
A spate of scam emails, all on the same theme, has prompted this week’s Breaking Scams post. In the space of several days, I received three suspicious looking emails all with the same theme, Windows Outlook “CANCEL/COMPLETE-REQUEST”.
The Microsoft Outlook Spam Email
All of the emails received contained the same message:
Dear Valued User,
Please view the attachment and CANCEL/COMPLETE-REQUEST.
Thanks,
Windows Outlook Team
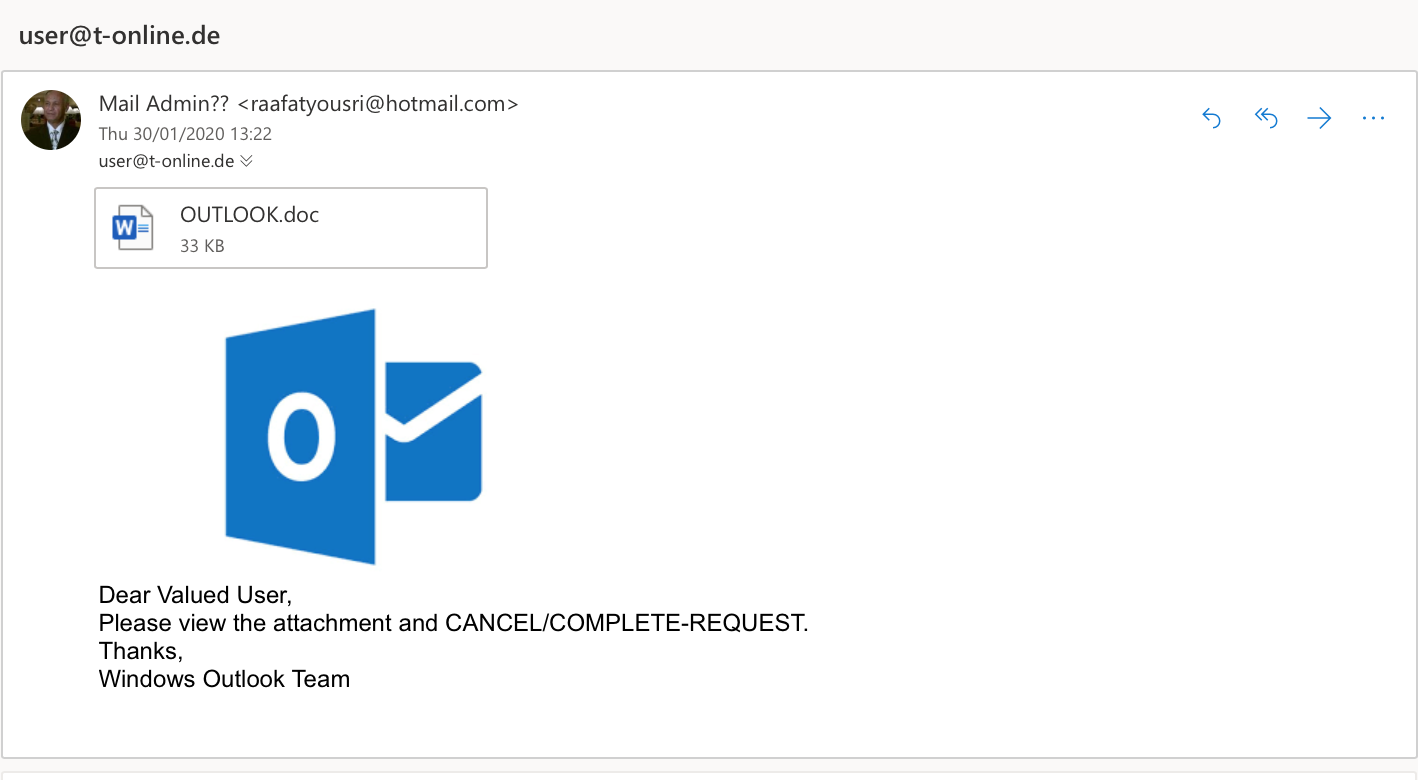
Each also contained a Word
document as an attachment.
There was no link in the email itself.
The email sender’s address was clearly not from Office 365 support, but the fraudsters had used Hotmail email addresses. Outlook was originally Hotmail and the fraudsters possibly hoped that recipients might equate Hotmail with Outlook, giving the email legitimacy.
The Email Phishing Attachment
Before attempting to open the Microsoft Word document attached to the email, I checked for malware using an online scanner. The attachment was shown to be free from malware. This meant that it must contain some other device to phish users.
On opening the attachment there was clear evidence that this was a phishing exercise. The document contained a letter purporting to be from Microsoft:
- The letter used Microsoft branding to create a sense of trust.
- The letter contained a sense of urgency and fear, stating that “because of security concerns, Microsoft had to free up space on servers”. This would result in email accounts being ‘terminated’ with the permanent loss of emails.
- The letter contained a link to ‘validate’ your email account to prevent the termination.
All of the above created a very suspicious letter. But it was other factors, including the poor grammar and formatting that gave the game away.
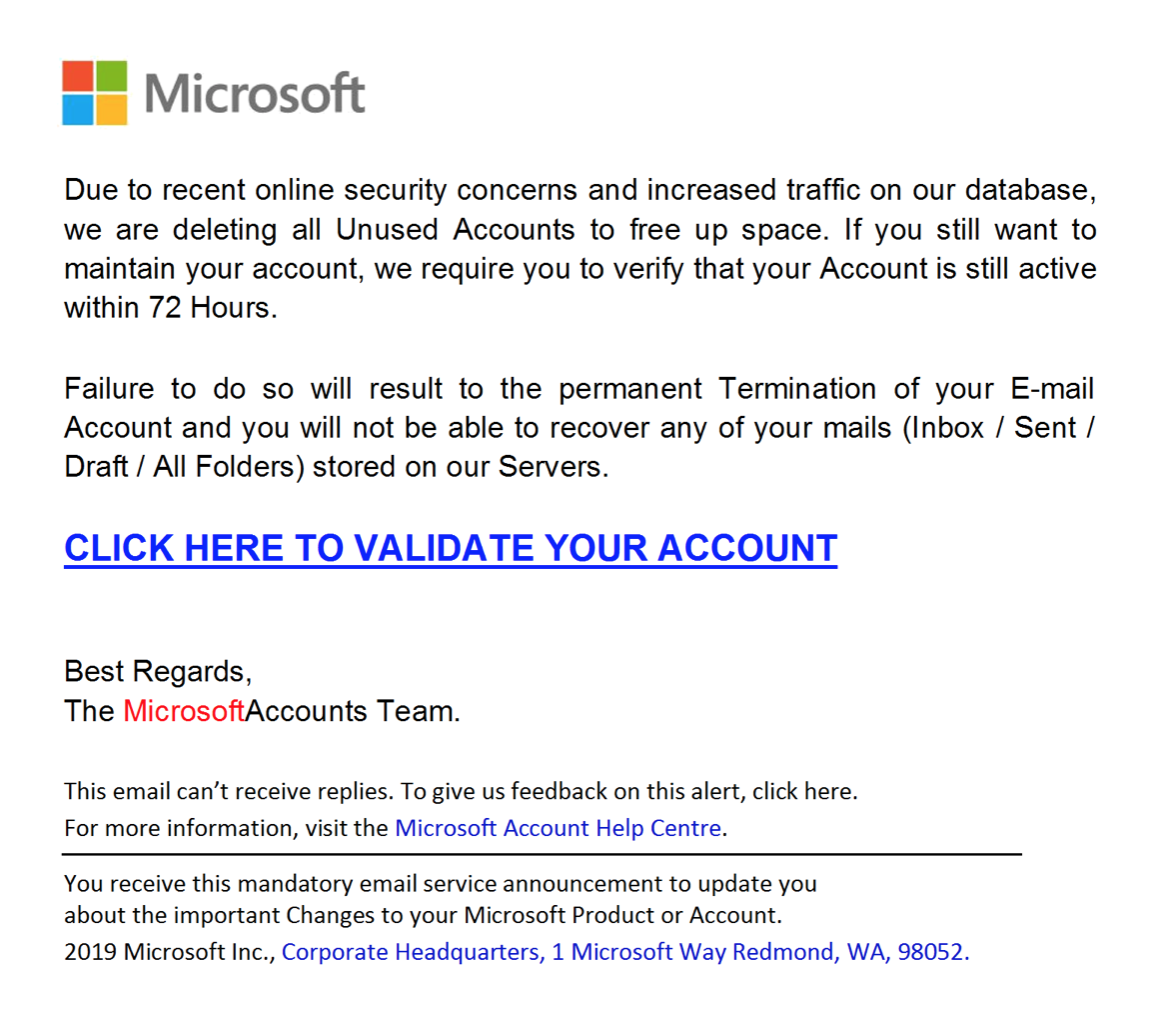
On clicking the link in the letter, you are taken to a website, which looks exactly like an Office 365 login page. If login credentials were entered into this page, they would be immediately sent to the fraudster behind the scam who would then use them to access your real Outlook account.
Anti-spam filters – do they work?
Microsoft Office Outlook 365 has spam filters in place. However, spam filters are not 100% effective. Cybercriminals continuously attempt to circumvent spam filters using various techniques, including the tactic used in this weeks’ Breaking Scam. Hiding a malicious link in a Word document means that spam filters cannot easily see the link to check it.
Hiding malicious links in attachments is an increasingly typical way to get around technological controls of phishing emails. This is why technology alone cannot prevent phishing. Make sure that your employees are aware of how phishing, of all types, works. Security awareness training is a fundamental way to ensure that your staff and your business remains cyber-safe.
Why not help your colleagues stay safe and send them this little reminder. Feel free to edit, copy/paste the advice below:
The Microsoft Outlook Scam
Emails that pretend to be from Microsoft Outlook are doing the rounds. They contain an attachment which is a spoof letter from Microsoft. The letter threatens to shut down your email account unless you take action.
AVOID OPENING THE LETTER. DO NOT CLICK ON THE LINK IN THE LETTER. IF YOU ENTER LOGIN CREDENTIALS IN THE WEBSITE THAT THE LINK GOES TO, THEY WILL BE STOLEN BY A CYBERCRIMINAL
For more information on what to do if you receive a phishing email check out “What to Do if You Click on a Phishing Link?”
Don’t forget to share this with your colleagues and friends and help them stay safe.
Let’s keeping breaking scams!

