There are three cybersecurity truths that have stood the test of time (so far).
- Most breaches involve the human element. The latest Data Breach Investigations Report (DBIR) from Verizon notes that more than three-quarters (76%) of all breaches involve a human element.
- Phishing is one of the most common tactics for gaining initial access to a business. The DBIR says phishing was the second-most used tactic in 2023, right after stolen credentials. (Notably, credentials are often lost in phishing attacks first.)
- People are willing to take risks. That’s why they often fall victim to attacks—because they take risky actions, like clicking on links and opening attachments from people they don’t know. Research for our 2024 State of the Phish report shows that 68% of people do this.
Given these truths, a human-centric security strategy is critical to protecting an organisation. And mitigating human risk should be an important foundational pillar.
This approach to cybersecurity recognises that while technological solutions are essential, they are not sufficient on their own. Human behaviour must be addressed directly. If you build an awareness programme that is guided by threat intelligence and gives users the tools to respond to phishing attacks, you can attain quantifiable results.
In this blog, we’ll discuss three tips that you can use right now to build your security awareness training programme in a way that empowers your employees to change their behaviour.
Tip 1: Prioritise high-risk user groups
Human-centric cybersecurity starts with having visibility into who presents the greatest risk to your business. Often, the actions of a very small percentage of employees are the root cause of most security incidents. When you understand who presents the most risk, you can maximise your programme’s impact by improving the resilience of these individuals.
For our 2024 State of the Phish report, we asked information security professionals who they believe represent the greatest risk to their organisations. The top group were the users who had access to critical data (privileged users).
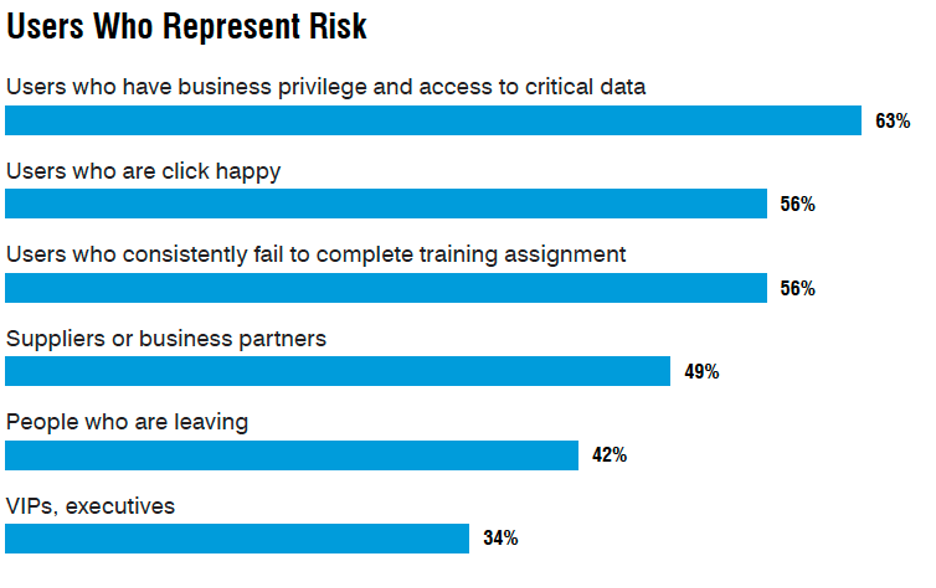
A chart that shows users who represent risk within companies. (Source: 2024 State of the Phish report from Proofpoint.)
Privilege risk is one key factor in quantifying total human risk. It considers the amount of damage that could result from a successful attack. However, you must also consider:
- Attack risk, which demonstrates that the more a person has been attacked in the recent past, the higher the probability that they will be attacked in the near future.
- Vulnerability risk, which evaluates the probability that an attack would be successful if a person is attacked. For this risk factor, it is important to track both real and simulated user behaviours such as actual URL clicks within live email and performance against security awareness knowledge assessments and phishing simulations.
Proofpoint makes it easy to quantify human risk and identify who represents the greatest risk to your business. Instead of manually tracking human risk across the three key risk factors of privilege, attack and vulnerability, our customers can use Proofpoint Nexus People Risk Explorer (NPRE).
With NPRE, each person receives a user risk score based on their behaviour and identity information. Users are automatically grouped based on their scores. With user risk insights from NPRE, you can easily prioritise which groups need the most attention and decide how to best deliver your training to maximise its impact.
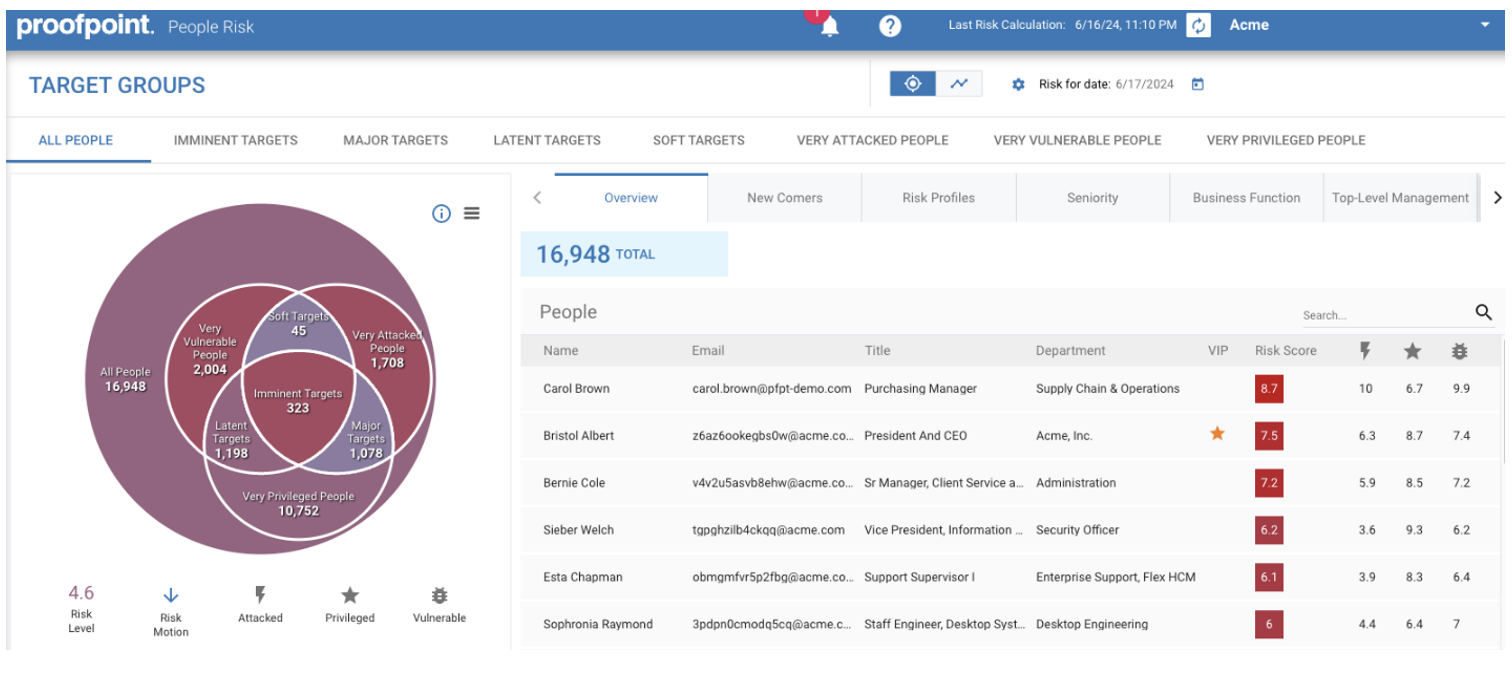
A view of the dashboard for Nexus People Risk Explorer.
Tip 2: Keep your programme agile
The threat landscape impacts every business differently. Comparing a financial services company to a manufacturing company may show that the former is targeted more often with ransomware than supply-chained based BEC attacks.
It is important to keep your programme agile so that you can easily adjust based on how the landscape evolves over the year. Ensuring that you are continuously monitoring the threats that target your users is the next key tip to maximise your training impact.
Say that you are tracking a high-risk user group of Very Attacked People™ (VAPs). Users in this group are attacked much more often than average users and, based on the intel, they are being targeted with financial services-related phishing lures. Below is an example of how Proofpoint Targeted Attack Protection (TAP) can help you track your VAPs.
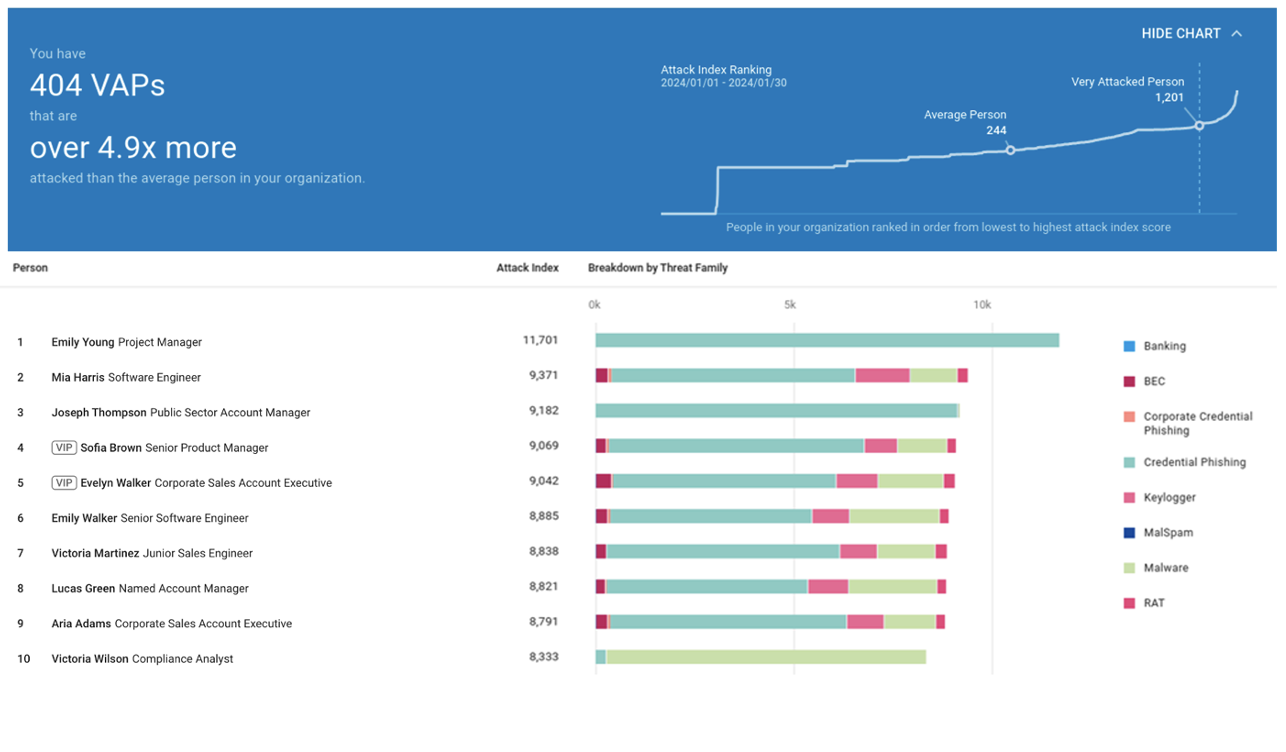
A view of the dashboard for Proofpoint TAP.
Using this data, you can tailor your security awareness training programme. First, you can use phishing simulations based on current banking-themed attacks.
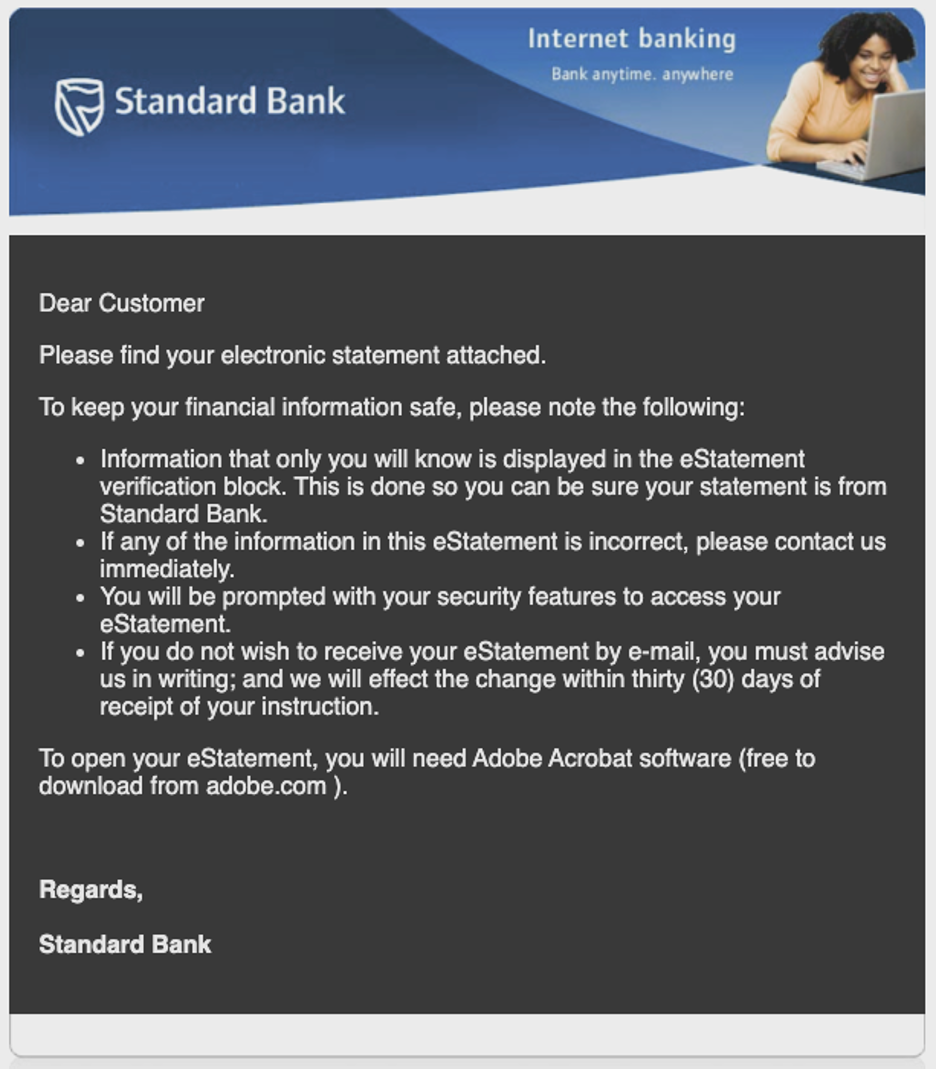
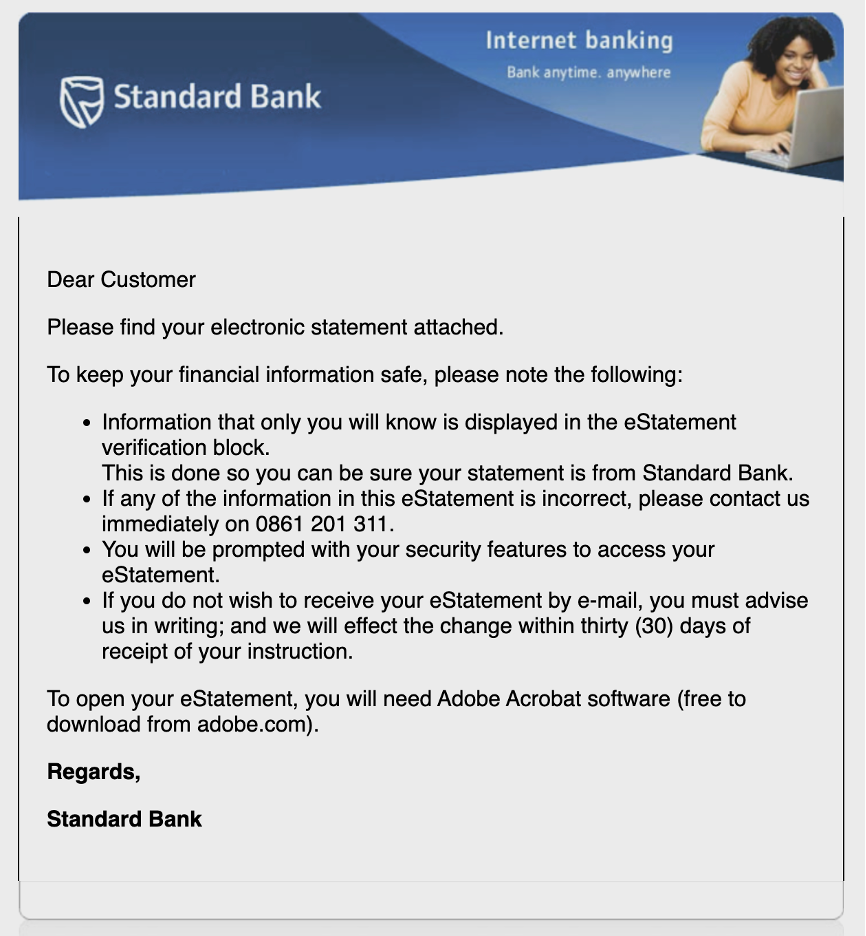
Examples of financial services phishing lures.
Next, based on a user’s performance against these lures, and their role and responsibilities, you have an understanding of the type of training content that they need to improve their real behaviours.
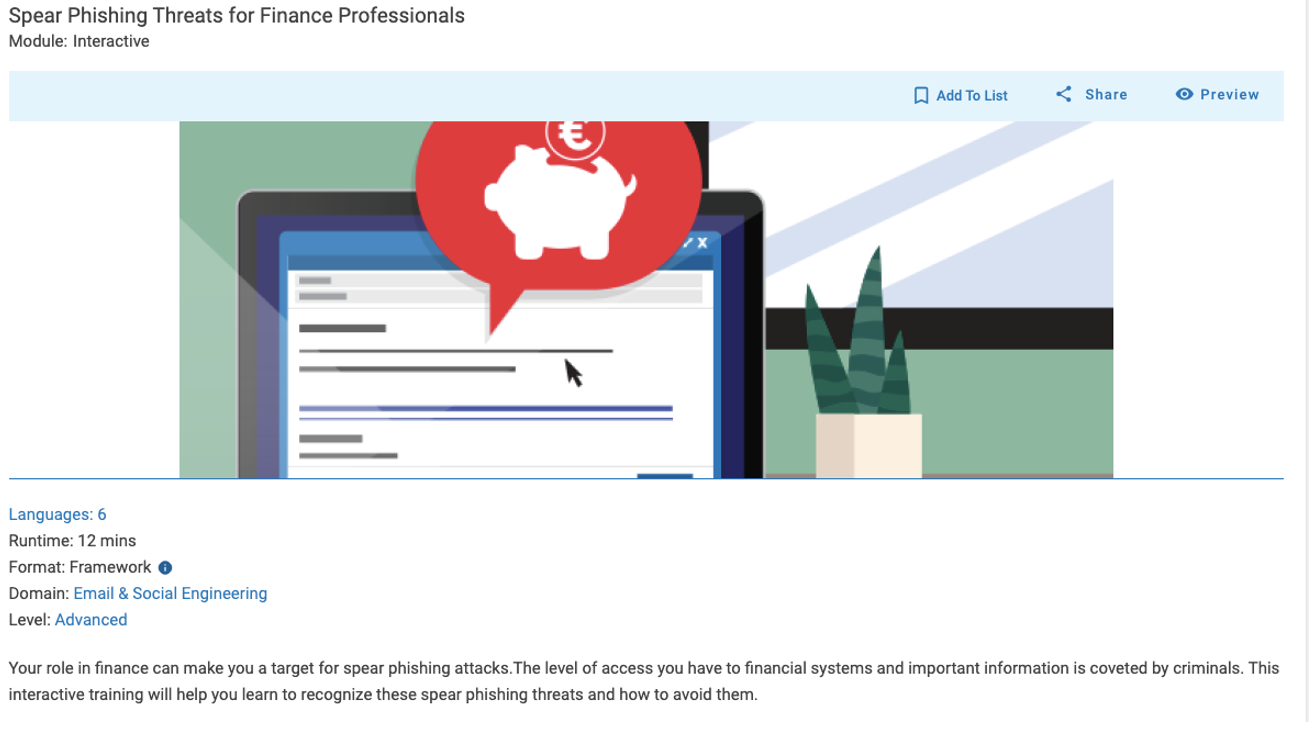
An example of an educational module from Proofpoint Security Awareness.
When you provide people with relevant security awareness training that is based on the attacks that bad actors are using to actively target them, then they will be better equipped to retain what they learn. And as they become more confident in their ability to recognise these attacks, they will feel empowered to report suspicious activity.
Tip 3: Give users tools to respond to phishing attacks
Once you incorporate Tips 1 and 2 and provide timely, relevant education as attacks occur, your users’ knowledge will improve. However, rather than simply avoiding attacks, your users will feel more empowered to actively report phishing attacks.
It is therefore critical to provide an easy-to-use tool for users to report suspicious email. At Proofpoint, we have partnered with Microsoft to deliver an integrated PhishAlarm reporting button.
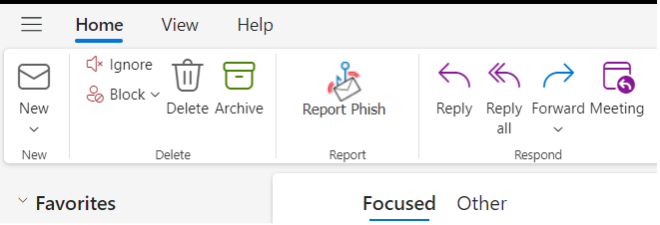
A screenshot of the PhishAlarm “Report Phish” button from Proofpoint.
PhishAlarm is supported across Google Workspace and all versions of Microsoft Outlook clients including the latest version of Outlook and Outlook for Microsoft 365. In the new version of Microsoft Outlook, the PhishAlarm button can directly replace the existing Microsoft reporting button so that it is the only email reporting button on the Outlook ribbon. This placement eliminates any confusion as to where the reported message will go.
A true differentiator is that Proofpoint Cloud Threat Response analyses the reported message. It also automates investigation for our customers, is backed by our industry-leading threat intelligence and saves administrative resources. It can be enabled to automatically remediate threats by pulling the malicious message out of every inbox across the business with our Closed-Loop Email Analysis and Response (CLEAR).
Fostering a culture of vigilance
Building an effective security awareness programme for your employees is crucial to meet the challenges presented by today’s cybersecurity landscape. Focus on high-risk user groups, maintain an agile approach to training and equip users with the tools to respond to phishing attacks. Together, these tactics can help you significantly enhance your company’s security posture.
When you prioritise empowering your employees, you can reduce the risk of breaches and foster a culture of vigilance and proactive defence against cyber threats. Implementing the tips outlined in this post will help to ensure your security awareness program is comprehensive as well as dynamic and responsive to the ever-evolving threat landscape. Ultimately, these measures can help you to create a more resilient and secure organisation.
If you are still struggling to reduce user phishing vulnerability, Proofpoint is here to help. Contact us today.
Fostering a culture of vigilance
Building an effective security awareness program for your employees is crucial to meet the challenges presented by today’s cybersecurity landscape. Focus on high-risk user groups, maintain an agile approach to training and equip users with the tools to respond to phishing attacks. Together, these tactics can help you significantly enhance your company’s security posture.
When you prioritize empowering your employees, you can reduce the risk of breaches and foster a culture of vigilance and proactive defense against cyber threats. Implementing the tips outlined in this post will help to ensure your security awareness program is comprehensive as well as dynamic and responsive to the ever-evolving threat landscape. Ultimately, these measures can help you to create a more resilient and secure organization.
If you are still struggling to reduce user phishing vulnerability, Proofpoint is here to help. Contact us today.

