It comes as no surprise that attackers are taking advantage of what is going on in the world today and preying on human vulnerability. Proofpoint research has shown cybercriminals are using coronavirus themes for nearly all types of attacks, including (but not limited to) business email compromise (BEC), credential phishing, malware, and spam email campaigns.
The targeting of these attacks has ranged from extremely broad to narrowly focused and campaign volumes have fluctuated between small and large. Attribution includes both well-known attackers, including TA505 and TA542 (the actors behind Emotet and Ostap respectively) and unknown. You can read more on our Threat Insight blog post here.
In this current environment, security practitioners are getting asked if employees are being targeted by COVID-19 attacks and what organizations can do to protect against them. Proofpoint Targeted Attack Protection (TAP) not only helps protect and defend against these types of attacks, but also exposes the most vulnerable targets.
Below is a simple three-step process to get visibility into these specific COVID-19 attacks that are targeting their people:
1. Log-in to the TAP Dashboard and go to the search page 2. Type “covid” in the search bar and click the magnifying glass
2. Type “covid” in the search bar and click the magnifying glass
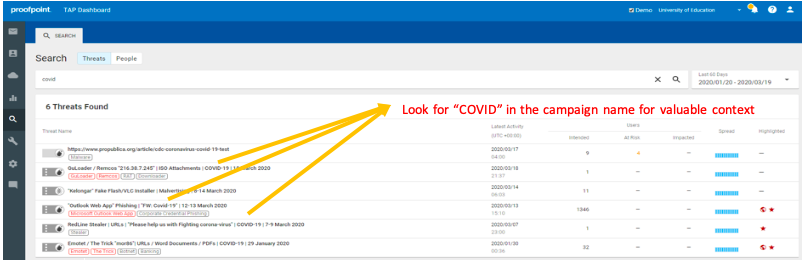
Results will match either having "covid" in the campaign name or "covid" in the URL. A campaign with “covid” in the campaign name is going to be preferable as it will have significantly more context (e.g. lures, screenshots, descriptions) that are all related to COVID.
Note that if the campaign does not have "covid" in the title but showed up in the search results, it means that the campaign matched because the URL that was included in the campaign scope had 'covid' in it.
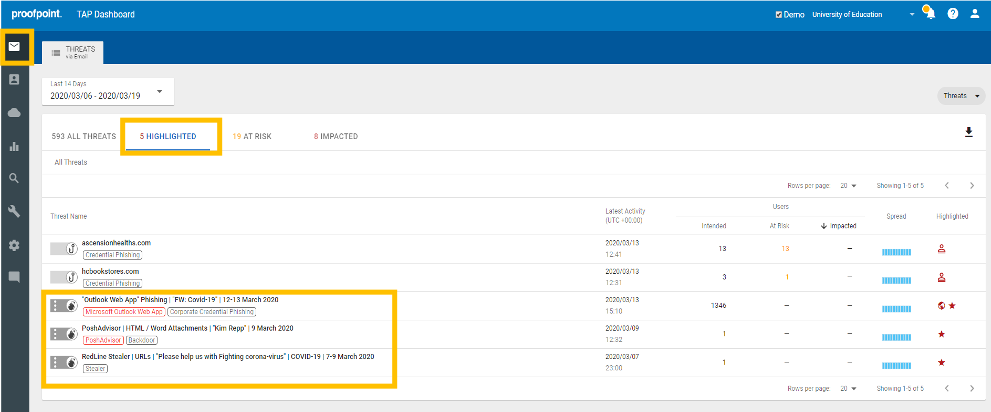
You can also find COVID-19 lures that have been marked as interesting at this point in time under the Highlighted tab when you first log-in to the TAP Dashboard. This could be another way to look through the campaigns associated with COVID-19. This is depicted in the screen shot above.
3. Pick a campaign
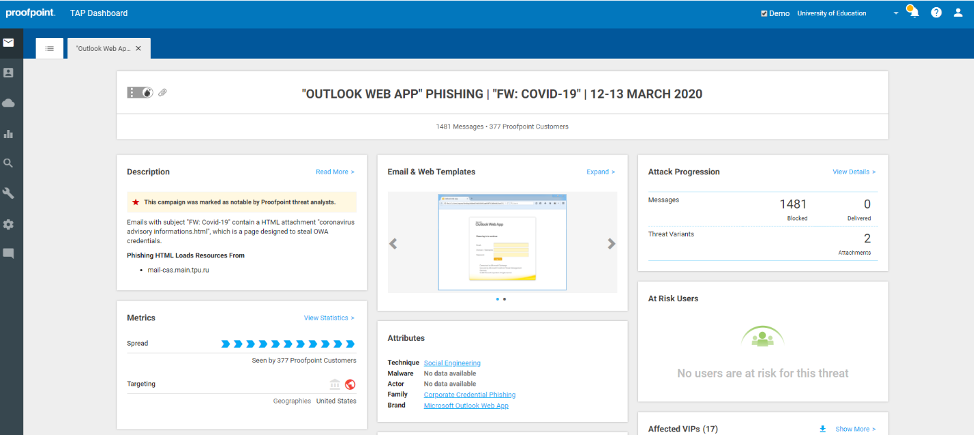
In this particular campaign, you can see that almost 1,500 messages were blocked that targeted the organization. The threat actor served up an Outlook Web App page for victims to put in their credentials. The target geography for this campaign was in the United States.
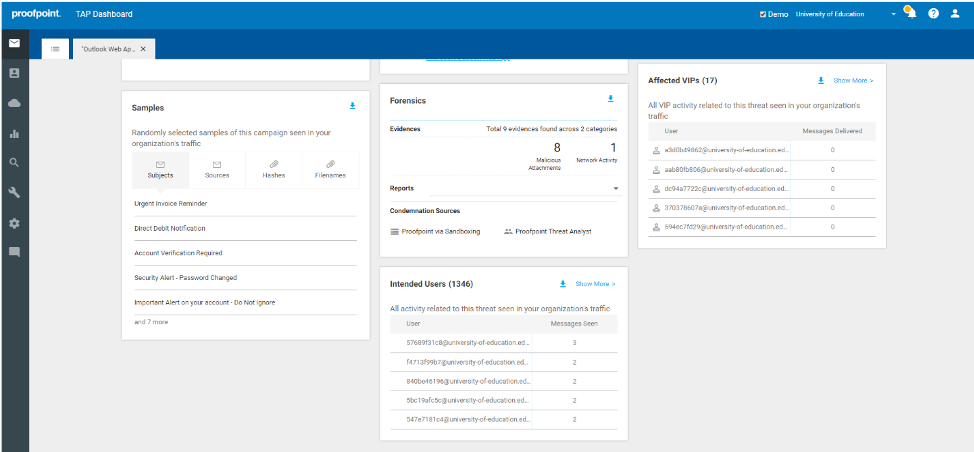 You can also see detailed forensics associated with this campaign. A very important finding is the targets as well. You can see all of the intended users and VIPs in the organization that have been targeted by this specific campaign.
You can also see detailed forensics associated with this campaign. A very important finding is the targets as well. You can see all of the intended users and VIPs in the organization that have been targeted by this specific campaign.
It is very easy to navigate through the TAP Dashboard and get visibility into the latest threats that are targeting your people. After getting this visibility, a best practice is to enroll these targeted users into a Security Awareness Training to raise their alertness to the fact they are being targeted by these types of threats.

