[Update, September 15, 2016 – This post was updated to reflect recent, ongoing research on Pokemon GO and related apps]
Proofpoint analysts were among the first to identify mobile malware associated with the wildly popular app Pokémon GO. Just days after its initial, early-July release in Australia and New Zealand, we found a cloned version of the app with a malicious remote access tool (RAT) called DroidJack built in. While this particular version was never detected in the wild, it nonetheless demonstrated the ease with which cyber attackers could capitalise on demand for the app and use it to distribute malware.
At the time, other researchers identified malware like a Pokémon GO lockscreen and scareware under the guise of guides and cheats for the game.
Now, six weeks after its initial release, Pokémon GO remains a wildly popular app that continues to make headlines. Whether it was early reports of complete access to users' Google accounts or stories about legions of fans walking the streets -- and sometimes into them -- in search of rare virtual creatures, the headlines didn't stop Niantic from making $200 million during the first month the game was on the market. And with Apple’s announcement today that Pokémon GO will be coming to the new Apple Watch, interest in the game will continue to grow, as will real-time, continuous engagement.
This kind of popularity has ensured that Pokémon GO found its way onto devices connected to corporate networks. 4.5% of devices across the organisations we surveyed had Pokémon GO installed, including a small percentage of them (4%) running early versions of the game that had no patch for the Google permissions issues.
This isn't necessarily a problem in itself - rather, it is indicative of the game's popularity. More problematic, however, is the prevalence of potentially risky apps related to Pokémon GO on corporate networks. Niantic has warned about the use of add-on map apps that scrape their servers for data. In addition, three malicious apps related to Pokémon GO have already been detected in US app stores, and have been distributed to users. These and other simply "risky" apps - those with excessive permissions or leaky data handling but that aren't necessarily malicious - are following users into the workplace.
Apps, though, aren't the only area of concern for popular phenomena like Pokémon GO. As we saw with the Rio Olympics, social media is fertile ground for scams and attacks when public interest in a topic is high, and Pokémon GO is no different. Proofpoint researchers identified 543 social media accounts related to Pokémon GO across Facebook, Twitter, and Tumblr. Of these, 167 - over 30% - were fraudulent.
- 44 accounts had links to download files, many purporting to be Pokémon GO, game guides, etc.
- 79 were imposter accounts.
- 21 accounts promised “free giveaways”.
Accounts with downloads affected both mobile and desktop platforms and delivered adware, malware, and software other than the one advertised.
For example, the fraudulent Facebook page below links users to a download of the Downware Trojan:
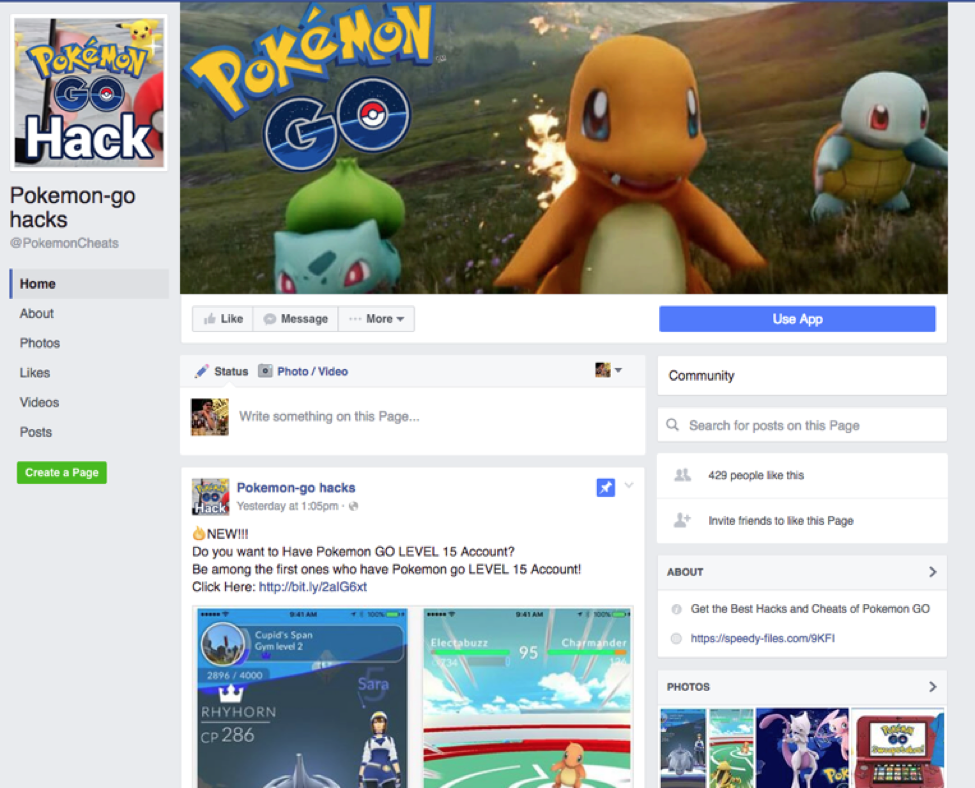
Figure 1: Fraudulent Pokémon GO page leading to malware
Mobile and social threats combine in another example in which a fraudulent Facebook page leads users to Android malware:

Figure 2: Fraudulent Pokémon GO page that links to Android malware
It’s important to note that while we have seen at least three malicious versions of Pokémon GO, social media is also driving users to install Android APKs, which happen to be malware, as shown in Figure 2. Power ups, guides, and walkthroughs are all common and easy ways to draw users’ attention as these are compelling tools that help players in the game.
Cyber criminals are bringing a full suite of attacks to the table with Pokémon GO: from compromised apps to fraudulent social media sites and phishing social posts that lead to more mobile malware… the list goes on. Customers of Proofpoint Mobile Defense can protect against Pokémon GO malware from both app stores and social networks with one of the industry's largest mobile app analysis and mobile threat intelligence databases, capable of ferreting out malicious and risky mobile apps.
At the same time, the 167 fraudulent social media accounts are the tip of the iceberg in terms of the risks, scams, and malware that face users as they search for tips, level ups, and other ways to gain advantage in the game. These accounts exist to make a statement or extract money from users who are not cautious enough to avoid them or lack security tools to protect themselves from social media threats and risks. Proofpoint provides market-leading social media security solutions that identify and block many of those threats posed to Pokémon GO players as well as protect the brands of the publishers involved.
The popularity of Pokémon GO has created many opportunities across social and mobile ecosystems for threat actors to target players and fans of the application. While even the developers of the app initially struggled with excessive permissions on Google accounts, the real challenges now are for organisations potentially exposed to malware and risky apps widely distributed through social and mobile channels. Individuals as well must exercise caution as they interact with wider communities related to Pokémon GO as the potential threats peripherally associated with this app are diverse and numerous.
More generally, though, Pokémon GO serves as a ready example of the ways in which cyber attackers will use popular phenomena to go after new targets. As the popularity and novelty of Pokémon GO eventually wanes, attackers will be looking for the "next big thing," exploiting attention on the holidays, presidential elections, major sporting events, and more.
[Update]
Since we published this post, we have continued to monitor threats associated with Pokemon GO, particularly those with potential enterprise impact. Most recently, we have discovered a modified version of Pokemon GO being distributed through third-party app stores that lures users with free cheats. Because it uses a carefully engineered, fraudulent enterprise certificate, it can be loaded on non-jailbroken iPhones. While the potential impact of this modified app remains to be seen, it has already been downloaded over 12 million times from one particular app store that has full English language support, despite being hosted in Vietnam (see the screenshot below). Several others stores are also distributing the app which should be considered mobile malware and deleted immediately. It is also worth noting that some of these stores may also install their own apps, further increasing the risks associated with installation. Again, the presence of an enterprise certificate exploit of this nature underscores the need for comprehensive mobile app analysis.


