The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals and how Proofpoint helps organisations better fortify their email defences to protect people against today’s emerging threats.
Phishing attacks surged significantly in 2024, increasing nearly 60% year-on-year. Experts have noted that not only are these attacks growing in volume, they’re also becoming more sophisticated. Shifts in the threat landscape—driven by advances in generative AI and evolving social engineering tactics—are enabling cybercriminals to conduct more personalised, sophisticated attacks that are increasingly difficult to detect.
Globally, an average of 4 billion phishing emails are sent per day. The increased success of these attacks has contributed to a high financial toll. By the end of the year, projected global costs could potentially reach $250 billion. Sectors like finance and insurance have been hit the hardest—experiencing over 27% of all phishing attacks—while technology, healthcare and education are also major targets.
Today, we’ll explore one type of phishing attack that is particularly hard to identify, which is called Dropbox phishing.
Background
During the past few years, Dropbox phishing scams have grown more sophisticated. Here’s how they typically work:
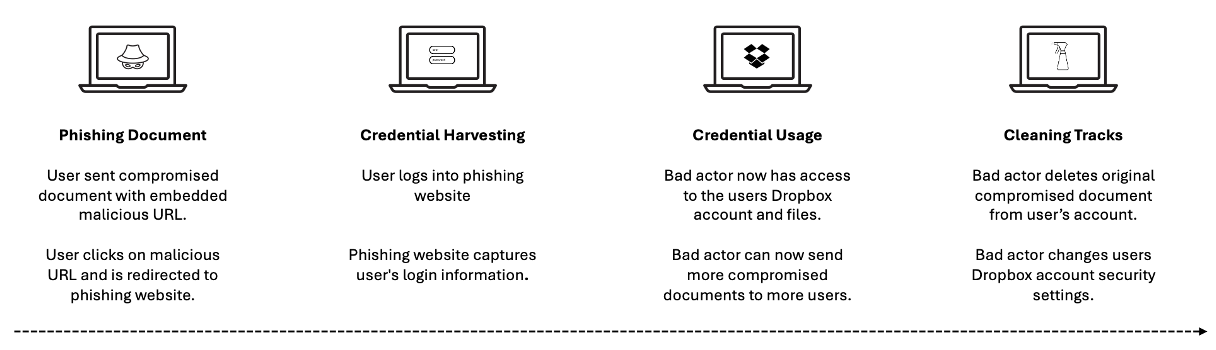
Steps in a Dropbox phishing scam.
Phishing attacks using legitimate Dropbox infrastructure are hard to identify for several reasons, including:
- Abuse of a legitimate service. A bad actor uploads a compromised document—like a PDF with an embedded malicious URL—and sends it directly through Dropbox. Because the threat is sent through a legitimate service, it can effectively bypass an organisation’s email security defences.
- Email pretexting. A malicious phishing email that initiates the attack can be very convincing. Bad actors often include realistic pretexts, such as ‘You’ve been invited to view a file’ or ‘A file was shared with you’, which closely mirror legitimate Dropbox notifications.
- Trust in the brand. Dropbox is widely trusted and frequently used for file sharing. If users regularly log into Dropbox to access shared files, they are less likely to scrutinise the login prompt, especially if they’re accustomed to receiving Dropbox file-sharing invitations.
This type of attack is very stealthy and highly evasive. Bad actors can launch and share any type of attack via Dropbox, including ransomware and malware.
The scenario
In this recent attack, a bad actor used legitimate Dropbox infrastructure to send a recipient a link to a malicious document that only they could access. The target organisation was a New England-based non-profit, which owns and operates upwards of 12,000 homes and 102 properties across 11 states.
The organisation’s incumbent email security was Microsoft 365 E3 plus an add-on API-based tool. Unfortunately, neither tool detected, blocked or remediated this advanced phishing attack, which left the organisation vulnerable to a potential cyberattack or data breach.
The threat: How did the attack happen?
Here is a closer look at how the attack unfolded:
1. Legitimate Dropbox message. A bad actor targeted employees with a shared PDF file, which could only be accessed by the recipients. The login message was genuine and was sent by the real Dropbox service.
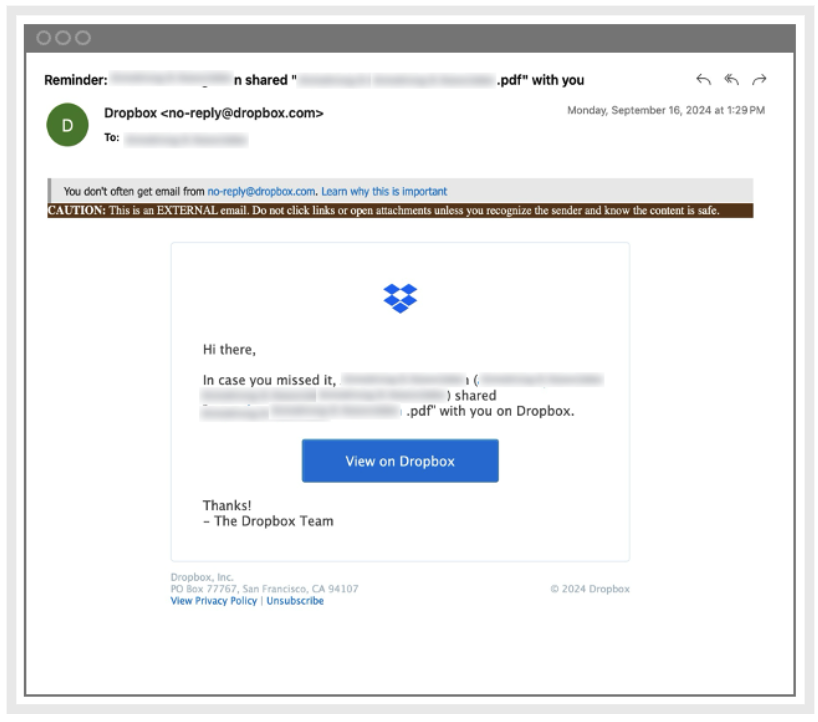
Legitimate Dropbox message received by the user.
2. Legitimate Dropbox login. To view the shared PDF file, employees needed to click on the ‘View in Dropbox’ button. If they had clicked on the link, they would have been prompted to log in and authenticate in the Dropbox service. Both the login screen and authentication messages were valid as they were sent from the real Dropbox service.
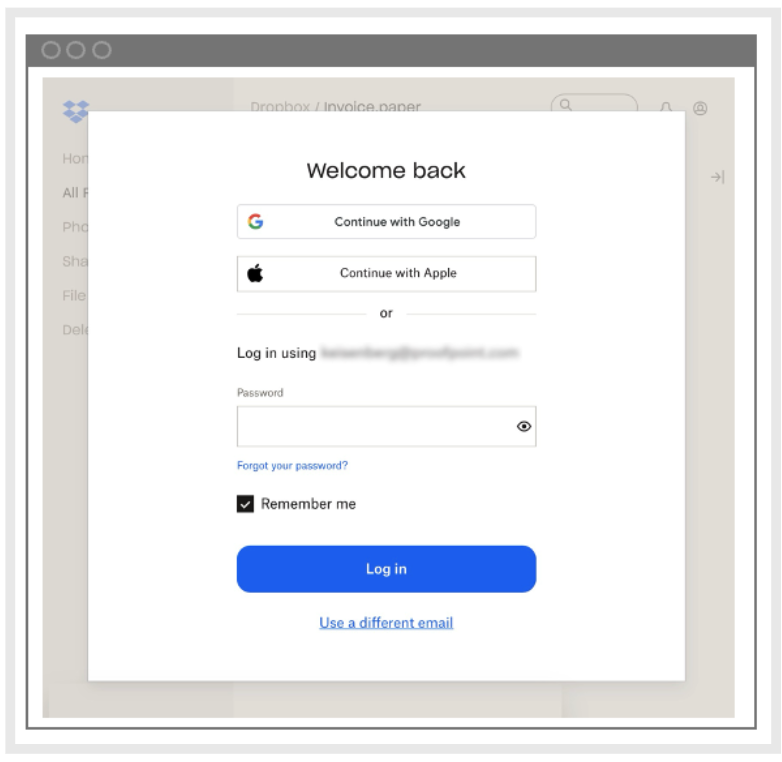
Legitimate Dropbox login page for accessing the shared file.
3. Dropbox phishing page. Once authenticated, users would have opened a shared PDF file with an embedded malicious URL. Clicking on the malicious URL would automatically have redirected them to a phishing page. At that point, they would have been prompted to log in and authenticate again. Unknown to the users, this site is controlled by the bad actor and is used to collect their login credentials.
The detection: How did Proofpoint identify this attack?
These multipronged Dropbox phishing attacks are hard to detect and almost impossible for users to spot these types of phishing email campaigns. Here’s why:
- Threats come from real senders with legitimate Dropbox accounts that have been compromised.
- Messages come from users that have an existing relationship with the recipient.
- URLs and templates from Dropbox are known, trusted and shared.
- The malicious URL that’s embedded in the shared document is masked behind Dropbox authentication.
Proofpoint has seen numerous Dropbox phishing attacks that have slipped past other email security tools. When Proofpoint detected and stopped this threat, we were doing a risk assessment with this customer, and our tool was deployed behind Microsoft and another API-only post-delivery tool. Notably, other organisations just like this one have reported that their API-only post-delivery tools have struggled to identify and stop these types of attacks.
Unlike the Proofpoint API-based solution, other API-based tools lack threat intelligence and URL sandboxing capabilities. Typically, they only scan for behavioural anomalies and not for malicious content. As a result, they fail to detect these highly evasive attacks that abuse legitimate cloud apps and compromised accounts. This gives security and IT teams a false sense of security that these threats will be identified. Even worse, they often incorrectly classify them as legitimate messages.
Proofpoint combines continuously evolving ML and behavioural AI techniques with threat intelligence and advanced sandboxing analysis to detect these types of sophisticated attacks. In this instance, we used a combination of behavioural signals within our sandbox, analysed message-level indicators and conducted malicious content analysis. By injecting the following signals into our URL sandbox, we detected and stopped this attack:
- Volume of messages shared by the same account
- Analysis of the sender plus the sender’s email address
- Presence of a Dropbox URL
- Advanced detection of abused URL sharing
- Enhanced document detection sent from many different URLs and different senders
- Analysis of message headers for malicious indicators, like reply-to mismatch
- Existence of other malicious messages with similar characteristics
Proofpoint detected and blocked this attack because we analysed the suspicious email with AI-driven behavioural indicators. And we scanned embedded URLs for malicious content. Ultimately, we provide security and IT teams with a much higher level of confidence in detecting and blocking these types of advanced email threats.
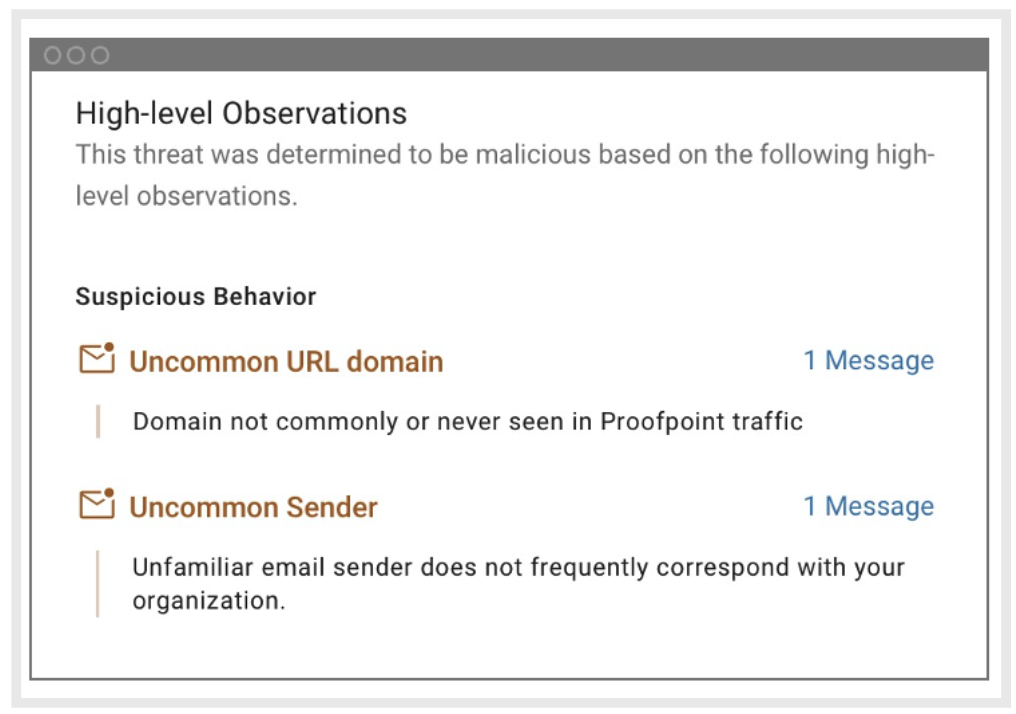
Condemnation summary of signals Proofpoint used to detect the threat.
The remediation: What are the lessons learned?
Here’s what we recommend to help protect against Dropbox phishing attacks:
- Analyse malicious URL content. Look for a solution that goes beyond simple scanning of suspicious messages and goes deeper to analyse malicious URL content. To do this right, it should support static and dynamic content analysis and machine learning (ML), as well as heuristics algorithms that are trained on data patterns from known malicious and benign URLs.
- Detect threats pre-delivery. According to Proofpoint research, 1 in 7 clicks on unsafe links occur within 60 seconds of an email’s delivery. Look for a solution that holds suspicious messages with URLs for sandbox analysis. It should use behavioural signals and threat intelligence to determine whether a message needs to be inspected further. This keeps users safe by blocking malicious messages before they are delivered.
- Keep your people informed. Training programmes can help users identify and respond to advanced phishing attempts. Educated users are less likely to fall for phishing scams. This means there’s less risk that their credentials—or your business—is compromised. Consider doing regular phishing simulations and providing users with feedback to improve their behaviour and awareness.
Proofpoint delivers human-centric protection
The surge in sophisticated phishing attacks is a stark reminder of how dynamic the threat landscape really is. That’s why you need to stay vigilant and take proactive steps to better protect your people and organisation.
Proofpoint provides a comprehensive solution that continuously detects and analyses known and emerging threats throughout the entire email delivery lifecycle. Unlike traditional email security products and API-only point tools, Proofpoint Threat Protection offers an AI-driven solution that detects 99.99% of threats from pre-delivery to post-delivery and at click-time. With Proofpoint, you can achieve end-to-end protection against threats before they reach users’ inboxes so you can better protect your people and business.
To learn more about how you can defend against evolving email threats, read our Threat Protection solution brief.
Read our Cybersecurity Stop of the Month series
To learn more about how Proofpoint stops advanced attacks, see our previous blogs in this series:
- Uncovering BEC and supply chain attacks (June 2023)
- Defending against EvilProxy phishing and cloud account takeover (July 2023)
- Detecting and analyzing a SocGholish Attack (August 2023)
- Preventing eSignature phishing (September 2023)
- QR code scams and phishing (October 2023)
- Telephone-oriented attack delivery sequence (November 2023)
- Using behavioral AI to squash payroll diversion (December 2023)
- Multifactor authentication manipulation (January 2024)
- Preventing supply chain compromise (February 2024)
- Detecting multilayered malicious QR code attacks (March 2024)
- Defeating malicious application creation attacks (April 2024)
- Stopping supply chain impersonation attacks (May 2024)
- CEO impersonation attacks (June 2024)
- DarkGate malware (July 2024)
- Credential Phishing Attack Targeting User Location Data (August 2024)
- Preventing Vendor Impersonation Scams (September 2024)
- SocGholish Haunts the Healthcare Industry (October 2024)
- Preventing Email Compromise in the Public Sector (November 2024)

