What happened
Beginning April 24, 2024 and continuing daily for about a week, Proofpoint observed high-volume campaigns with millions of messages facilitated by the Phorpiex botnet and delivering LockBit Black ransomware. This is the first time Proofpoint researchers have observed samples of LockBit Black ransomware (aka LockBit 3.0) being delivered via Phorpiex in such high volumes. The LockBit Black sample from this campaign was likely built from the LockBit builder that was leaked during the summer of 2023.
Messages were from “Jenny Green” with the email address of Jenny@gsd[.]com. The emails contained an attached ZIP file with an executable (.exe). This executable was observed downloading the LockBit Black payload from Phorpiex botnet infrastructure.
From: “Jenny Green” jenny@gsd[.]com
Subject: Your Document
Attachment: Document.zip
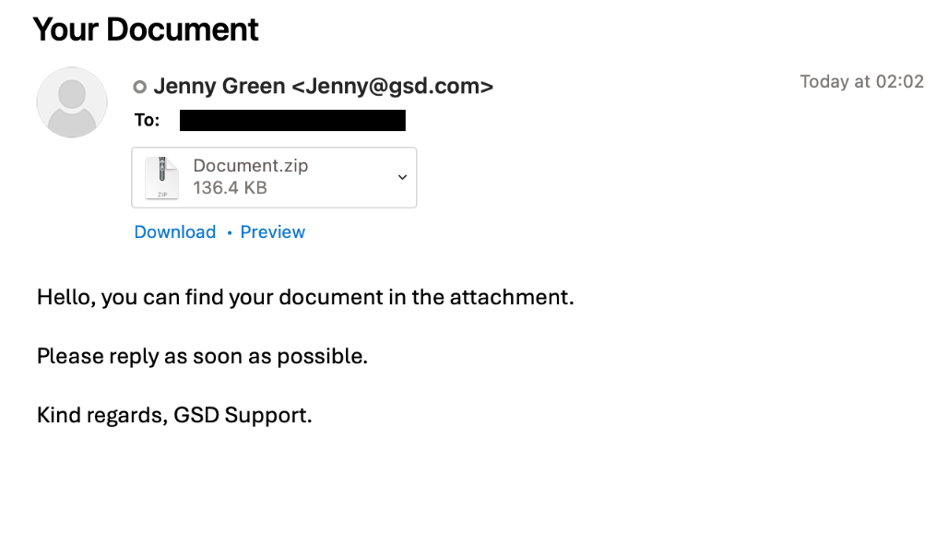
Example message from ”Jenny Green.”
The emails targeted organizations in multiple verticals across the globe and appeared to be opportunistic versus specifically targeted. While the attack chain for this campaign was not necessarily complex in comparison to what has been observed on the cybercrime landscape so far in 2024, the high-volume nature of the messages and use of ransomware as a first-stage payload is notable.
The attack chain requires user interaction and starts when an end user executes the compressed executable in the attached ZIP file. The .exe binary will initiate a network callout to Phorpiex botnet infrastructure. If successful, the LockBit Black sample is downloaded and detonated on the end user’s system where it exhibits data theft behavior and seizes the system, encrypting files and terminating services. In an earlier campaign, the ransomware was directly executed, and no network activity was observed, preventing network detections or blocks.
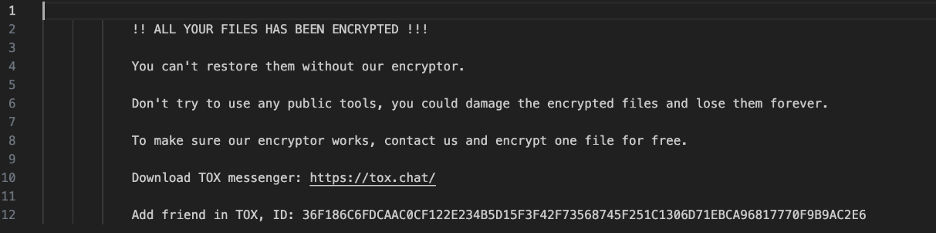
LockBit Black sample ransom note.
Attribution
Proofpoint Threat Research has not attributed this campaign to a known threat actor. Phorpiex is a basic botnet designed to deliver malware via high-volume email campaigns. It operates as a Malware-as-a-Service and has garnered a large portfolio of threat actor customers over more than a decade of operation (earlier versions were first observed on the threat landscape circa 2011). Since 2018, the botnet has been observed conducting data exfiltration and ransomware delivery activities. Despite disruption efforts throughout the years, the botnet persists.
Proofpoint has observed a cluster of activity using the same “Jenny Green” alias with lures related to “Your Document” delivering Phorpiex malware in email campaigns since at least January 2023.
LockBit Black (aka LockBit 3.0) is a version of LockBit ransomware that was officially released with upgraded capabilities by the ransomware affiliates in June 2022. In September 2022, the confidential ransomware builder was leaked via Twitter. At the time, multiple parties claimed attribution, but LockBit affiliates claimed the builder was leaked by a disgruntled developer. The leak allows anyone to adopt the configuration for customized versions.
Why it matters
Ransomware as a first-stage payload attached to email threat campaigns is not something Proofpoint has observed in high volumes since before 2020, so the observation of a LockBit Black sample in email threat data on this global scale is highly unusual. Additionally, this campaign has been particularly notable due to the high volume of messages in the millions per day, volumes not commonly observed on the landscape. The number of messages and cadence associated with recently observed LockBit Black campaigns are at a volume not seen in malspam since Emotet campaigns.
The LockBit Black builder has provided threat actors with access to proprietary and sophisticated ransomware. The combination of this with the longstanding Phorpiex botnet amplifies the scale of such threat campaigns and increases chances of successful ransomware attacks. This campaign is another good example of how the threat landscape continues to change, underscored by recurring and significant shifts and pivots in the tactics, techniques, and procedures (TTPs) used by threat actors.
Example Emerging Threat (ET) signatures
2022050 ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M1
2022051 ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M2
2016141 ET INFO Executable Download from dotted-quad Host
2853272 ETPRO MALWARE Win32/Phorpiex Bot Executable Payload Inbound
2848295 ETPRO MALWARE Win32/Phorpiex.V CnC Activity M3
Sample indicators of compromise
|
Indicator |
Description |
First Seen |
|
Jenny Green <Jenny@gsd[.]com> |
Sender address |
2023-2024 |
|
Jenny Brown <JennyBrown3422@gmail[.]com> |
Sender address |
2024-04- 29 |
|
Photo of you??? |
Subject |
2024-04-29 |
|
Your Document |
Subject |
2023- 2024 |
|
01cd4320fa28bc47325ccbbce573ed5c5356008ab0dd1f450017e042cb631239 |
SHA256 |
2024-04-29 |
|
7bf7dfc7534aec7b5ca71d147205d2b8a3ce113e5254bb342d9f9b69828cf8ee |
SHA256 |
2024-04-29 |
|
ddbc4908272a1d0f339b58627a6795a7daff257470741474cc9203b9a9a56cd6 |
SHA256 |
2024-04-29 |
|
6de82310a1fa8ad70d37304df3002d25552db7c2e077331bf468dc32b01ac133 |
SHA256 |
2024-04-24 |
|
86e17aa882c690ede284f3e445439dfe589d8f36e31cbc09d102305499d5c498 |
SHA256 |
2024-04-24 |
|
13916d6b1fddb42f3146b641d37f3a69b491f183146e310aa972dd469e3417bf |
SHA256 |
2024-04-24 |
|
062683257386c9e41a1cd1493f029d817445c37f7c65386d54122fa466419ce1 |
SHA256 |
2024-04-25 |
|
1ecea8b0bc92378bf2bdd1c14ae1628c573569419b91cc34504d2c3f8bb9f8b2 |
SHA256 |
2024-04-25 |
|
dec445c2434579d456ac0ae1468a60f1bad9f5de6c72b88e52c28f88e6a4f6d0 |
SHA256 |
2024-04-25 |
|
263a597dc2155f65423edcee57ac56eb7229bdf56109915f7cb52c8120d03efb |
SHA256 |
2024-04-29 |
|
a18a6bacc0d8b1dd4544cdf1e178a98a36b575b5be8b307c27c65455b1307616 |
SHA256 |
2024-04-29 |
|
0cc54ffd005b4d3d048e72f6d66bcc1ac5a7a511ab9ecf59dc1d2ece72c69e85 |
SHA256 |
2024-04-29 |
|
f2198deecddd5ae56620b594b6b20bf8a20f9c983d4c60144bc6007a53087ce4 |
SHA256 |
2024-04-26 |
|
874d3f892c299a623746d6b0669298375af4bd0ea02f52ac424c579e57ab48fd |
SHA256 |
2024-04-26 |
|
185.215.113[.]66 |
Payload Delivery IP |
2023-2024 |
|
193.233.132[.]177 |
Payload Delivery IP |
2024-04-29 |

