July marked the start of tax season in Australia and cybercriminals are following the money by actively targeting taxpayers through sophisticated phishing emails and fraudulent websites designed to look legitimate. Our research has shown that threat actors target individuals within companies that will result in the highest payout, and these tax-themed phishing emails are the latest example of why organisations need to take a people-centric approach to their security strategy. Tax season presents a unique opportunity for threat actors to target individuals and organisations for financial theft and fraud using both email and social engineering.
Each year we observe an annual increase in tax-themed email lures during tax season that aim to distribute a variety of malware payloads, in addition to the perennially popular credential phishing uses. The phishing pages and lures themselves are often highly convincing, look authentic, and make use of stolen branding to fool even savvy recipients. From a global perspective, these tax lures are consistent with the phishing content sent to the U.S. and UK as well.
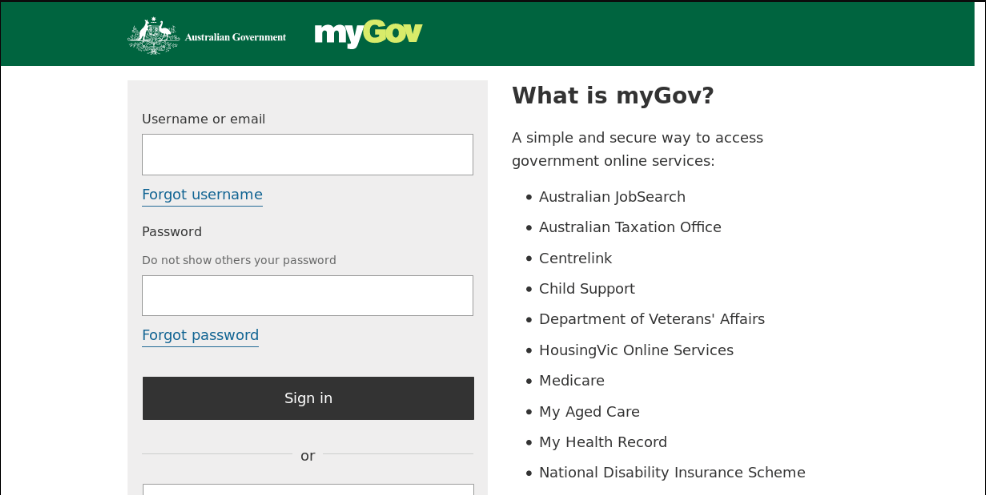
To help security teams and citizens alike, below are examples of a recent Australian Taxation Office (ATO) phishing email and a fraudulent myGov landing page, along with security tips to keep in mind as Australians file their taxes between now and October.
Attack Details: 2019 ATO Phishing Email Example and Fraudulent myGov Landing Page
The email phishing example below, and subsequent fraudulent website, are designed to trick Australians into entering their online banking login credentials into a site that mimics the appearance of myGov. As demonstrated in the example below, the display name in the ‘from’ field of this phishing email doesn’t represent the email address that is actually sending the message. The phishing emails we’ve observed try to convince users to click on HTML attachments with URLs linking to the fraudulent tax institution account login page; other examples also include a direct URL linking to the phishing page.
Once the malicious URL is clicked and the user enters their credentials in the fraudulent login page, three things could occur. They may be sent to an external site controlled by the attacker, their credentials may be saved in a text file on the same server for later retrieval, or their information could be emailed to an attacker-controlled email address. Oftentimes the user is redirected to the real tax institution login page after entering their credentials; to the victim, it will simply appear that their login failed and they will attempt to login again. Alternatively, a PDF or other document may be opened and displayed to the end user in order to avoid arousing the victim’s suspicions.
Fraudulent ATO Phishing Email Example:

Fraudulent myGov Landing Page Examples:




How to Stay Safe This Tax Season
It’s important to remember that any Australian of age is at risk of being targeted with a tax-related scam and that the ATO will never ask for your tax file number or financial details over social media, text message, or email. Be extremely careful with any unsolicited email that claims to be from the ATO. Taxpayers can view their tax account information online at ato.gov.au or my.gov.au and confirm any money owed there. If you do need to speak with the ATO via phone, you can call them using the phone number listed on the official ATO website: 1800 008 540. If someone calls claiming to be from the ATO, do not provide any information; promptly hang up.
For more information on how to stay safe this tax season, please visit https://www.ato.gov.au/General/Online-services/Online-security/. And for more information on developing a people-centric security strategy, please visit https://www.proofpoint.com/au/resources/webinars/how-build-your-people-centric-cybersecurity-strategy.

