The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals. It also examines how Proofpoint helps businesses to fortify their email defences to protect people against today’s emerging threats.
The interconnectedness of today’s business ecosystems has created a prime target for attacks on digital supply chains. Within those supply chains, email remains the No.1 vector to access people and poses a major risk. According to our research, more than 80% of Proofpoint customers receive an email attack each month from a trusted vendor or supplier. And these attacks can be quite costly. Based on IBM’s Cost of a Data Breach report, the average financial loss from a data breach that involves the supply chain tops $4.8 million.
Unlike native and API-based email security tools, Proofpoint regularly stops these highly targeted attacks before they reach employee inboxes. If you’ve been following this series, you will have seen in earlier blog posts that we’ve covered many different types of supply chain attacks. We’ve seen attackers targeting the legal, manufacturing, aviation industries, and more with complex impersonation and vendor email compromise techniques.
Today, we’ll explore a phishing attack on a public sector agency, which was disguised as an electronic fax (eFax).
Background
In this example, bad actors exploited a supplier’s email through vendor email compromise. This occurs when an attacker gains access to and weaponises an email account of a smaller business partner instead of going directly after a bigger, more secure organisation. This can be a very effective tactic. Attackers know that larger organisations typically have better resources, bigger budgets and more mature cybersecurity defences to keep them out.
When this tactic is combined with credential phishing, attackers are able to trick even the savviest recipients. In fact, Proofpoint research shows that employees are three times more likely to click on a phishing link when it comes from a trusted partner. That’s not only because there’s an inherent trust between senders. It’s also due to the fact that threat actors may use legitimate file hosting services and extremely convincing fake login sites to spoof well-known brands.
The scenario
Proofpoint recently detected this potent combination of threats during a customer’s initial evaluation process. This threat was started by a cybercriminal who gained access to the email account of a marketing professor at a public university. With this access, the attacker sent a phishing link – which appeared to be an eFax – to the email address of a government agency’s employee who the university professor had previously communicated with. Because the employee was a known contact in the professor’s inbox, the attacker was able to bypass many layers of security intended to catch such threats.
As with many vendor email compromise attacks, this threat was specific, highly targeted, and unique to the sender. Because Proofpoint has extensive global email visibility and insights, we were able to see that the same phishing link was delivered to less than 40 other accounts worldwide.
Notably, the phishing link was hosted by a legitimate, well-known file sharing website. As a result, it was missed by this agency’s Microsoft 365 native email security tool, which lacks comprehensive URL sandboxing capabilities. And because of the extended nature of this attack chain, it was further missed by an API-based security tool after it was delivered.
Fortunately, Proofpoint detects and blocks phishing messages before they ever reach a user’s inbox. If this customer had been using Proofpoint, its employees would never have been exposed to the account takeover risk.
The threat: How did the attack happen?
Here’s a breakdown of the attack.
1. Setting a lure. To set the trap, the attacker created a highly stylised message that looked like an eFax notification, which was delivered from a third-party sender on behalf of the university’s marketing professor. All the intended victims of this attack were Bcc’d within the message.
The message included a phishing link as well as fake PDF images and contextual details. These details helped to increase the message’s believability to more likely trick the victim. The attacker’s goal was to steal credentials and gain access to the recipient’s government employee accounts.
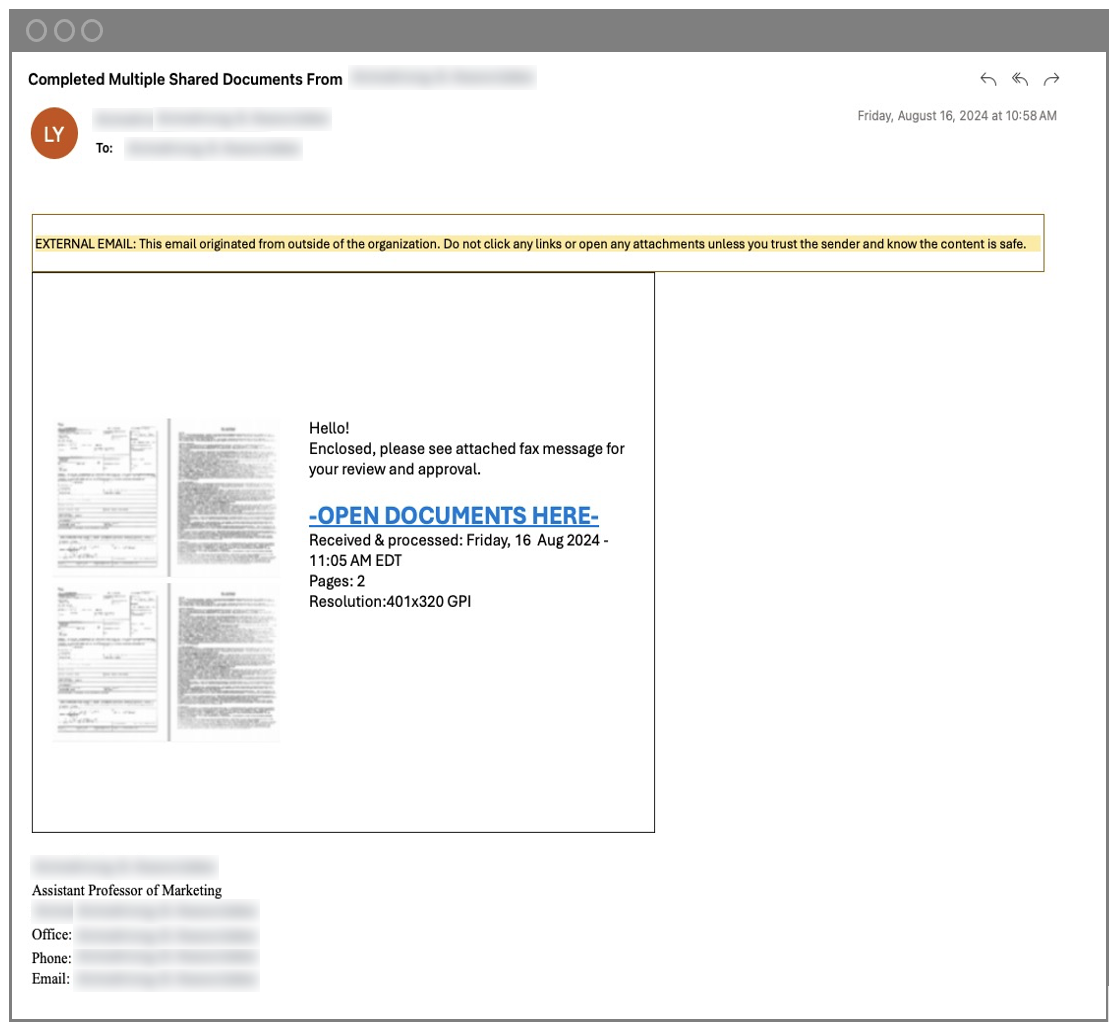
Phishing email received by the employee.
2. Taking the bait. If the employee had clicked on the malicious link in the message, they would have been taken to a hosted webpage that contained yet another link. At that point, they would have been asked to sign-in so that they could open the “full PDF document”. Once the sign-in was complete, the bad actor would have full access to the employee’s credentials, account and sensitive data.
Both malicious URLs impersonated trusted brands, including Microsoft, to convince the employee of their legitimacy.

Phishing website with disguised login request.
Detection: How did Proofpoint identify this attack?
Although the government agency had a security tool that was purportedly enhanced by AI, the phishing email slipped through and reached the intended inbox without being detected.
However, Proofpoint identified this email during the evaluation using Proofpoint Nexus, our end-to-end AI-driven detection stack. And because we identified it early, we were able to notify their security team to remove and remediate the threat.
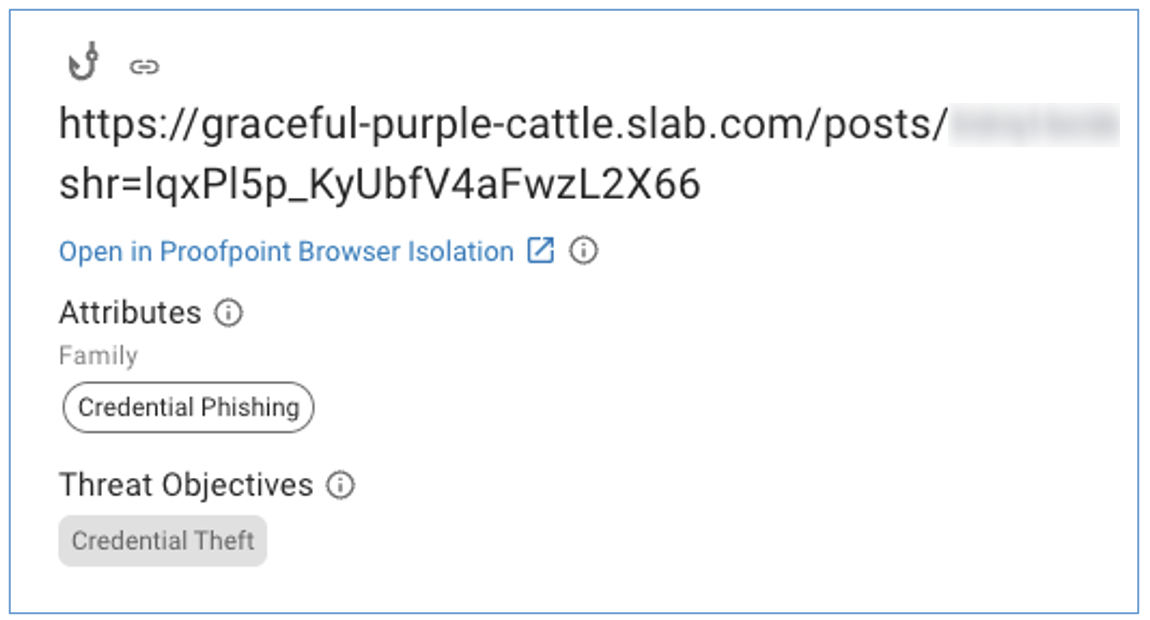
Attributions Proofpoint assigned to the condemned message.
Proofpoint Nexus algorithms combine a wide variety of signals and types of analysis to stop phishing threats. Because we rely on so many points of detection, Nexus has extremely high accuracy. Our false positive rate is very low – less than one false positive was reported in every 19 million messages. Our analysis offers the following pre-delivery capabilities:
- Behavioural detection for processing relationships and unusual sending patterns
- Semantic analysis for understanding the intent and context of typical conversations
- URL sandboxing to analyse links before the message is delivered
In this case, our pre-delivery URL detection was crucial in first identifying the phish. The sandboxing includes URL-to-URL (U2U) analysis to follow the malicious link in the email body through the additional link on the hosted webpage. Exclusive to Proofpoint, this pre-delivery capability stops messages from being delivered, so post-delivery analysis isn’t needed.
Below, you can see how Proofpoint sandboxing highlighted both the known file hosting domain as safe and the actual malicious page as phishing. Note that although these partners often shared documentation, Proofpoint was also able to detect that there was unusual sender behaviour in the recipients who were included in the Bcc.
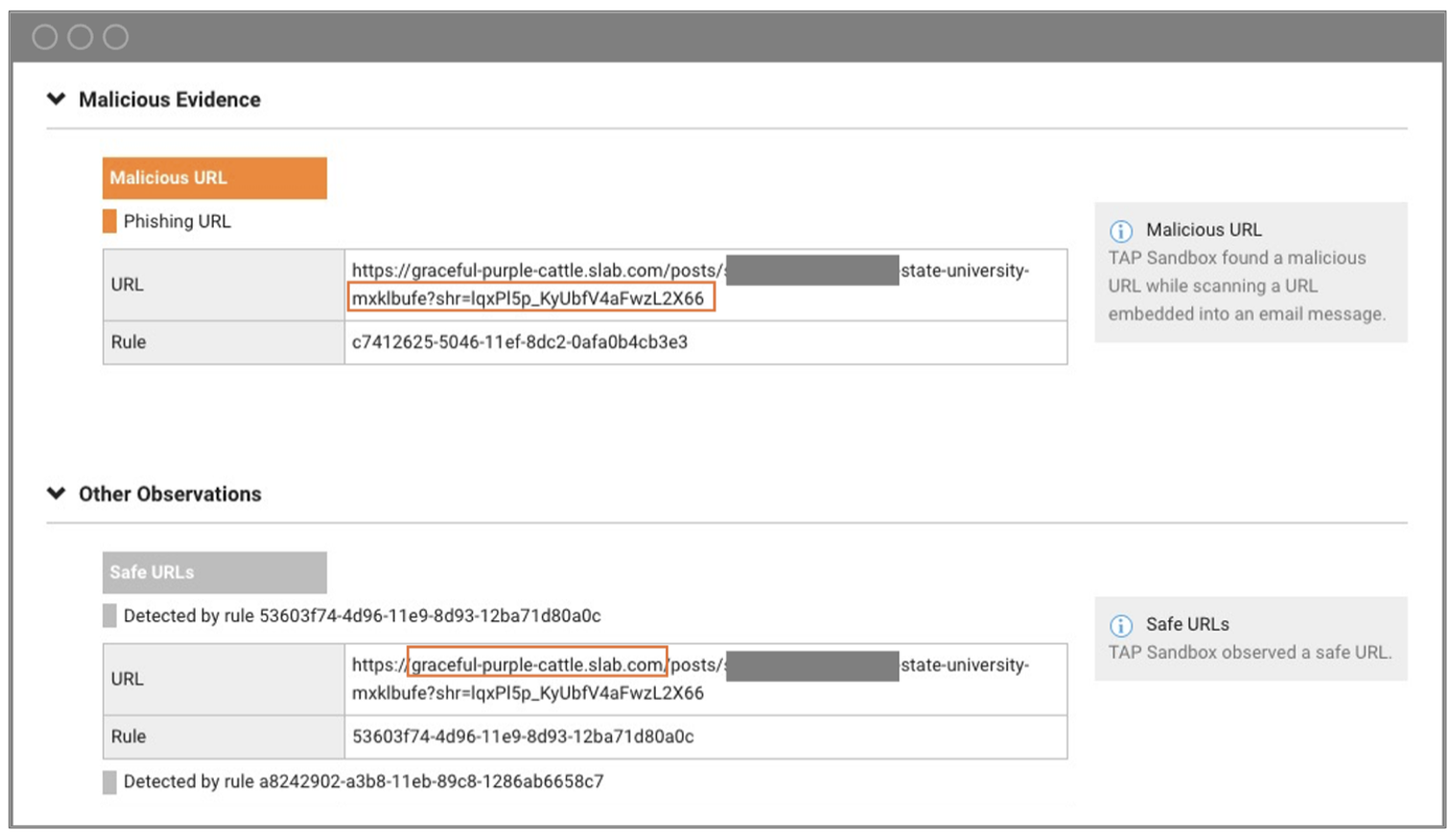
Condemnation summary of signals Proofpoint used to sandbox the malicious URL.
Remediation: What are the lessons learned?
To safeguard against phishing threats like the one described in this post, here’s what we recommend:
- Use pre-delivery URL analysis. Email clicks happen in the blink of an eye. According to Proofpoint research, 1 in 7 occurs in less than 60 seconds after message delivery. As phishing continues to evolve, security tools must look beyond reputation and thoroughly analyse suspicious links before they pose a risk in user’s inboxes.
- Keep your people informed. When phishing messages make it past security controls, employees, partners, and vendors are a vital defines. While you can’t control what happens in your supplier’s environment, it’s critical to train your own users to recognise and report phishing from trusted sources.
- Invest in additional supply chain protection. Vendor email accounts that are compromised are highly likely to be used in impersonation attacks. You can proactively identify these high-risk partners sooner with Proofpoint Supplier Threat Protection.
- Implement click-time protections. In this example, the target organisation used email warning tags which are important for notifying users of potential danger. Furthermore, having multi-factor authentication (MFA) in place is also a standard best practice, though not fool-proof. When bypassed, a good cloud security platform can identify account takeover (ATO) attempts and prevent unauthorised access and resulting data breaches.
Proofpoint delivers human-centric protection
In this complex credential phishing example, attackers tried to infiltrate a public sector agency and thereby gain access to its employee’s accounts and confidential data. If the attack had been successful, it could have resulted in a significant data breach, large financial losses, secondary compromised accounts and more. But Proofpoint human-centric security caught the threat and prevented any harm.
Using continuous end-to-end detection methods, Proofpoint protected this customer’s employees and enabled their security team to be more effective in their response efforts. This was only possible thanks to advanced tools like Proofpoint Nexus with behavioural AI and pre-delivery URL sandboxing which identified the attack early and kept their sensitive data secure.
Proofpoint methods go beyond native and API-based email security capabilities to prevent your people and your business from becoming a target. To learn how to stop vendor email compromise and advanced phishing attacks, download our Threat Protection solution brief today.
Read our Cybersecurity Stop of the Month series
To learn more about how Proofpoint stops advanced attacks, check out our previous blogs in this series:
- Uncovering BEC and supply chain attacks (June 2023)
- Defending against EvilProxy phishing and cloud account takeover (July 2023)
- Detecting and analysing a SocGholish Attack (August 2023)
- Preventing eSignature phishing (September 2023)
- QR code scams and phishing (October 2023)
- Telephone-oriented attack delivery sequence (November 2023)
- Using behavioural AI to squash payroll diversion (December 2023)
- Multi-factor authentication manipulation (January 2024)
- Preventing supply chain compromise (February 2024)
- Detecting multi-layered malicious QR code attacks (March 2024)
- Defeating malicious application creation attacks (April 2024)
- Stopping supply chain impersonation attacks (May 2024)
- CEO impersonation attacks (June 2024)
- DarkGate malware (July 2024)
- Credential Phishing Attack Targeting User Location Data (August 2024)
- Preventing Vendor Impersonation Scams (September 2024)
- SocGholish Haunts the Healthcare Industry (October 2024)

