STOP EMAIL FRAUD AND IMPOSTOR EMAIL THREATS
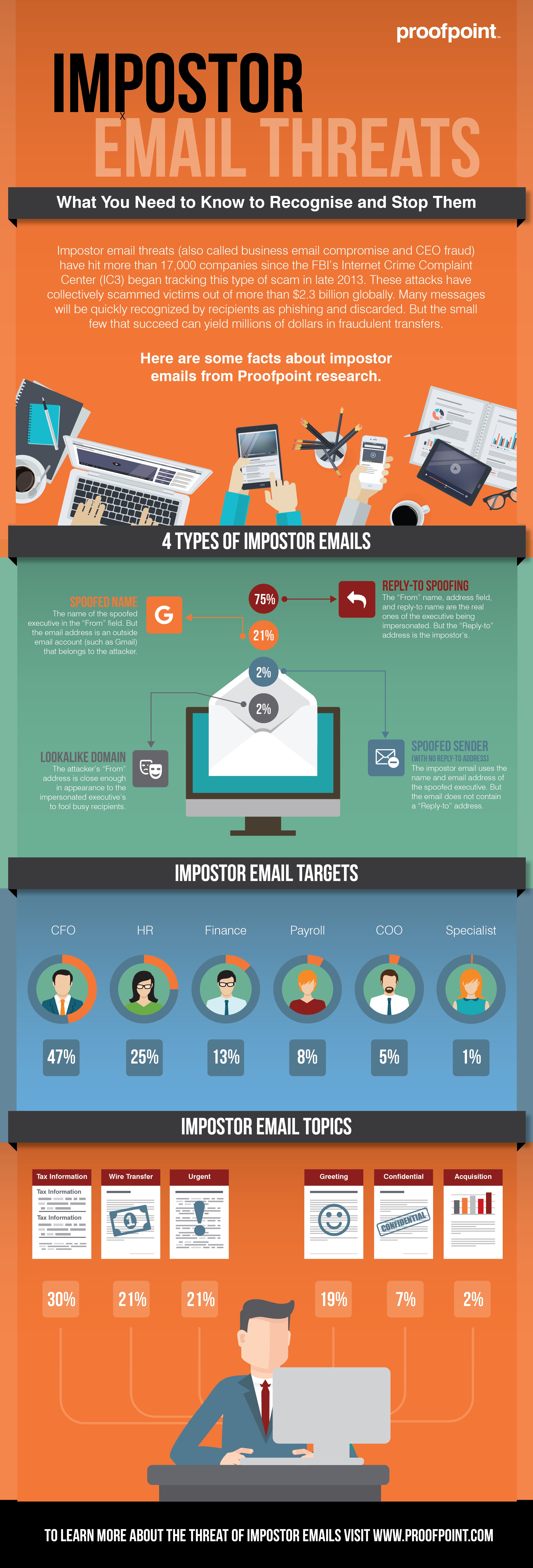
Learn how to identify and stop impostor email threats (also known as business email fraud). This infographic describes the four types of impostor emails, who they target, and the most-used topics for subject lines.
According to the FBI, this type of scam has siphoned more than $2.3 billion from more than 17,000 victims—and those are just reported incidents. Impostor emails succeed for three primary reasons:
- They look and feel legitimate
- They do not include a malicious link or malware attachment
- They do not arrive in high enough volumes to raise red flags in most anti-spam tools
Because these threats do not use malicious attachments or URLs, impostor emails can evade solutions that look for only malicious content or behavior. That’s why they require a different approach. An effective solution must dynamically analyze the attributes of all email as it arrives and detect anomalies that point to an impostor.
Learn More About Proofpoint Solutions:
Email Protection Solutions Suite
Proofpoint Email Security & Protection
To learn more about BEC and CEO email fraud, download The Impostor in the Machine whitepaper.