The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals. It also examines how Proofpoint helps businesses to fortify their email defences to protect people against today’s emerging threats.
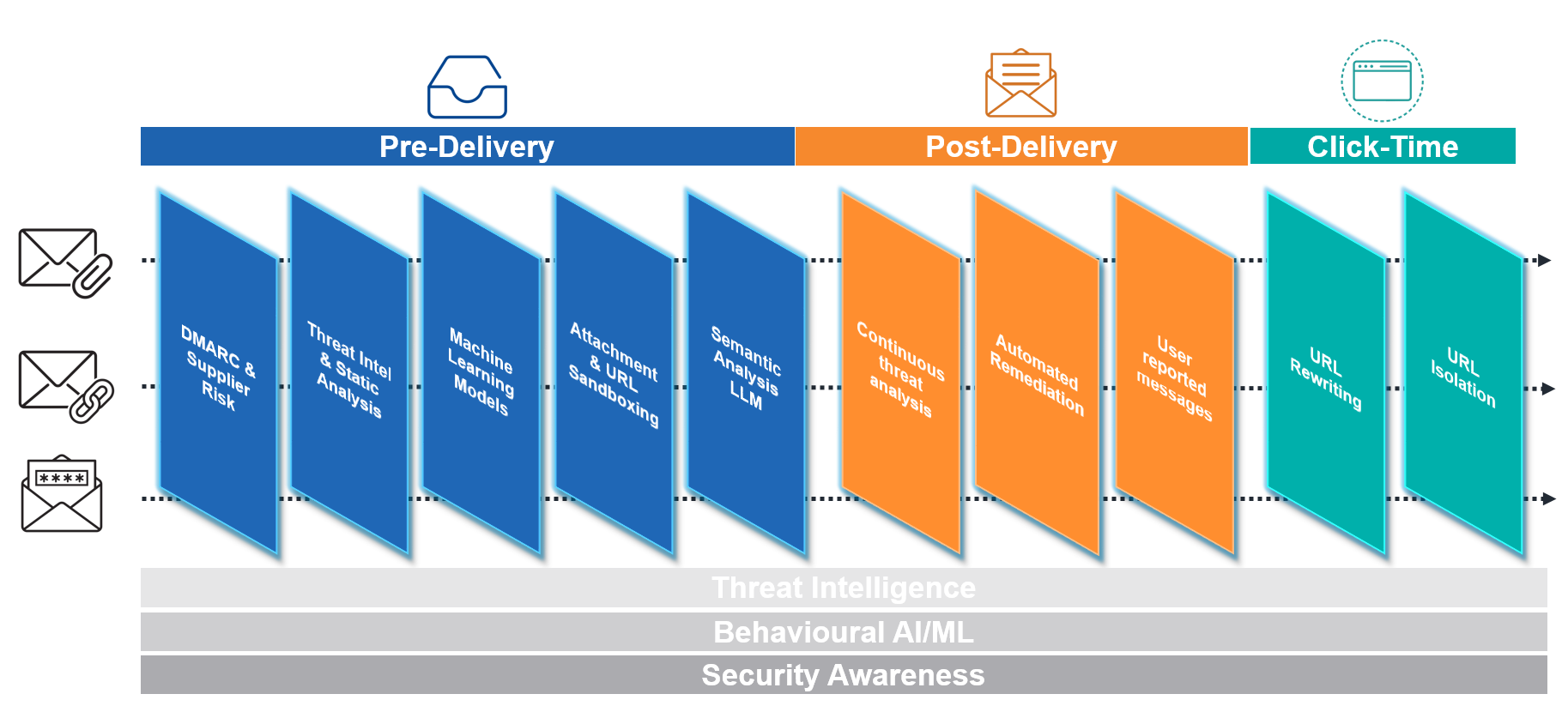
Proofpoint people protection: end-to-end, complete and continuous
So far in this series, we have examined these types of attacks:
- Uncovering BEC and supply chain attacks (June 2023)
- Defending against EvilProxy phishing and cloud account takeover (July 2023)
- Detecting and analysing a SocGholish Attack (August 2023)
- Preventing eSignature phishing (September 2023)
- QR code scams and phishing (October 2023)
- Telephone-oriented attack delivery sequence (November 2023)
- Using behavioural AI to squash payroll diversion (December 2023)
- Multifactor authentication manipulation (January 2024)
- Preventing supply chain compromise (February 2024)
- Detecting multilayered malicious QR code attacks (March 2024)
- Defeating malicious application creation attacks (April 2024)
- Stopping supply chain impersonation attacks (May 2024)
- CEO impersonation attacks (June 2024)
- DarkGate malware (July 2024)
- Credential Phishing Attack (August 2024)
In this blog post, we will look at how threat actors used a business email compromise (BEC) attack to target one of the world’s largest aviation companies and their global network.
Background
Threat actors are increasingly using sophisticated BEC attacks for financial fraud. In these attacks, legitimate business email accounts are compromised so that threat actors can steal funds through unauthorised transfers.
The impact of these attacks is staggering. Organisations report losing more than $50 billion between October 2013 and December 2022. These scams have been reported in all 50 U.S. states and 177 countries, with banks in Hong Kong and China being the primary international destinations for fraudulent funds.
The scenario
A threat actor spoofed an EMEA-based aviation company to target its customers, which included global and US-based aviation companies. During the attack, they sent emails to the customers’ accounting departments, requesting payment for missed invoices.
While Proofpoint detected the attack, another well-known secure email gateway provider failed to catch it. This is because Proofpoint goes beyond the basic requirements for setting custom impersonation policies, which some customers use to address certain BEC threats. These policies may be effective for some BEC threats, but not for others.
The threat: How did the attack happen?
Throughout July, threat actors repeatedly sent emails to aviation companies, requesting payment for overdue invoices. By mid-August, new intelligence and detections from Proofpoint revealed that the domains used in the attack had changed yet again – attackers altered typo-squatted domains at least five times during the extended campaign.
To lend credibility to their emails and stories, attackers also created a fake LinkedIn profile. Over several months, they repeatedly targeted personnel in the accounts payable and finance departments as well as distribution lists tied to finance and accounting.
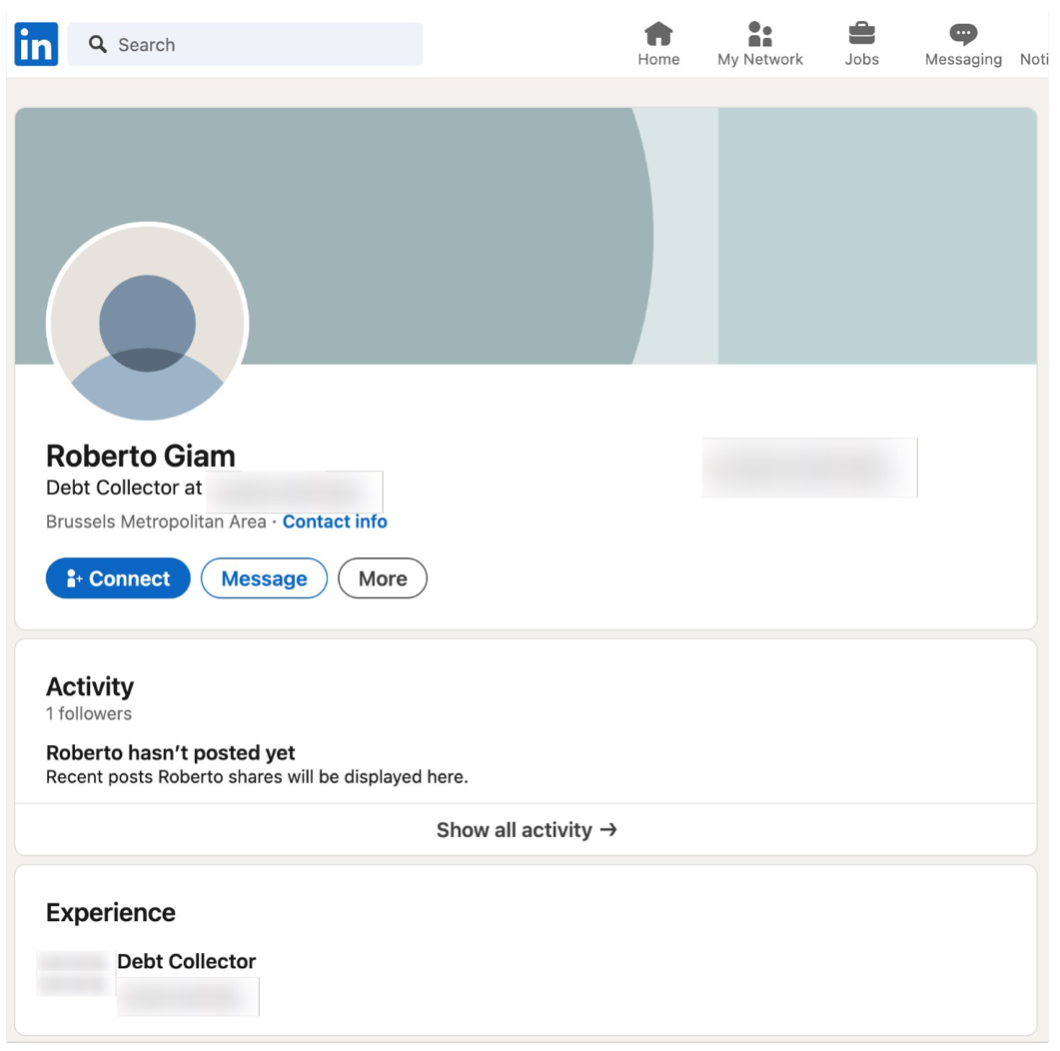
The fake LinkedIn account created by attackers to add legitimacy to their emails.
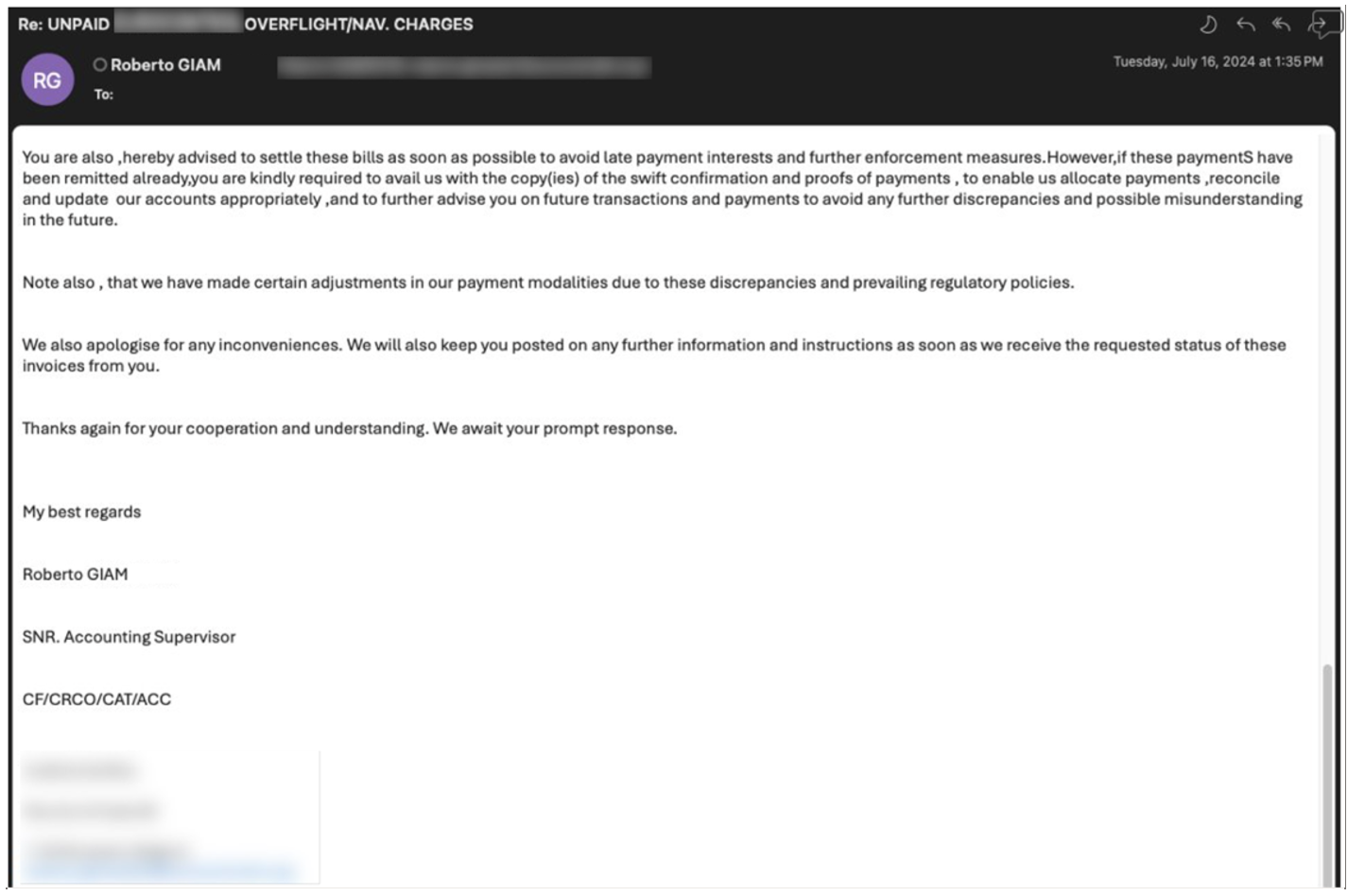
An email spoofing the EMEA-based aviation company.
Detection: How did Proofpoint prevent this attack?
Proofpoint detects many types of malicious email messages. This includes messages used by threat actors that are trying to defraud businesses. Proofpoint uses stateless and stateful AI to analyse the content, including the message body, headers, URLs and payloads.
Proofpoint Targeted Attack Protection (TAP) dashboard flagging BEC and social engineering.
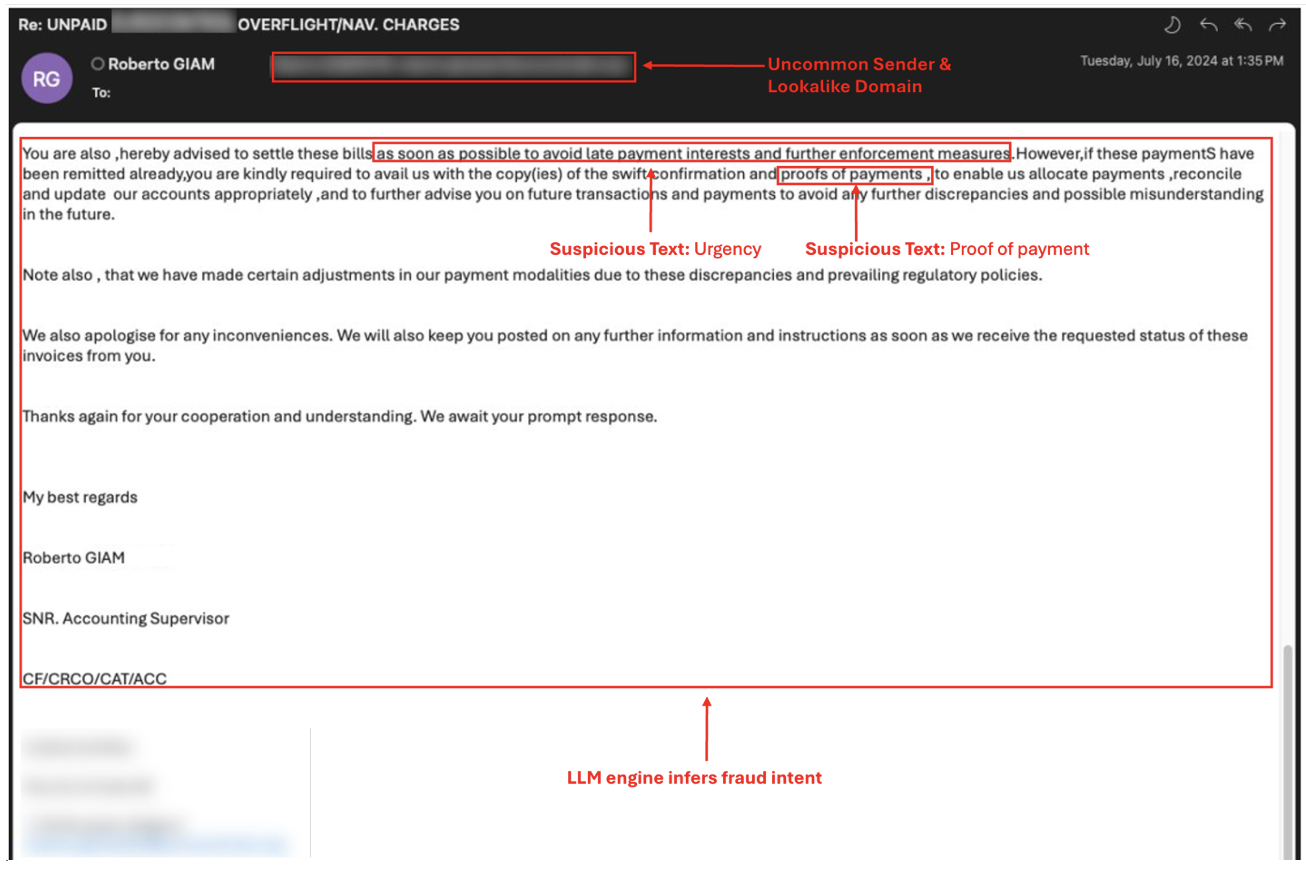
The Proofpoint threat indicators detected in the spoofed email.
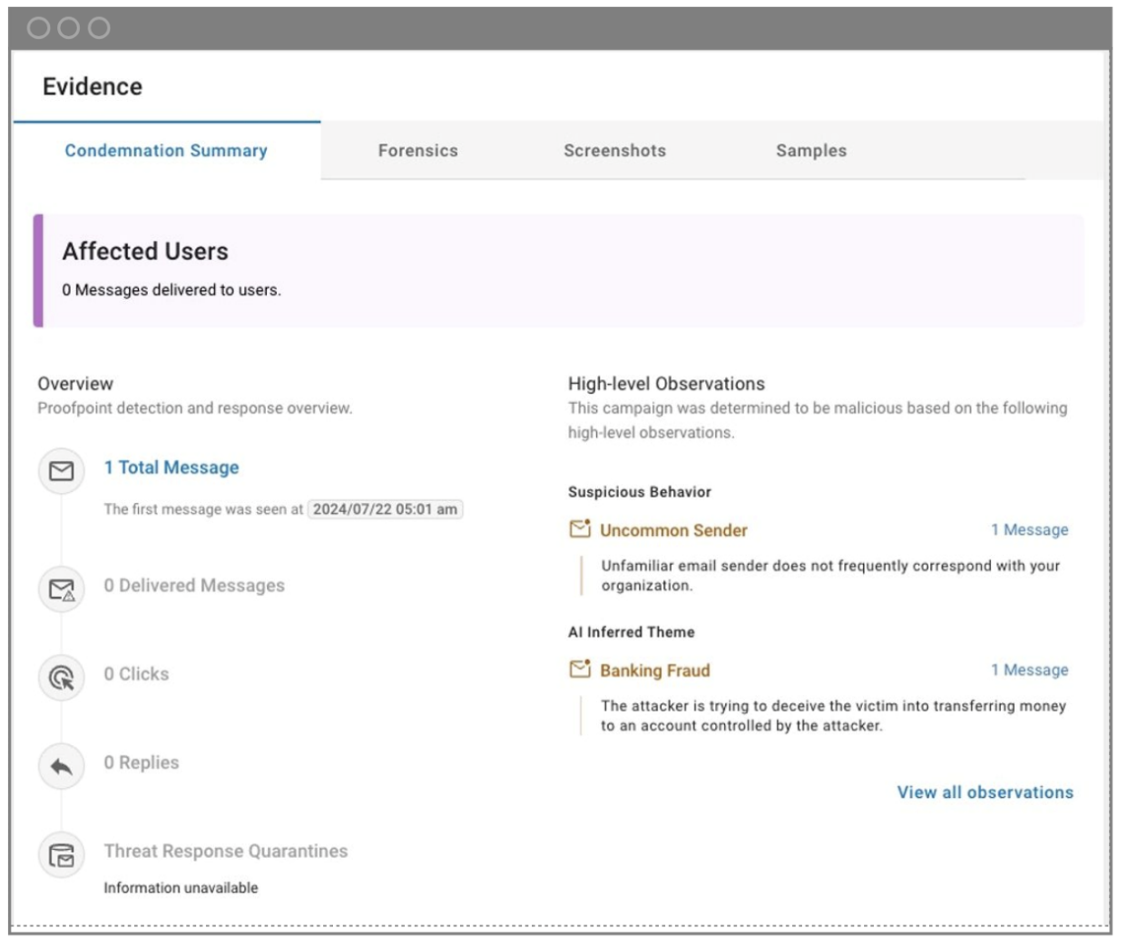
View of Proofpoint TAP dashboard highlighting malicious indicators.
These indicators were detected by Proofpoint:
- Uncommon sender. The recipient and the sender did not have an established relationship and had never corresponded over email. Unexpected messages from new senders do not always mean that an email is malicious. However, when this indicator is combined with other indicators like urgency, they can mean that a message is fraudulent – even when there’s no malicious payload like a URL or file.
- Newly registered domain. The sender’s domain was recently registered, which is an indicator that raises suspicion.
- Low volume domain. Proofpoint assesses sending patterns based on content, volume, the sender’s server, and more to help determine if a message might be malicious. The domain was not only recently registered, but it was also new to the organisation. Plus, it had very low volumes across the rest of our entire customer base.
- Lookalike domain. To mask its malicious identity, the sender registered a domain that looked like an existing supplier’s domain. Using a lookalike domain is a tactic used by bad actors to help make their suspicious requests look legitimate. In this example, the domain had an extra letter “I”. This was a small change that the bad actor hoped would go unnoticed.
- AI-inferred theme. Proofpoint uses a large language model (LLM) to analyse message content and determine its intent using AI-inferred themes.
- Suspicious request. The request asked the recipient to pay the invoices or send proof of payment if the invoice had already been paid. This is suspicious because a legitimate sender would already have the payment details and wouldn’t need to ask for them.
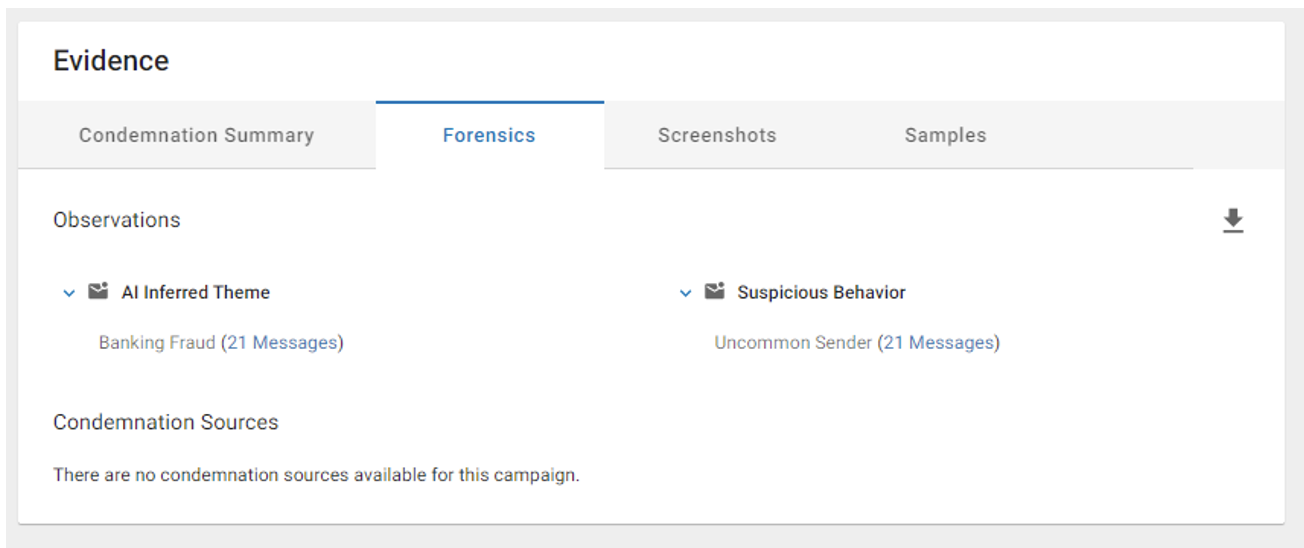
Proofpoint Nexus Behavioral Detections.
Proofpoint Nexus Behavioral Detections uses AI and ML engines to identify suspicious messages with banking fraud themes. In this instance, numerous indicators all added up to fraud, including a financial request, an uncommon relationship, and the use of a newly registered domain. This resulted in Proofpoint condemning the attack.
Remediation: What are the lessons learned?
To protect against vendor impersonation attacks and other BEC threats, it is crucial to implement proactive measures:
- Get pre-emptive email security. The only sure way to keep users safe is to block threats. Look for a tool that combines machine learning algorithms and advanced threat detection. While many tools claim to detect these threats, they often do so too late – after the threat has already reached users’ inboxes. This leaves users vulnerable until threats are remediated.
- Educate your users. Your employees and customers are your last line of defence. Make sure that they receive security awareness training that teaches them about all types of malicious emails, including deceptive and fraudulent requests. This training can help reduce their chances of falling victim to phishing attacks.
- Protect your supply chain. Defend your supply chain from email-based attacks. Look for a tool that uses advanced AI and the latest threat intelligence to detect compromised supplier accounts. It should also prioritise the accounts that security teams need to investigate.
Proofpoint delivers human-centric protection
Proofpoint end-to-end protection against BEC uses advanced machine learning and artificial intelligence to detect and prevent financially focused email fraud. Our integrated platform analyses multiple message attributes to identify and block various BEC tactics, such as domain spoofing, display name spoofing, and lookalike domains. By providing visibility into the users who are most targeted and automating threat detection and response, Proofpoint ensures comprehensive protection.
Register for one of our Proofpoint Protect 2024 events in London, Austin, or Chicago to learn how you can protect people and defend your data in today’s complex threat landscape.

