The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals and how Proofpoint helps organisations better fortify their email defences to protect people against today’s emerging threats.

Proofpoint people protection: end-to-end, complete and continuous.
In this series, we have examined the following types of attacks:
- Uncovering BEC and Supply Chain Attacks (June 2023)
- Defending Against EvilProxy Phishing and Cloud Account Takeover (July 2023)
- Detecting and Analysing a SocGholish Attack (August 2023)
- Preventing eSignature Phishing (September 2023)
- QR Code Scams and Phishing (October 2023)
- Telephone-oriented Attack Delivery Sequence (November 2023)
- Using Behavioural AI to Squash Payroll Diversion (December 2023)
- Multifactor Authentication Manipulation (January 2024)
- Preventing Supply Chain Compromise (February 2024)
- Detecting Multi-layered Malicious QR Code Attacks (March 2024)
- Defeating Malicious Application Creation Attacks (April 2024)
- Supply Chain Impersonation Attacks (May 2024)
- CEO Impersonation Attacks (June 2024)
- Reeling in DarkGate Malware Attacks from the Beach (July 2024)
- Credential Phishing Attack Targeting User Location Data (August 2024)
- Preventing Vendor Impersonation Scams (September 2024)
Background
According to The Center for Internet Security, Inc., SocGholish remains the top malware downloader, responsible for 60% of all these types of attacks. Why do cybercriminals favour SocGholish? Because it’s a highly effective social engineering tool to distribute malware through malicious or compromised websites. It uses fake software updates, most often masquerading as browser updates, to trick users into downloading malware.
Once the malware is installed, it uses different methods to redirect traffic and deliver harmful payloads. This allows it to steal sensitive data from a user’s system. SocGholish can also be used for further attacks, like installing remote access tools or even ransomware. SocGholish stands out because of several key features:
- Social engineering. SocGholish tricks users into downloading malware by mimicking software updates, usually for browsers. These familiar prompts make users more likely to trust them and fall for the scam.
- Wide attack surface. SocGholish often spreads through legitimate websites that have been compromised. When users visit these sites, they are presented with a prompt to download a fake update. Since legitimate websites are used as the delivery mechanism, users are more likely to believe the prompt and download the malware.
- Easy customisation. Threat actors can modify SocGholish code to avoid detection by antivirus and email security tools. This flexibility helps it stay ahead of cybersecurity defences.
- Targeted and broad campaigns. SocGholish can be used in both wide-reaching and targeted attacks, which makes it versatile. Threat actors can tailor fake updates to target specific groups, which makes it effective for general malware distribution or more focused phishing campaigns.
- Persistent and hard to detect. SocGholish often delivers its malware in stages using obfuscated scripts, making it difficult for security systems to detect. This stealthy behaviour allows the malware to remain in a system longer without raising alarms.
It’s easy to see why SocGholish is a favoured tool for cybercriminals. It combines social engineering with malware that’s not only easy to distribute but also easy to tweak to avoid detection.
SocGholish attack sequence:
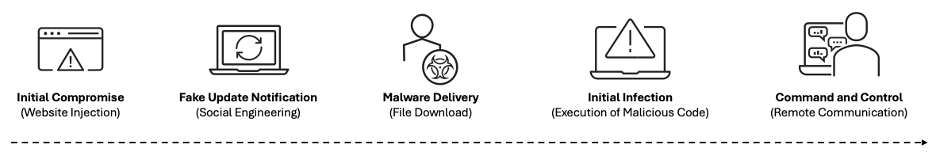
Typical SocGholish attack sequence.
- Initial compromise. Threat actors first compromise legitimate websites by injecting malicious JavaScript into them.
- Fake update notification. When a user visits the site, a pop-up or redirect appears that claims their browser or software needs an urgent update.
- Malware delivery. If the user believes the pop-up, then they download a file, which is often disguised as a legitimate installer (.zip or .exe). This file contains the SocGholish malware.
- Initial infection. Running the file executes the SocGholish malware. It often starts by dropping scripts onto the user’s system. This enables further malicious activity while staying under the radar of antivirus software.
- Command and control. Now, SocGholish establishes communication with the threat actors command and control servers. This allows the malware to receive additional instructions. The servers may instruct the malware to perform different actions, such as downloading more malware, exfiltrating data or setting up remote access for the attacker.
The Scenario
In this recent attack, a bad actor known as TA569 used SocGholish malware to target more than 1,000 organisations worldwide, sending over 232,000 malicious messages. The attack was so stealthy that 14 established email tools failed to detect it. And it was meticulously planned.
In this instance, TA569 targeted a Texas-based healthcare services organisation that serves more than 50,000 adults and children each year.
The Threat: How did the attack happen?
Here’s a closer look at how the attack unfolded:
1. Legitimate message. Victims received an email promoting a well-known, upcoming healthcare conference. The email was legitimate – not written by the threat actor – and it contained a URL link to a legitimate webpage. However, the webpage was compromised. With SocGholish malware campaigns, the malicious code doesn’t activate until a user interacts with the compromised website.
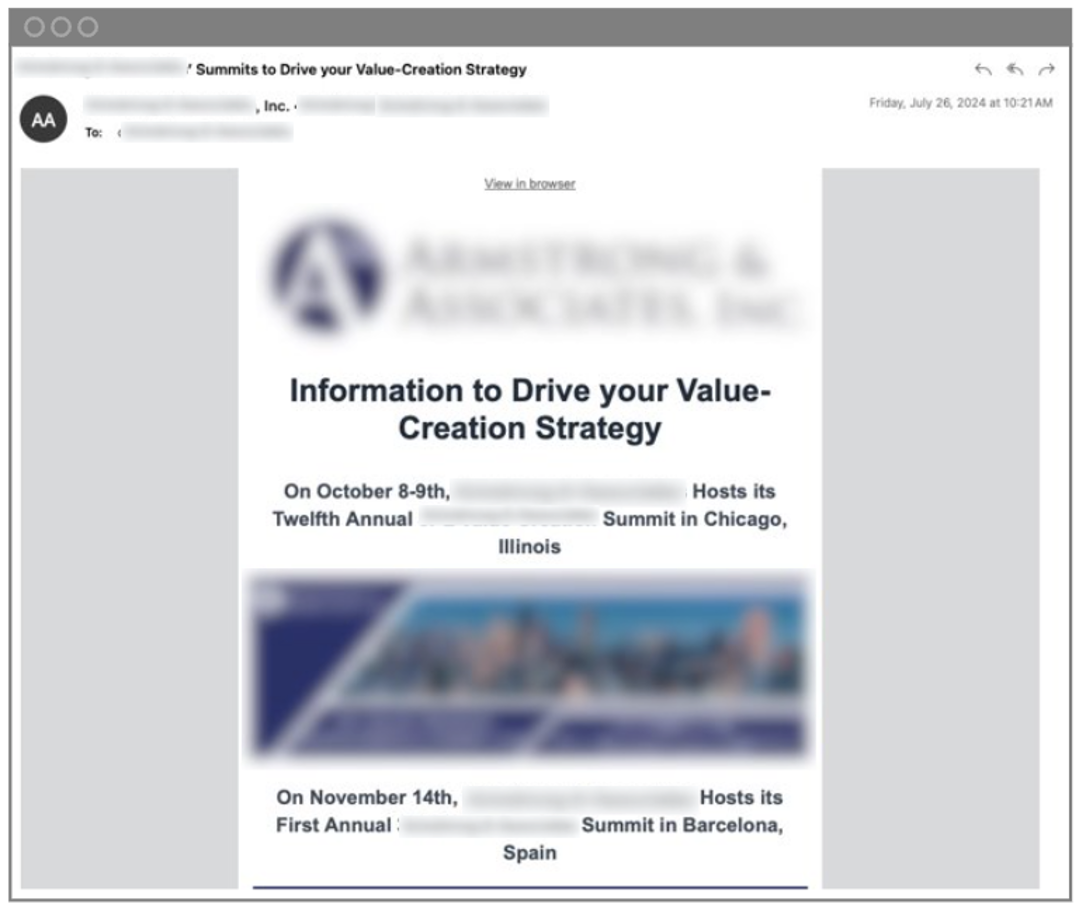
Legitimate email that was received by the user.
2. Fake update notification. SocGholish does not target every user; it tends to be selective. Typically, users get a fake update notification based on their browser cookies, system vulnerabilities and other identifying information. This allows SocGholish to focus on users who are more likely to fall for the fake browser update prompt, which increases the chances of infection.

Fake browser update notification request.
3. Malware delivery. If the fake alert convinces the user to update, then they are directed to download a file, which is often disguised as a legitimate installer (.zip or .exe). This file contains the SocGholish malware.
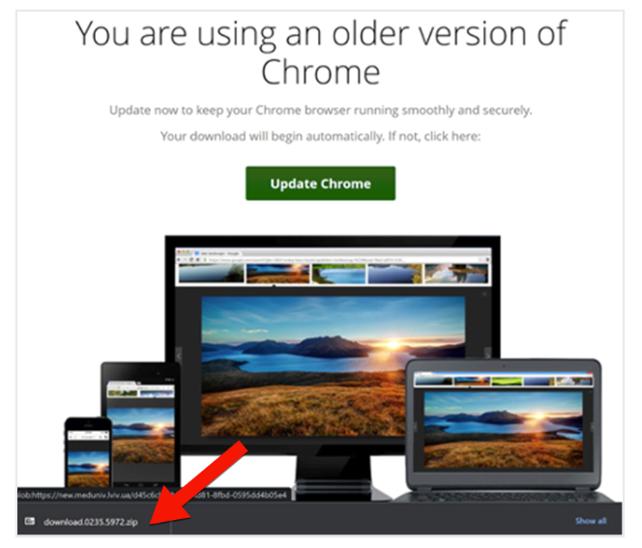
SocGholish malware download file.
Detection: How did Proofpoint detect the attack?
SocGholish malware is very difficult to catch. It won’t activate if it detects that it’s in a simulated environment, like a threat analyst’s sandbox. What’s more, it uses legitimate messages for distribution. In this case, Proofpoint used a combination of advanced signals and layered analysis to detect the SocGholish attack including:
- Sender reputation
- Deep URL content analysis
- Network activity analysis
- Volume of unique URL variants
- Heuristic examination of webpages
- Dynamic analysis of HTML content, payloads, and other artifacts
- Sender and recipient relationship based on past communication
Although the email invitation to the healthcare conference was not malicious, there were signs that it might be suspicious. So, we investigated deeper. We found that we had encountered this threat actor, TA569, before. TA569 is a well-known attacker who uses SocGholish malware to infect legitimate websites.
Signals that Proofpoint used to condemn the message as a threat.
Here are a few indicators that we analysed using our multi-layered detection stack.
When we analysed the network activity, we found malicious behaviours that were linked to the malware phoning home to Command and Control (C2) servers. We also identified redirections to a DNS service associated with SocGholish.
Plus, we found the use of compromised scripts. These injections are similar to those seen in other malicious campaigns, which make detecting and mitigating these attacks more challenging. Coupled with TA569’s known techniques – such as geofencing, social engineering, and JavaScript – we recognised this as a significant threat.
We also used our pre-delivery behavioural AI detection stack to sandbox the malicious URL within the legitimate message. Suspicious message-level characteristics helped us decide to sandbox the URL using our message hold capability. In this case, an uncommon sender, an unusual URL domain, and a few other characteristics were suspicious, resulting in the sandboxing of the malicious URL prior to be delivered to the user’s inbox. We also detected a fake update JavaScript in the compromised webpage. Together, these indicators helped us to identify the SocGholish malware attack so that we could block it before delivery.
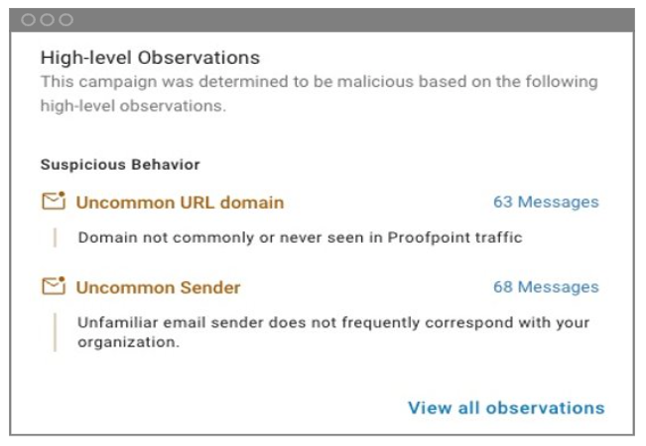
Condemnation summary of signals Proofpoint used to sandbox the malicious URL.
As noted earlier, this SocGholish attack was so stealthy that 14 other email security tools missed it. For example, Abnormal Security, a post-delivery email security provider, failed to detect and block the SocGholish attack due to its basic approach to threat detection. Although they claim to use behavioural AI to identify advanced email threats, they struggle with SocGholish.
In this case, the email message was legitimate. Plus, it was not flagged as unusual based on behavioural sending patterns, URL reputation analysis or message-level indicators. Without pre-delivery detection, URL sandboxing, deep URL content analysis and advanced threat intelligence, Abnormal Security will continue to miss these types of advanced threats.
Remediation: What are the lessons learned?
To protect against SocGholish malware attacks, here’s what we recommend:
- AI and threat intelligence. As Qui-Gon Jinn once said: “You cannot prevent what you cannot see coming.” While the quote reflects on a key lesson about the importance of foresight and awareness in a Jedi’s life, it also be applied to cybersecurity. Without insight into the threat landscape, you’re at a disadvantage. Find a tool that uses global threat intelligence and AI-driven machine learning to identify and block new and emerging threats like SocGholish before they impact your people and business.
- Deep URL analysis. Many email security tools fail to detect advanced threats like SocGholish because they rely on static URL reputation analysis. Look for a tool that goes beyond basic URL reputation and includes in-depth URL analysis. It should inspect the content that a suspicious URL leads to, identify any URL redirects, and analyse what happens after the URL is accessed, such as a script that triggers a download. This enables your organisation to detect and block SocGholish attacks more quickly.
- Pre-delivery threat protection. According to Proofpoint research, 1 in 7 clicks on unsafe links occur within 60 seconds of an email’s delivery. This highlights why pre-delivery protection is so important. Look for a tool that holds suspicious messages with URLs for sandbox analysis. It should use behavioural signals and threat intelligence to determine if a message needs to be inspected further. Pre-delivery URL sandboxing and message hold keeps users safe by blocking malicious messages before they are delivered.
Proofpoint delivers human-centric protection
Threat actors are constantly finding new ways to get past existing security tools. SocGholish is just the latest threat that proves why multi-layered and robust email security measures are so critical to protecting your organisation.
To stay ahead of evolving threats, you need a comprehensive approach to protect against threats that target your people. Proofpoint offers continuous detection throughout the email delivery lifecycle – pre-delivery, post-delivery, and click-time. Our approach ensures end-to-end protection against modern email threats. We achieve a 99.99% efficacy rate by combining deep URL analysis and URL sandboxing techniques to help you stay ahead of threat actors.
To learn how to protect your people and business against threats like SocGholish, download our Proofpoint Threat Protection solution brief.

