The traditional network security model was designed to connect workers at headquarters or a branch office to the resources they needed in data centers. At that time, there were relatively few remote workers and they connected back into their home network using an operationally complex VPN.
Today, most employees work remotely at least one day a week and virtually all organizations also make use of multiple public cloud services. Those factors combined with the security vulnerabilities associated with VPNs means that the traditional model is no longer effective.
The End of Trust
A critical defect in the use of VPNs for remote access is that once users are authenticated they are considered trusted and are granted broad access. As a result, once a hacker penetrates an organization’s firewalls he/she can move through the network with little if any resistance.
Back in 2010 John Kindervag created the zero trust security model. In a recent article he discussed how trust is a human emotion and added that "It has no purpose in digital systems, such as networks. There is no use for 'trust' in these systems, except to be used by malicious actors, who exploit ‘trust’ for their own nefarious gain. The only thing that can happen to trust in a digital system is for it be exploited, and the only outcome for trust is some type of betrayal."
The zero trust security model is based on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify everything trying to connect to its systems before granting access. In a zero trust model users have a unique, fixed identity and one-to-one connections between a user and the resources that he/she needs to access. A key advantage of this model is that a compromise to one asset does not compromise the entire company.
Taking Zero-Trust to the Next Level
A weakness in the original zero trust security model was that the connections that were established between a user and network resources could last for an extended period of time. This potential attack vector can be mitigated by an expanded model in which the right of a user to access resources is continuously verified – ideally at the packet level.
In addition to continuous verification, an effective zero trust model must support next generation access. As explained by Chase Cunningham in a recent Forrester blog, next generation access encompasses a range of functionality including single sign-on, multifactor authentication and correlation between access and users; i.e., who is doing what, where, and why?
Moving to a Zero Trust Network-as-a-Service (NaaS)
The best way to address the systemic flaws in the traditional network security model is to replace that site-centric approach with an identity-based approach that includes both dynamic, per-user network segmentation and continuous authentication. A cloud-native NaaS is built around a zero-trust architecture in which each user has a unique, fixed identity and is bound by a software-defined perimeter (SDP). The SDP framework enables one-to-one network connections that are dynamically created on demand between the user and the specific resources that he/she needs to access – everything else on the NaaS is invisible to the user. No access is possible unless it is explicitly granted and any access that is granted is continually verified at the packet level.
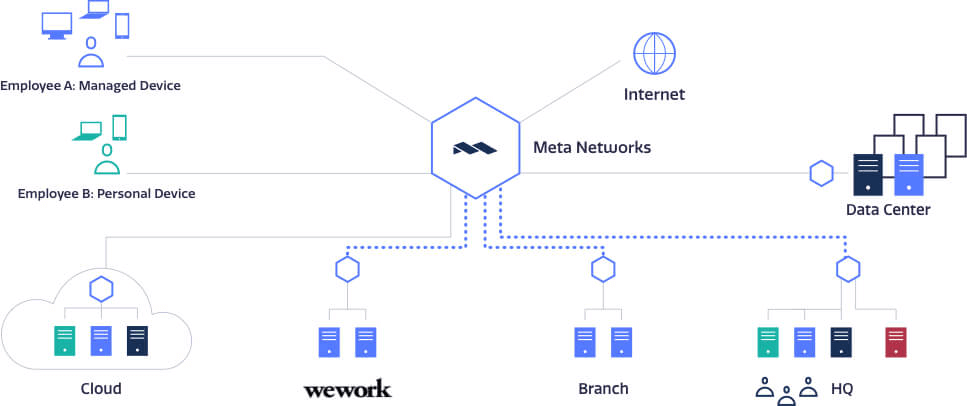
Once data centers, clouds, and branches are onboarded to the NaaS, policies define what is visible to authenticated users.
Turning Theory into Practice
A zero trust security model is critical in the age of digital transformation. In contrast to the old “trust but verify” approach, the new way of thinking is based on never trust, continually verify, as well as minimizing access to a company’s resources with dynamic micro segmentation.
Given the growth in the sophistication and impact of security attacks, IT organizations must move quickly to adopt the new security model. Many will find that the optimum place to start is where the current security model has the greatest weaknesses – remote access – and look into replacing VPNs with a zero-trust Software-Defined Perimeter.
To learn more about Proofpoint Meta and how it can help your organization enable Zero Trust click here.

