phishing email from an unsuspecting employee at your organisation could still open the door to a serious incident. If so, you’re not alone.
Even though you’ve put security measures in place, held training sessions and distributed awareness posters, security incidents keep happening. But why? Because real security isn’t just about what employees know; it’s about how they feel about their responsibility in protecting your organisation. It’s also about how they react when faced with a threat. In cybersecurity, knowledge without behaviour change is incomplete.
Today’s threat landscape is more complex than ever with cybercriminals constantly refining their tactics to exploit human vulnerabilities. However, there is good news: People can become your most effective line of defence. When employees feel empowered and engaged in their role as defenders, they shift from being potential security risks to proactive protectors. How do you get them to that place? You need a systematic, people-first approach to building a security culture.
This is where the Proofpoint DICE framework comes into play. DICE stands for detect, intervene, change behaviour and evaluate. In this blog post, we’ll explore each of these components. We’ll also talk about the psychology behind this framework—and how it empowers organisations to create resilient security cultures. It doesn’t matter if you’re a seasoned security leader or just starting to build a positive security culture as this guide offers actionable insights into achieving long-term behaviour change. Let’s dive in.
What is DICE?
Our experience working with organisations across industries has taught us that effective behaviour change begins when you can detect the people who are most at-risk from threats or those who are most likely to engage in unsafe behaviours and intervene in a timely way. Part of this is tailoring educational experiences to align to each person’s vulnerabilities. You also need to continuously evaluate and improve your programme’s impact.
That’s why DICE makes such a difference. It goes beyond traditional security training, which relies on a one-size-fits-all approach. Instead, it provides employees with continuous, contextually relevant guidance that helps them develop lasting habits.
There are four steps in the Proofpoint DICE framework.
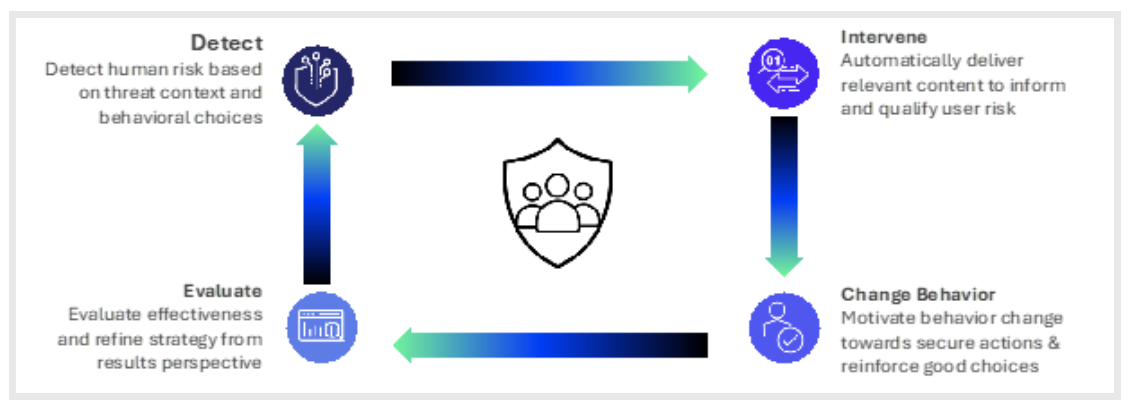
Steps in the Proofpoint DICE framework.
Step 1: Detecting human risk—the heart of effective behaviour change
The first step is detecting human risk, which is based on threat context and behavioural choices. What’s most important here is to identify and understand organisational, departmental and individual risk.
Why detection matters
The journey towards effective security behaviour change starts with a deep understanding of human risk. Who in your organisation is most vulnerable to cyber threats? Which employees continually take risky actions? And why do they do this? Traditional security awareness programmes often lack this level of precision. Instead, they treat everyone as if they face the same risks and need the same training.
During this phase, organisations must quantify and analyse several key risk factors. This helps them build a comprehensive view of each employee’s risk posture. This is crucial because when programmes don’t use targeted insights, they can become unfocused and less impactful. Content that’s one-size-fits-all may not resonate with high-risk users that face unique challenges.
Here’s how to build an effective strategy for detecting risk:
- Analyse behaviour
When you analyse real-world behaviours, you can see that some people are more susceptible to security threats than others. Just consider how activities can reveal whether someone is high risk. If they click on a suspicious link, respond to an unknown sender or share confidential data with an unauthorised recipient, then they are a higher risk than someone who doesn’t. Security teams can use this insight to create targeted education that directly addresses an individual’s risky patterns. This gives them the skills to make safer choices in the future. - Assess knowledge gaps
Regular, targeted assessments provide key insights. Not only do they reveal how well employees understand security principles, but they also help to identify where they lack knowledge. For example, quizzes or short surveys can highlight specific gaps in understanding, like how to avoid social engineering tactics or the best practices for handling data. When security teams know which employees need help with critical areas, they can provide them with foundational awareness on those topics. - Assess vulnerability to real-world threats
Threat simulations—such as QR code scams, credential phishing and SMS phishing—can be used during the assessment process. This helps reveal employees’ vulnerability to real-world attacks. By observing responses, security teams gain a more accurate view of each person’s weaknesses. True-to-life assessments help teams prioritise interventions. Thus, they can focus on the individuals who need more practice identifying specific threats. - Evaluate security beliefs and attitudes
Security awareness isn’t just about knowledge and skills. It’s also about mindset. Cultural assessments and surveys can help security teams gain insight into employees’ attitudes towards cybersecurity and whether they view it as a shared responsibility. For example, questions about how they perceive their role in the organisation’s security can uncover key cultural factors that may increase their vulnerability. It’s crucial to address these beliefs so that a more security-conscious attitude can be fostered.
Why context matters
Context is needed to effectively detect risk. It enables a more tailored and impactful approach to behaviour change. And it ensures that interventions are relevant to the unique challenges each employee faces.
For example, an executive who makes high-stakes decisions might encounter different risks to an entry-level employee who has limited access to sensitive data. This is one reason why the detection process should consider each employee’s job role. It should also take into account their level of access as well as their exposure to external threats.
Step 2: Intervening—turning insight into action
The second step is providing users with relevant content to inform and qualify their risk.
Moving from detection to intervention
Once you’ve identified high-risk employees, the next step is to guide them towards safer behaviours. In this phase, employees should be offered personalised, contextual guidance. This should happen at the point that they behave in a risky way or encounter a threat. Alternatively, at a minimum, they should automatically be enrolled in an educational curriculum that directly relates to what they did that was risky.
Strategies for intervening effectively
To create a more targeted approach to behaviour change, it’s important to track and adaptively place employees into groups, which are based on their roles, behaviours and risk profiles.
Here’s how:
- Provide timely, contextual alerts and guidance
Real-time alerts about emerging threats allow employees to make informed decisions when faced with potential risks. Email Warning Tags are a great example of a timely intervention that provides information about the suspicious nature of an email. This nudge can help guide an individual to not respond or to report the message if they know that they have never interacted with this sender before. These proactive alerts ensure that employees receive the support they need at the moment of risk, preventing incidents before they occur. - Automatically enrol people into tailored learning paths
Security teams can intervene in a targeted way by developing learning paths based on individual behaviour, threat context and risk profiles. For example, high-risk employees who are targeted by a specific threat can be assigned a curriculum that coaches them on how to recognise that threat. Meanwhile, employees who carelessly share confidential data with unauthorised people can get refreshers on data security best practices. This approach ensures employees receive the right amount of guidance in accordance with their unique needs. It also increases the chances that their habits will change.
Step 3: Changing behaviour—using continuous, real-world training
In this step, users are motivated to change their behaviour so that it’s more secure. Good choices are reinforced.
The science of behaviour change
Behaviour change doesn’t happen overnight. Rather, it’s the result of consistent, deliberate practice that is informed by key principles from behavioural science. This phase combines proven learning techniques to embed secure practices into employees’ everyday actions. This, in turn, helps them form lasting habits.
Key components of continuous education
- Spaced practice
Spaced practice is a study technique that involves learning over time. These are shorter, more frequent sessions so that information isn’t crammed in all at once. This aligns well with micro-learning and nano courses. It gives employees the opportunity to revisit security concepts periodically, allowing them to absorb information in manageable doses so that they can retain it over the long term. This approach builds a strong foundation for behaviour change, making secure actions more natural and habitual. - The testing effect
The testing effect is a learning principle where students are asked to actively retrieve what they’ve learned by taking quizzes, tests or other assessments. This improves their long-term memory. In the context of security education, this aligns perfectly with phishing simulations and regular assessments. As employees actively engage with realistic phishing exercises and knowledge quizzes, they recall security best practices. These repeated experiences help to solidify their ability. As a result, secure behaviours become more instinctive when they’re faced with real-world attacks. - The doer effect
The doer effect says that students are more likely to remember something when they apply it to real life. They learn by doing, not passively absorbing information. When it comes to security education, this principle is applied through interactive training modules and gamified learning experiences. As employees participate in hands-on activities—such as simulations, role-playing scenarios and competitive challenges—they gain practical experience. Gamified elements, like point systems, achievements and leaderboards, also enhance motivation. This makes learning both memorable and enjoyable.
Creating lasting change through active learning
These principles ensure that training is designed in a way that’s not only meant to educate but also create lasting behaviour change. Together, they create a culture of active learning where secure behaviours become second nature. Through frequent, engaging and realistic training experiences, employees gain the confidence and reflexes they need to respond securely to threats.
Step 4: Evaluating effectiveness—measuring what matters
In this step, you evaluate the effectiveness of your programme. Then, you refine your strategy based on your results.
Why evaluation matters
Meaningful data is essential to understand the impact of a behaviour change programme. This phase must provide metrics that assess behaviour change efforts. And it should demonstrate to stakeholders that the programme has real value.
Key metrics for measuring success
- Real-world behaviour analysis
Both positive and negative real-world behaviours provide essential insights into a programme’s impact on human risk. When organisations track these behaviours, they can understand the real-world impact of their security awareness efforts. This approach enables a proactive, data-driven strategy to human risk management.- Positive behaviours—like consistently reporting suspicious emails and avoiding risky actions—show that an employee’s risk level has been reduced. What’s more, they show that secure behaviours are becoming ingrained and that their individual risk profile is lower. This means that the organisation’s overall risk is reduced too.
- Negative behaviours—like ignoring security guidelines even after a course is complete—show that the risk level is increasing. Security teams can analyse these patterns and adjust education to address specific vulnerabilities. Employees who continue to behave in risky ways should be a priority. And when they do show any positive actions, their behaviours should be reinforced.
- Suspicious email reporting metrics
It’s essential to track user reporting rates and reporting accuracy. These metrics help security teams evaluate how well a programme is helping to change user behaviour. They provide a complete picture of behaviour change. And they show that training is strengthening an organisation’s human defence layer.- Reporting rate measures how often employees report suspected phishing or suspicious activity. It indicates how vigilant and proactive they are when it comes to defending the organisation.
- Reporting accuracy measures how well employees correctly identify actual threats versus false positives. It shows their skill is growing when it comes to identifying genuine risks.
- Benchmarking and industry comparisons
When organisations measure how well their security culture performs against industry standards, they can better assess it within a broader context. This is called benchmarking. And it provides a valuable perspective on programme effectiveness. It helps organisations understand where they stand relative to their peers.
Conclusion: Building a resilient security culture
Changing security behaviour is a complex and ongoing process. People must be more than just aware of security practices—they must also be engaged. To get there, security education must be both relevant and continuously measured.
The DICE framework helps organisations transform their education. It does this by providing a structured, effective way to turn security awareness into something that creates lasting behaviour change.
By following the framework, organisations can create a security culture that isn’t just about being aware but about being resilient. Employees become active partners in defending against threats. This, in turn, actively reduces an organisation’s risk and enhances its security posture.
How Proofpoint can help
Proofpoint is committed to helping you build a proactive, behaviour-based security programme. Through the DICE framework and tools like ZenGuide, People Risk Explorer, Adaptive Groups and the Adaptive Learning Framework, we provide everything you need to guide your team towards lasting security behaviour change.
If you’re ready to make the shift from awareness to action, connect with us. Together, we can work to reduce your human risk and create a culture of resilience.

